This topic is to discuss the following lesson:
I think you are missing a keyword in this line:
<strong>permit host 2001:db8:0:12::1 any eq 23
Think it should be:
permit tcp host 2001:db8:0:12::1 any eq 23</strong>
Hi Jeppe,
For sure, not sure what went wrong there. Just fixed it…
Also added my configs at the bottom of the lesson.
Rene
Hi Rene
Will the 3 implicit permit/deny statements won’t show up when we use the show access-list statements?
Thanks
Palani
Palani,
That’s right–the 3 statements will not appear with a show access-list command.
Hi Rene,
I think telnet traffic filter in line vty NOT per interface ? correct me if I wrong.
Adding an access-list on the interface that blocks telnet traffic will work. Adding it on the VTY is easier if you want to block telnet traffic, no matter on what interface you receive it:
line vty 0 4
ipv6 access-class R1_TRAFFIC in
Thanks for answer,
I was in doubt so I did a test in a LAB
In the LAB I deny telnet connection instead of permit it and when I apply the access list on the interface the telnet connection is permitted and when apply it on the vty the telnet connection is denied, can you please test it and give me feedback ???
Hi @hussien.samer,
It’s working fine here:
R2(config)#ipv6 access-list R1_TRAFFIC
R2(config-ipv6-acl)#deny tcp any any eq telnet
R2(config-ipv6-acl)#permit any any
R2(config)#interface GigabitEthernet 2
R2(config-if)#ipv6 traffic-filter R1_TRAFFIC in
This blocks telnet traffic and permits everything else:
R1#telnet 2001:DB8:0:12::2
Trying 2001:DB8:0:12::2 ...
% Connection timed out; remote host not responding
R1#ping 2001:DB8:0:12::2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 2001:DB8:0:12::2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/2 ms
You can see the matches here:
R2#show access-lists
IPv6 access list R1_TRAFFIC
deny tcp any any eq telnet (8 matches) sequence 10
permit ipv6 any any (13 matches) sequence 20
Hi Rene,
when I tried it in my IOL with eve-ng it’s not working ?? weird thing
I tested this on Cisco VIRL. You might also want to try it on some real hardware…could be a IOL quirk ![]()
Maybe, in the end I wanted to know the correct behavior, thanks for your feedback.
Rene,
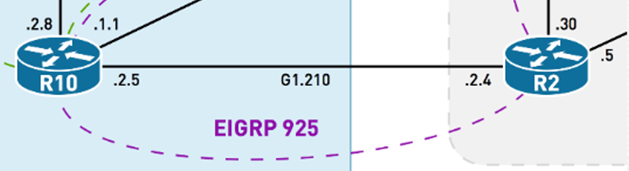
Having trouble understanding how an IPv6 ACL is used to permit & block EIGRP (88) Traffic…so I have two directly connected routers (IOSv) that have EIGRP Adjacency…when the following line is used:
!
ipv6 access-list default
permit 88 any any
control-plane host
!
EIGRP Control-Plane Traffic isn’t allowed but when I change it to:
!
ipv6 access-list default
no seq 10
seq 10 deny 88 any any
!
Adjacency comes back up…it has me confused due to the fact that I understand the rule is working vice-versa, whereas deny = permit & permit = deny…have you seen this before?
Hello Allen
Yes, that is counter-intuitive! Can you share with us a little more of your configuration? Can you include your topology, the application of the access list on the interface(s) as well as what seq 10 was originally?
Laz
Laz,
Sure…I think CoPP is my issue, doing a lab out of a Tshoot WB…I just need to understand why EIGRP Neighborship works when the deny is in place…attaching configs for both routers and the topology.
##################################
############R2####################
##################################
!
hostname R2
!
boot-start-marker
boot-end-marker
!
!
vrf definition CustA
rd 122.1.1.2:100
route-target export 100:100
route-target import 100:100
route-target import 200:200
!
address-family ipv4
export map vrfcusta
exit-address-family
!
address-family ipv6
exit-address-family
!
class-map match-all default
match access-group name default
!
policy-map default
class default
police 8000 conform-action drop exceed-action drop violate-action drop
!
interface GigabitEthernet0/0.210
encapsulation dot1Q 210
vrf forwarding CustA
ip address 10.245.2.4 255.255.255.254
ipv6 address 2001:10:245:2::4/127
!
router eigrp CustA
!
address-family ipv6 unicast vrf CustA autonomous-system 925
!
af-interface default
authentication mode hmac-sha-256 v6PASS!
exit-af-interface
!
topology base
exit-af-topology
exit-address-family
!
ipv6 access-list default
permit 88 any any
control-plane host
!
!
control-plane
service-policy input default
!
###############################
###########R10#################
###############################
!
interface GigabitEthernet0/0.210
encapsulation dot1Q 210
ip address 10.245.2.5 255.255.255.254
ipv6 address 2001:10:245:2::5/127
!
router eigrp XXX_DOT_COM
!
address-family ipv6 unicast autonomous-system 925
!
af-interface default
authentication mode hmac-sha-256 v6PASS!
exit-af-interface
!
topology base
exit-af-topology
exit-address-family
!
@ReneMolenaar can you help me understand why is it when a “deny” is in place the adjacency works?
Hello Allen,
The permit statement in your ACL defines what “hits” the control plane policer. In your case, you match EIGRP traffic so it gets policed.
The deny statement in the ACL means the control plane policer won’t touch it.
Rene
Hello
I need help. I’m trying to answer a question below:
“Which three elements can you use to identify an IPv6 packet via its header, in order to filter DoS attacks?”
Possible answers:
- Traffic Class
- Source address
- Flow label
- Hop limit
- Destination address
Anybody clarify me?
Thanks
Hello Boris
The question as it is stated is not very clear. After doing a search, I found that the question you stated is used as a summary. The specific question that is being asked is:
The enterprise network WAN link has been receiving several denial of service attacks from both IPv4 and IPv6 sources. Which three elements can you use to identify an IPv6 packet via its header, in order to filter future attacks? (Choose three.)
The question is specifically asking you to show how you would distinguish an IPv6 header from an IPv4 header. The answers are: Traffic Class, Flow Label, and Hop Limit as these headers are only found in IPv6 headers.
I hope this has been helpful!
Laz
Hello Laz,
Thank you for clear explanation.