Hello Curtis
Thanks for the update. For your specific application of securing a single wireless link with IPSec, your implementation is just fine. Whether you use BVI/BVD or the method you describe, both are sufficient for what you need.
As far as your more general question, you are correct that a BVI can be used on a single router to bridge two local LAN interfaces, effectively turning that router into a switch for those two ports. For example, bridging GigabitEthernet0/1 and GigabitEthernet0/2.
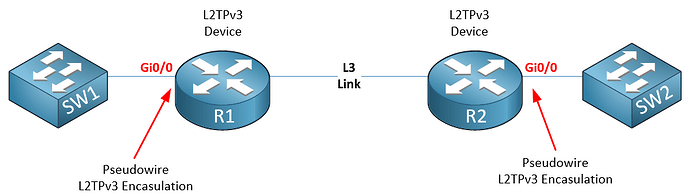
However, that is only its most basic application. The feature is used within ISPs and service provider networks, as well as in extremely large enterprise networks. Its primary power is to bridge a physical interface (like your LAN port) to a logical interface (like a Pseudowire).
Think of a Bridge Domain as a virtual Layer 2 switch inside the router. You can connect different types of interfaces to this virtual switch:
- Physical Ethernet ports (via a Service Instance)
- Pseudowires (like L2TPv3 or MPLS VPLS)
- Ether-over-GRE tunnels
When you do this, you create what is known as an “L2VPN” or a “Transparent LAN Service” (TLS). You are essentially “plugging” your local LAN into one port of this virtual switch, and “plugging” the long-haul L2TPv3 tunnel into another port. The router then simply switches frames between them.
So, to directly answer your question: No, the BVI/BDI model is not just for a single router. It is the foundational technology for building Layer 2 VPNs between two or more routers across a Layer 3 WAN, and is much more scalable.
So, both methods are valid for your point-to-point scenario, but they operate differently, and the BVI/BDI method is far more scalable and aligned with modern networking practices. It’s often called “Carrier Ethernet” or “E-LAN/E-LINE” services.
For your specific case however, it doesn’t sound like scalability is an issue, so either one is siutable for what you need.
I’m glad you interaction with the lessons and the forum has been beneficial for you! It’s beneficial for me as well, as lookin into these technologies helps me to learn as well!! I’m glad you feel you’re getting your money’s worth, that is very satisfying for us. Keep networking!
I hope this has been helpful!
Laz