This topic is to discuss the following lesson:
Quick question Rene, if you were to omit the IPv6 global unicast address on the tunnel interface, would you need to use “ipv6 enable” instead so OSPFv3 could use a link local address? Or does enabling OSPFv3 on the interface automatically generate a link local address?
Hi Chris,
You’ll need to configure an IPv6 address or use “ipv6 enable”. Without an address, you get an error:
R1(config)#interface GigabitEthernet 0/1
R1(config-if)#ipv6 ospf 1 area 0
% OSPFv3: IPV6 is not enabled on this interface
Rene
Hi Rene
I use virtual tunnel interface and i seem to work, it is correct ?
IPv4 Crypto ISAKMP SA
dst src state conn-id status
192.168.12.2 192.168.12.1 QM_IDLE 1002 ACTIVE
192.168.12.1 192.168.12.2 QM_IDLE 1001 ACTIVE
IPv6 Crypto ISAKMP SA
R1#sh crypto ipsec sa
interface: Tunnel0
Crypto map tag: Tunnel0-head-0, local addr 192.168.12.1
protected vrf: (none)
local ident (addr/mask/prot/port): (192.168.12.1/255.255.255.255/47/0)
remote ident (addr/mask/prot/port): (192.168.12.2/255.255.255.255/47/0)
current_peer 192.168.12.2 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 256, #pkts encrypt: 256, #pkts digest: 256
#pkts decaps: 245, #pkts decrypt: 245, #pkts verify: 245
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
Another question is how much mtu does IPsec Takes
Cordially
Hi Fabrice,
This is looking good, the number of packets encrypted/decrypted tells you your VPN is working.
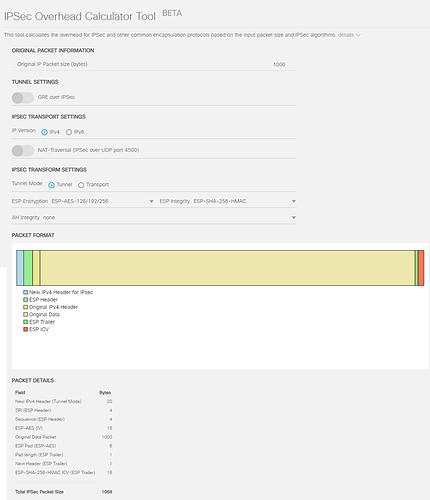
The overhead of IPSec depends whether you use AH, ESP, AH+ESP, tunnel or transport mode, and the algorithms you use. Cisco has a very nice calculator that shows you exactly how much overhead you’ll have. Here is a screenshot:
Rene