This topic is to discuss the following lesson:
Hi, I really enjoy the lessons.
I have two related questions, please.
In the lesson, you said
“The wireless client can use this to verify that it’s communicating with a legitimate AP.”
-
So that’s mean the attacker can’t make a certificate for its rogue AP? or it’s possible but difficult to make?
-
Who originate these certificates? is it the 802.11 standard or the Manufacture of the AP? In other words, where do these certificates come from?
I appreciate your effort.
Hello Ameen
Certificates are a widely used method for authentication in a very broad area of application. Some examples include:
A certificate, or digital certificate, or more correctly referred to as a public key certificate, is a method used to prove the ownership of a public key. A digital certificate includes information about the key, information about the identity of its owner, as well as the digital signature of the entity that has verified the certificate’s contents. This entity is known as the issuer. If the signature is valid, and the software examining the certificate trusts the issuer, then it can use that key to communicate securely with the certificate’s owner.
In this case, the wireless host examines the digital certificate of the AP, and if the signature is valid, it has been proven that the AP is indeed legitimate.
Now it is possible to issue your own certificate. This can be done as shown in the lessons I have linked above. However, the most secure way to validate digital certificates is to use a Certificate Authority (CA) as the issuer. This is an entity that issues digital certificates. The CA acts as a trusted 3rd party that is trusted by both the host and the AP.
Some examples of CAs include Amazon Web Services, Cloudflare, Google Cloud Platform, and others.
So to answer your questions directly, it is not possible for an attacker to make a “fake” certificate, especially if you use a 3rd party as the CA. The certificates can be made by you, or by the manufacturer of the AP, but such certificates can be compromised if the CA is not secure (i.e. an employee from the manufacturer leaked the certificate, or the certificate you created was somehow compromised). It is best to purchase such a service from a publicly trusted CA.
For more examples of how certificates are used, take a look at these NetworkLessons Notes:
https://notes.networklessons.com/why-do-we-trust-a-website-certificate
https://notes.networklessons.com/certificate-authority-structure
I hope this has been helpful!
Laz
Thanks a lot, Mr. Lazaros.
Guys, the lesson is great, but I would like to suggest two improvements:
1 - Add the “full wireless handshake”
In this image here, you share the phases “Authentication” and “Association”. But I think you should introduce the “Beacon” and “Probe” phases as well, and quickly introduce them, just like here. I’m following the CCNA 200-301 course and, at this point, beacon and probes were not introduced yet. Adding all the phases will make easier for the student to understand exactly where/when the authentication phase occurs.
2 - Improve wording
What happens when someone steals one of the wireless clients? That’s a problem because of two main reasons:
- The attacker has access to your pre-shared key and can now connect to the wireless network from any device.
- You need to configure a new pre-shared key on the AP and all wireless clients.
There are stronger authentication options where we ask users for a username and password instead. This helps. When a device is stolen, at least you can pinpoint which username was compromised and reset the password for that username. You don’t have to reset the pre-shared key and configure it on all wireless clients.
What about the AP? If you are at a hotel and see a wireless network with the name “guest,” you assume that this is the hotel’s wireless network. Anyone can configure an AP and use the SSID “guest,” though. How do you know that this is a legitimate AP, owned and operated by the hotel?
A wireless client saves a profile for all wireless networks it has connected to. When it sees the “guest” network again, it will attempt to authenticate and associate with it.
Some wireless attacks use a fake AP, called a rogue AP. The rogue AP acts just like a regular AP; it transmits beacons, answers probes, and associates clients. When a client associates with the rogue AP, the attacker sits in between the wireless and wired traffic and can intercept all traffic, just like the real AP.
To prevent this type of man-in-the-middle attack, the client should authenticate the AP before the client authenticates itself to the AP.
- In addition to the bullet point “The attacker has access to your pre-shared key and can now connect to the wireless network from any device”, I think you should add a new bullet point “Now it’s possible for the attacker to de-encrypt and then read traffic from other stations connected to the same AP”, just to make clear the limitations of this authentication method.
- When you say “To prevent this type of man-in-the-middle attack, the client should authenticate the AP before the client authenticates itself to the AP”, you do not make clear if this is valid for WPA Enterprise mode, WPA Personal mode or both.
- My understanding is that this is only valid for WPA Enterprise mode. For Personal mode, if the attacker somehow get access to the PSK and configure a fake/rogue AP with the same PSK, there is no much what the client can do. So for WPA Personal mode, it’s really necessary to protect the PSK, and in a hotel, is WPA PSK is used and the PSK is shared with everyone, someone creating a rogue AP is a real possibility/vulnerability to consider.
- If my understanding is correct, I would suggest you do edit the lesson to make clear that “server certificate validation” only applies to WPA Enterprise mode.
Hello Rarylson
Thanks for your feedback! I’ll let @ReneMolenaar know to take a look and consider your suggestions.
Laz
How would one setup up a self-signed certificate and use it to authenticate to a wireless network?
Hello Robert
You can find out more information about setting up authentication on a wireless network using self-signed certificates at the following Cisco documentation:
You will also be able to learn more about authentication methods PEAP and EAP-TLS which use certificates for authentication at the following lesson:
I hope this has been helpful!
Laz
Hello, everyone.
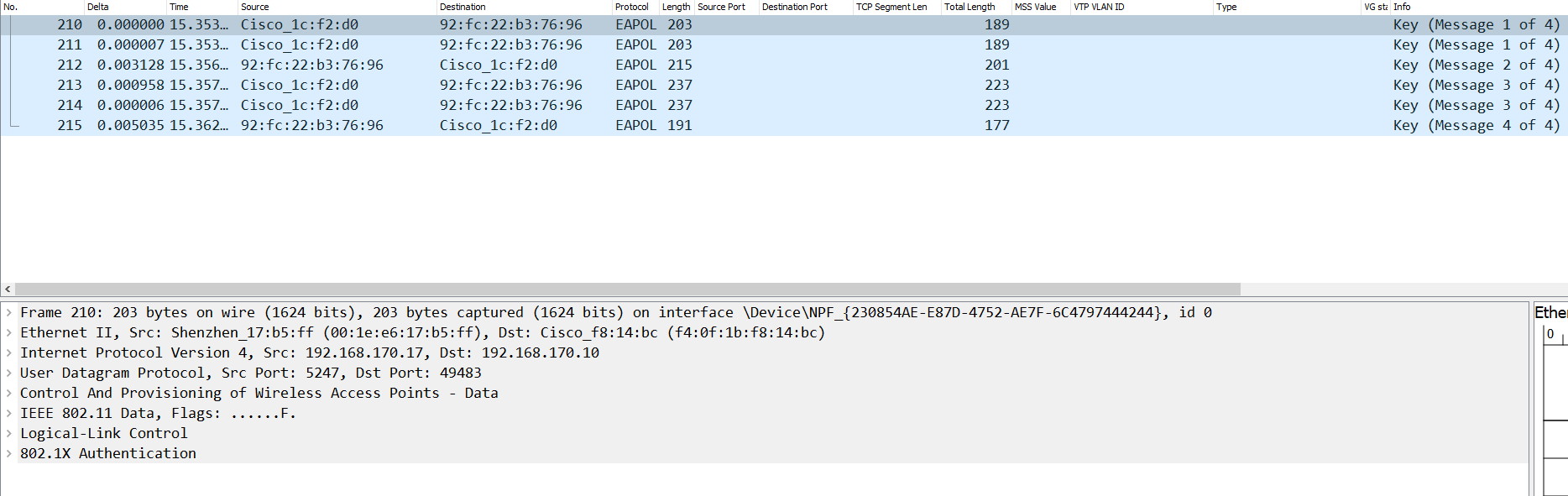
So EAP is used even if we’re not using WPA Enterprise? The 4-way handshake goes like this:
It’s using EAPOL to perform the authentication.
It’s just a little confusing considering that it says 802.1x at the bottom even though I am not using that.
My book says
So is EAP used or not?
The only thing that makes sense to me is that when we say that PSK authentication doesn’t use EAP, we mean that no EAP messages (challenges, requests, responses) are used for authentication.
But this doesn’t mean that EAPOL isn’t being used, right? So is it right to say that it’s a transport protocol that carries PSK-related information and in the case of WPA Enterprise, EAP messages?
Also, what exactly is the difference between EAP and EAPOL? This part confuses me a little
EAP is always carried by another protocol. To transport EAP messages, we need to encapsulate them. EAPOL (Extensible Authentication Protocol over Local Area Network) encapsulates EAP packets within Ethernet frames.
The messages themselves are a part of a certain protocol such as EAPOL? If so, are there any other protocols that can contain these EAP messages?
Thank you.
David
Hello David
EAP authentication itself is not used in WPA-Personal, as this mode relies on a shared password for authentication. However, EAPOL frames are still utilized in the 4-way handshake process for key derivation and mutual authentication, even in WPA-Personal. This explains why you see EAPOL as the protocol of those handshake messages in Wireshark.
The presence of “802.1X” in the Wireshark capture refers to the encapsulation standard (EAPOL), not necessarily 802.1X authentication. EAPOL is part of the 802.1X framework but can be used independently for key management. Wireshark simply interprets it as 802.1X.
EAP is indeed not used, but as you suggest, this doesn’t mean that EAPOL isn’t being used for the protocol of the handshake process.
EAP is a framework, not a full protocol itself. It defines how authentication messages are exchanged but doesn’t define exactly how they’re carried across the network.
EAPOL is one such carrier protocol. It specifically transports EAP messages over Ethernet (like in wired 802.1X).
There are other protocols that can carry EAP messages besides EAPOL. These include:
- PPP (Point-to-Point Protocol) — used in dial-up or VPN links. This is actually what EAP was originally designed for.
- IKEv2 (used in IPsec VPNs) can also carry EAP for user authentication.
- Diameter or RADIUS servers can carry EAP inside their own messages for backend authentication.
I hope this has been helpful!
Laz