Hello George
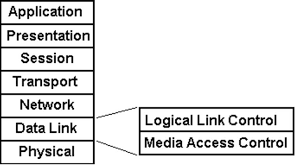
I believe that the word “skipped” is being used differently by Rene and differently by the author of the book you quote. When Rene made the statement, the meaning is that in any defined communication, such as that used by sending an Email, you can’t skip a layer on your way down. For example, using the TCP/IP model, the layers you would traverse when sending an email are:
- Application layer - SMTP
- Transport layer - TCP
- Network layer - IP
- Data Link layer - Ethernet
- Physical layer - Pulse Amplitude Modulation level 5 (PAM-5) encoding
As you send your data down the stack, you can’t simply skip the network layer. The communication would not be complete. There would be no IP addresses defined, and thus, devices down the line will not know what to do with the recieved packets. Do you agree? This is the meaning of Rene’s statement.
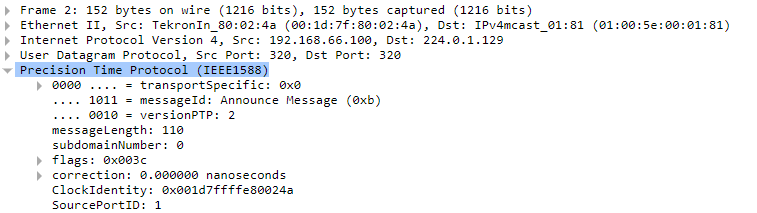
Now there are cases, as I mentinoed before, where the protocol being served functions on top of a particular layer, but does not go higher. That protocol is the top layer of that particular stack. This is the case in the example you state, where you say that PTP can function on top of the Data Link layer. In such a case the stack is like so:
- PTP
- Data Link layer
- Physical layer
Again, you can’t skip the Data Link layer to get to the physical layer, it just won’t work.
Now if we consider that the PTP protocol is on the application layer, then yes, the term “skip” can be used to say essentially that we skip the transport and network layers in the above example. I believe that is what the author intended. However, my opinion is that the word skip, in this case, is misleading. It can give the impression that layers are sometimes unnecessary.
I believe it is better to simply say that a particular protocol only uses the stack from the bottom, up to a particular layer. For example,
- the CDP protocol uses only the physical and data link layers
- the OSPF protocol (for exchange of routing information) uses only the physical, data link, and network layers
- the SMTP protocol uses all layers of the TCP/IP stack
Does that clarify the terminology a little more for you?
I hope this has been helpful!
Laz