This topic is to discuss the following lesson:
I configured the switch port for voice and data vlans. I was trying to use IP source guard for this port but it was failing. I can see the phone IP address in the DHCP binding table but the IP source guard was failing. I configured static binding for the IP phone and it was working.
Any suggestion to solve this issue without using the static binding ?
Hello Hind
In order for IP source guard to function with a voice VLAN, DHCP snooping must be enabled on that voice VLAN. Take a look at the following documentation from Cisco:
When you say IP Source Guard was failing, what do you mean exactly? If the issue was not DHCP snooping, please elaborate on the behaviour you are encountering and come back and let us know so we can continue troubleshooting.
I hope this has been helpful!
Laz
Does this work on GNS? I tried this on GNS3 with an IOU image, though the configuration was perfect, I couldn’t ping between clients.
Hello Dongsok
When some features tend to work on some platforms and not others, there may always be an issue with the IOS, the platform being used, or just the fact that GNS3 may not be able to accurately reproduce the features. It’s difficult to determine this, unless you have real devices on which you can configure these features. Hopefully, after reviewing your config as well, you’ll be able to determine the reason for the topology not functioning correctly.
I hope this has been helpful!
Laz
Hi Laz,
When the voip phone comes up it will boot as vlan 10 (data vlan). the port is configured to authenticate via ISE server. ISE will notice the mac address is for VOIP phone and will change the vlan from vlan 10 (data vlan) to vlan 20 (voice vlan).
VOIP phones configured to use dhcp to get the IP address. I am able to see the voip ip address in the dhcp sooping binding but the phone ip address is no longer pingable.
I think IP source guard feature blocking the VOIP phone as its using 2 vlans for same MAC address.
Any idea how to fix this issue ?
Hello Dongsok,
in GNS3 you can test IPSG only with checking IP address. It does not work while you wanna check the source MAC address.
I tested this with VIRL vios_l2-adventerprisek9-m.03.2017.qcow2 image.
Hello Michal,
Thank you, I’ll definitely try that out.
Laz, Thx for the comment and suggestion!
Hello Hind
When using ISE and voice and data VLANs on the same interface, there are some additional precautions that you should take. Specifically, these can be found at this Cisco Documentation.
Look especially at steps 5 through 7 in the procedure described.
To be honest, I haven’t configured voice and data VLANs along with authentication with ISE and IP source guard with an IP telephony implementation, but I’m hoping this may be helpful for you…
Laz
Hi,
I can’t understand it very well.
It works like a protection redundancy.
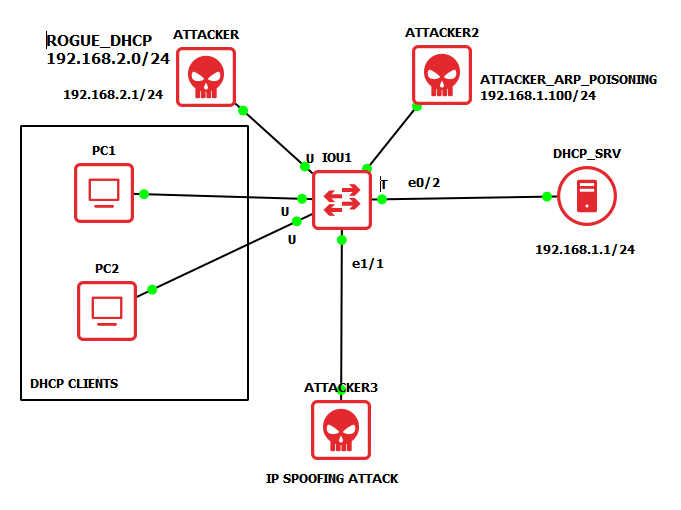
I’ve attacched a picture with a GNS3 topology, the attack (ip spoofing) from host ATTACKER3 will be mitigated by DAI configuration on SW1 because its ip not exist on ip snooping database, all this without any IPSG configuration.
Do I miss something?
Thanks
Hello Giovanni
It is important to understand the difference between DHCP snooping and IPSG. DHCP snooping can function alone while IPSG requires DHCP snooping to function. So it essentially adds an additional functionality to the whole operation.
Specifically, DHCP snooping allows DHCP Offer packets only on trusted ports and DHCP discover packets on both trusted and untrusted ports. In addition, DHCP discover packets, even though they are broadcast, will only be forwarded out of trusted ports.
IPSG adds an additional security feature. When it is enabled, all traffic is blocked on untrusted ports except for DHCP packets. Once a host gets an IP address through DHCP, only the IP address provided by the DHCP server to that port is permitted. What this means is you can’t statically assign an IP address to a device and plug it in to an untrusted port and obtain connectivity.
So IPSG mitigates IP spoofing. DAI on the other hand will mitigate ARP spoofing, and it won’t block an attacker’s device using its IP address.
In your scenario the attacker is mitigated because he is trying to impersonate another device with an unsolicited ARP reply. But what if he configured a static IP address (that was legitimate) and tried to gain access? Only IPSG can mitigate against that.
I hope this has been helpful!
Laz
Hi,
My 3560CG switch not provide the verify source command unless I enable the ip routing globally.
This is really needed to configure IPSG?
Thanks
Hello Giovanni
Hmm, that’s interesting. I tried logging in to a switch on VIRL and attempted to reproduce your results, but it seems that I am able to successfully issue the ip verify source command even if IP routing is disabled. Of course I am using the following vIOS version, so this may make a difference:
Cisco IOS Software, vios_l2 Software (vios_l2-ADVENTERPRISEK9-M), Version 15.2(CML_NIGHTLY_20180619)FLO_DSGS7, EARLY DEPLOYMENT DEVELOPMENT BUILD, synced to V152_6_0_81_E
It seems strange that IP routing is necessary for IPSG to function. I wouldn’t have thought that these features are connected. However, looking at the command reference for this feature for the 3750 (version 12.2(25)), it does state the following:
This command is available only if your switch is running the enhanced multilayer image (EMI).
This seems to indicate that Layer 3 functionality may be required for it to function, on the specific platform, with the specific version.
I know it doesn’t definitively answer your question, but it does give some indication of how it functions.
I hope this has been helpful!
Laz
Hi,
So i try to correlate switchport port security, dhcp snooping, DAI and IPSG , do you think my understanding below is correct?
port security: per port basis , when device connect to the port that has port security mac-address H.H.H enabled, it only check MAC address, doesn’t consider about the MAC-IP mapping
DHCP Snooping:per switch basis, main purpose is to drop malicious DHCP offer/ack packets. for devices that connect to the switch that has DHCP snooping enabled, it only obtain IP from the trust port that connects to the DHCP server
DAI: per switch basis, for devices that connect to the switch, switch check DHCP snooping DB and see whether the mac - ip mapping match the connected device IP/MAC, if it’s not matched, ARP reply will be dropped.
IPSG: per port basis, when device connect to the port, it check the DHCP snooping DB and see whether the source IP matches the entry in snooping DB on that interface. If not, drop.
if want to check source MAC along with source IP, it will need to combine IPSG + port security
Thank you very much for your time and help,
Hello Helen
It looks like your explanations are correct! Good job in understanding. These are all similar concepts and can be easily confused, but I think you have a good understanding of their differences and their uses.
Laz
Hey Laz, quick question. Can you use IP Source guard along with DAI?
Hello Gordon
Yes, you can use IP Source Guard (IPSG) alongside DAI, and this is something that Cisco considers best practice. These two features complement each other to provide layered security at different layers of the network stack.
IPSG operates at Layers 2 and 3. It prevents IP/MAC spoofing by validating the source IP and MAC address of incoming traffic against the DHCP snooping binding table or against static bindings.
DAI operates at Layer 2. It validates ARP packets to prevent ARP cache poisoning and spoofing and checks ARP requests/replies against the DHCP snooping binding table or static entries to ensure valid IP-to-MAC mappings.
Together, they mitigate common Layer 2/Layer 3 attacks in shared or untrusted environments. Both features depend on the DHCP snooping binding database for validation.
I hope this has been helpful!
Laz
Hey Guys,
Do I always apply the ip verify source command after I get a valid IP to populate the DHCP Snooping table. When I enabled it on the port prior, I kept failing to get an IP address on hosts so I had to turn it off then I could finally get an IP. Am I missing something?
Hello Gordon
Hmm, that’s interesting. IPSG should actually allow DHCP messages so that the host can obtain an IP address even with the ip verify source command applied. However, I suggest you check the following:
- IPSG depends on DHCP snooping to build the binding database. If snooping is not enabled, everything including DHCP messages may be blocked.
- Access ports must be untrusted (default), and uplink ports to the DHCP server must be trusted. If the switch’s uplink to the DHCP server isn’t trusted, DHCP Offers/ACKs coming back are dropped.
Check these out and take a look to see if this changes any behavior and let us know…
I hope this has been helpful!
Laz