This topic is to discuss the following lesson:
Hi Rene,
Thank you for the excellent intro on VPN. I like the way you teach and make the concept simple.
I also heard about other types of VPN like Easy VPN, Anyconnect VPN and many more. If you can throw some lights on that and let us know their use in real networks.
Hello Bharath
EasyVPN is a wizard that can be used either on the router (using Cisco Configuration Professional) or at the client to simplify the creation of VPNs. Using a wizard it allows you to enter information in a GUI to create your VPN. There are three components that can be used: Easy VPN Client, Remote and Server. You can find out more information about it here.
Cisco AnyConnect is a secure mobility client that allows you to connect securely (via VPN) to a VPN server. It is essentially Cisco’s VPN client software for PC, laptop and mobile devices.
So Easy VPN and AnyConnect are not really types of VPNs, but they are tools that leverage VPNs and simplify their deployment.
I hope this has been helpful!
Laz
Hi lazaros,
What is the difference between Tunnel, DMVPN and VPN?
Hello Muhammad
A VPN is a method by which you can establish a secure connection between two points over an inherently insecure network. For example, you may have a corporation headquarters and a branch office, and you create a connection between these two over the Internet. Now the Internet is considered an insecure environment, as you have no control over who can see the traffic that may be traversing any portion of the Internet. However, with a VPN, you can encrypt the data you send so that any intercepted packets will be unreadable and ultimately useless to any potential attacker. The packets, when they reach the branch office, will be decrypted such that they can be read and used. Only the destination device at the branch office is capable of successfully (and legally) decryption the data, thus ensuring security and confidentiality.
A tunnel in the context of communications is a construct that is used by VPNs and other technologies, to allow the movement of data from one private network to another, over a public network. Tunnelling involves repackaging or further encapsulating the data into a form that can be transmitted over the Internet, only to be unpackaged at its destination and sent to the private network. A tunnel will allow two private networks to “believe” that they are directly connected as they are oblivious to the mechanisms of the transmission over the Internet. Think of it as a ferry boat. You want to drive your truck with its contents from England to Ireland. There are road networks in England, and in Ireland, but not in between. You load your truck into the ferry boat which takes you from Liverpool to Dublin. You don’t care how you get there, nor are you concerned with the mechanisms involved in navigation, or even staying afloat. As far as you are concerned, you drove from the English road network into the ferryboat only to drive out onto the Irish road network to get to your destination. The communications tunnel is the ferry boat, which repackages your payload to be able to traverse the Irish Sea. Now VPNs use tunnels to get their job done, but tunnelling is only one aspect of VPNs. The other major aspect is encryption and security, something that tunnelling alone does not do.
Now Dynamic Multipoint VPN or DMVPN is a special type of VPN. A DMVPN is actually a routing technique that can be used to build a VPN network with multiple sites and allow routing to take place, all dynamically, without having to statically configure all devices. It is a technique that is especially popular among enterprises that have multiple sites and require secure communication between them. You can find out more about DMVPN at the following lesson:
I hope this has been helpful!
Laz
Thanks Lazaros,
Great and clear explanation as I expected.
We have a remote warehouse. We want to put a vpn router at the warehouse. I have a couple questions
Does the vpn router require a site to site connection, or can a different type of VPN be used.
Would the main office would be local and the warehouse considered the remote.
Hello Mark
It depends on what you want to achieve. Based on your description, it looks like you’ll need a site to site VPN connection. This requires that you have a VPN router at the main office to act as the VPN server, and a VPN router at the warehouse to act as the VPN client.
Alternatively, if you have only a few hosts at the warehouse, you could create a “client-to-site” VPN where each individual computer at the warehouse connects via a separate VPN connection to the VPN server at the main office. In this case, each VPN connection actually terminates on the user’s computer itself.
You can find out more about both of these VPN types in the Introduction to VPNs lesson.
Now such a VPN could be configured using either Cisco IOS routers or using an ASA firewall. You can find out additional information about both of these options at the following lessons:
I hope this has been helpful!
Laz
Hi @lagapidis
I’m a bit confused when it comes to the VPN I use such as ExpressVPN or any other similar type of application and the site-to-site and client-to-site VPN’s.
My understanding is that with something like ExpressVPN, my computer makes a connection to the ExpressVPN server and my public IP address is converted to theirs. Now is the process like this?:
if I go to google.com, the request will be sent from my computer, through my modem in a tunnel to the ExpressVPN server and the request for google.com will go from their server to google and back to ExpressVPN server and back to me. So, I’m assuming there is no tunnel between the server and google, but there is a tunnel between my computer and the VPN server. I’m not 100% on this. If I look at the “client-to-site VPN” diagram, would I be the client and ExpressVPN (or any other personal VPN) be considered the site?
I also noticed that the Cisco AnyConnect on my work computer does NOT change my public IP address, but gives me access to my companies files. So this I understand would be considered as a client-to-site VPN.
And if I understand correctly, a site-to-site VPN would be if I’m in a branch office connecting to files in my main office through something like Cisco AnyConnect.
My main interest involves the typical VPN applications that a regular user can purchase and where the tunneling processes involve in that.
Thank you!
Grant
Hello Grant
One of the things that can get confusing about VPNs is the terminology used. Services such as ExpressVPN call themselves VPNs services, and do indeed use VPN technology, but their primary purpose isn’t that for which VPNs have been originally created. This post describes this discrepancy in detail:
Now having said that, when you use a service such as ExpressVPN, what you are actually doing is something like this:
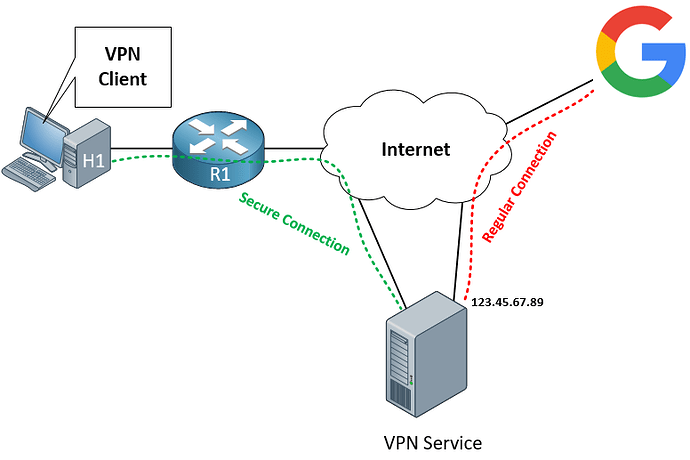
You are creating a secure VPN between your PC and the VPN service server. The server will then connect to Google using its own IP address. The result is that Google will only see the 123.45.67.89 IP address and not your actual address in all of your communication. Thus the primary (although not the only) purpose of such a VPN service is to hide your IP address.
Now this resembles a “client to site” VPN, but it isn’t really. The purpose of a client to site VPN is to provide access to internal corporate network services to a remote client. In other words, the client PC will gain a private internal IP address and will function as if it was physically connected to a switch on the premises of an enterprise network. This is not being achieved using the VPN service in the diagram above, since there is no “internal corporate network” here.
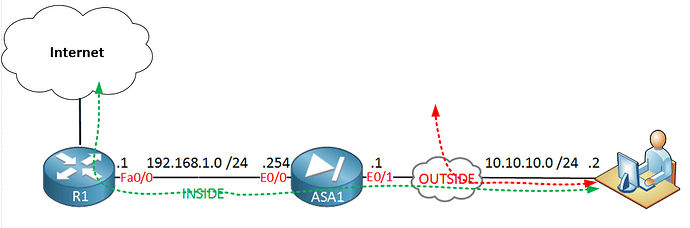
This is indeed a client to site VPN with the real meaning of the term. However, in such a setup, you can configure the client to connect to the Internet either through the VPN, or via its own Internet connection. Take a look at this diagram:
In this case, the client is connecting via AnyConnect to the ASA, but you can configure his Internet access to be gained either through the corporate internet connection (green dotted line) or you can employ what is known as split tunnelling, where internet connectivity is achieved via the client’s own Internet connection (red dotted line). In your case, split tunnelling is activated, and this is why Internet services see your real IP address and not that of your corporate network.
You can find out more about split tunnelling here:
I hope this has been helpful!
Laz
Hello René,
Could you please share sample configuration of route based IKEv2 tunnel config for IOS XE ?
Regards
Huseyin
Hello Huseyin
Currently, there is no lesson that covers that specific topology with those devices. However, you can find something similar at the following Cisco documentation, where one end of the link is a Cisco ASR and the other is an ASA:
Alternatively, you can take a look at this lesson, which shows the newer method that is being used in IOS XE which is the use of IPSec VTIs:
I hope this has been helpful!
Laz
Hello Lazaros;
thank you for your helps.
Regards
Huseyin