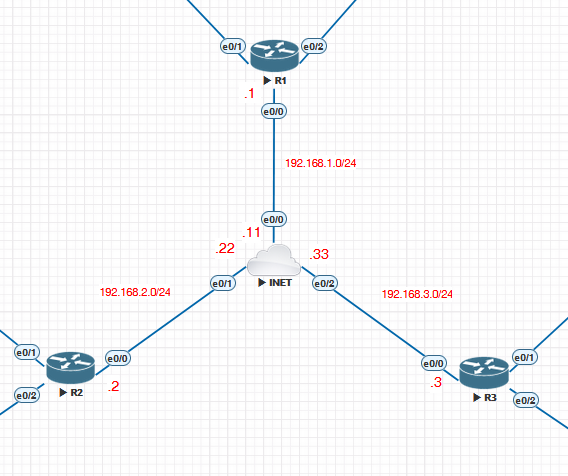
Hi,
Thank you for explaining how the MPLS over FlexVPN work.
I followed the steps and created a lab but the NHRP is not initiating and I couldn’t receive any routes from the spokes (I made some modifications in the ikev2 profile using the ip addresses instead of the fqdn). Following my config :
Hub:
vrf definition CUSTA
rd 1:1
!
address-family ipv4
route-target export 1:1
route-target import 1:1
exit-address-family
!
aaa new-model
aaa authorization network FLEXVPN_LOCAL local
!
crypto ikev2 authorization policy IKEV2_AUTHORIZATION
route set interface
crypto ikev2 keyring KEYRING
peer SPOKES
address 0.0.0.0 0.0.0.0
pre-shared-key local cisco123
pre-shared-key remote cisco123
!
crypto ikev2 profile IKEV2_PROFILE
match identity remote any
identity local address 192.168.1.1
authentication remote pre-share
authentication local pre-share
keyring local KEYRING
aaa authorization group psk list FLEXVPN_LOCAL IKEV2_AUTHORIZATION
virtual-template 1
crypto ipsec profile IPSEC_PROFILE
set ikev2-profile IKEV2_PROFILE
!
interface Loopback0
ip address 172.16.1.1 255.255.255.255
!
interface Ethernet0/0
ip address 192.168.1.1 255.255.255.0
duplex auto
!
interface Virtual-Template1 type tunnel
ip unnumbered Loopback0
ip nhrp network-id 1
ip nhrp redirect
mpls nhrp
tunnel protection ipsec profile IPSEC_PROFILE
!
router bgp 1
bgp router-id 172.16.1.1
bgp log-neighbor-changes
bgp listen range 172.16.1.0/24 peer-group FLEXVPN_SPOKES
neighbor FLEXVPN_SPOKES peer-group
neighbor FLEXVPN_SPOKES remote-as 1
neighbor FLEXVPN_SPOKES transport connection-mode passive
neighbor FLEXVPN_SPOKES update-source Loopback0
!
address-family ipv4
neighbor FLEXVPN_SPOKES activate
neighbor FLEXVPN_SPOKES send-community both
exit-address-family
!
address-family ipv4 vrf CUSTA
network 10.0.0.0
exit-address-family
!
ip route 192.168.2.0 255.255.255.0 192.168.1.11
ip route 192.168.3.0 255.255.255.0 192.168.1.11
ip route vrf CUSTA 10.0.0.0 255.0.0.0 Null0
Spoke:
vrf definition CUSTA
rd 1:1
!
address-family ipv4
route-target export 1:1
route-target import 1:1
exit-address-family
!
aaa new-model
aaa authorization network FLEXVPN_LOCAL local
!
crypto ikev2 authorization policy IKEV2_AUTHORIZATION
route set interface
crypto ikev2 keyring KEYRING
peer HUB
address 192.168.1.1
pre-shared-key local cisco123
pre-shared-key remote cisco123
!
peer SPOKE3
address 192.168.3.3
pre-shared-key local cisco123
pre-shared-key remote cisco123
!
crypto ikev2 profile IKEV2_PROFILE
match identity remote address 192.168.1.1 255.255.255.255
match identity remote address 192.168.3.3 255.255.255.255
identity local address 192.168.2.2
authentication remote pre-share
authentication local pre-share
keyring local KEYRING
aaa authorization group psk list FLEXVPN_LOCAL IKEV2_AUTHORIZATION
crypto ipsec profile IPSEC_PROFILE
set ikev2-profile IKEV2_PROFILE
!
interface Ethernet0/0
ip address 192.168.2.2 255.255.255.0
duplex auto
!
interface Ethernet0/1
vrf forwarding CUSTA
ip address 10.1.2.1 255.255.255.0
duplex auto
!
interface Virtual-Template1 type tunnel
ip unnumbered Loopback0
ip nhrp network-id 1
ip nhrp shortcut virtual-template 1
mpls nhrp
tunnel source Ethernet0/0
tunnel protection ipsec profile IPSEC_PROFILE
!
router bgp 1
bgp router-id 2.2.2.2
bgp log-neighbor-changes
neighbor 172.16.1.1 remote-as 1
neighbor 172.16.1.1 update-source Loopback0
!
address-family vpnv4
neighbor 172.16.1.1 activate
neighbor 172.16.1.1 send-community both
exit-address-family
!
address-family ipv4 vrf CUSTA
redistribute connected
exit-address-family
!
ip route 192.168.1.0 255.255.255.0 192.168.2.22
Thank you in advance for your comments.