This topic is to discuss the following lesson:
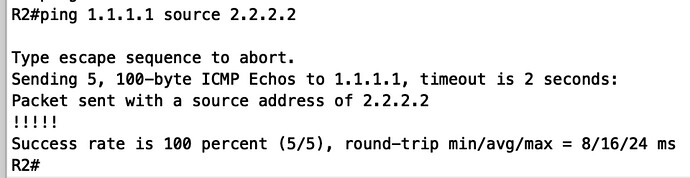
Why I can ping 1.1.1.1 source 2.2.2.2 even without virtual link, let alone the authentication? Is it the IOS bug or others?
Hello Rocky
I’ve recreated the topology with the appropriate configuration, but I was unable to reproduce your results. I found that the two routers did indeed become neighbors however, no routes were actually exchanged. The routing tables of both routers were empty.
Check your configuration again and verify that everything is indeed configured as in the topology.
I hope this has been helpful!
Laz
Thanks for your reply.
I will show my config as follows,
- IOS: c3725-adventerprisek9-mz.124-15.T14.image
- GNS3: 2.1.11
- My topology:
r1 config.txt (1.2 KB)
r2 config.txt (1.2 KB)
As you can see, I didn’t config virtual link. But I could
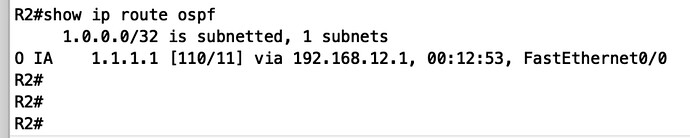
and its routing table is,
Look forward to your reply, thanks.
Hello Rocky
This is indeed puzzling. This may have to do with the fact that these are Loopback addresses that you are pinging and also because on R1, the router ID is explicitly defined as the same IP as the loopback and as the IP you’re pinging.
Now the fact that the routing table includes the 1.1.1.1 destination in its routing table makes sense, because it sees it in a neighboring area, which is what should happen. What shouldn’t happen however is for there to be L3 connectivity between the loopbacks.
However, notice that the routing table indicates that the route is to 1.1.1.1 and not to 1.1.1.0/24 which is the participating subnet, so it may have to do with how the loopbacks and the router IDs are handled.
Don’t get me wrong, connectivity should not be occurring, however, in order to see if we can get to the bottom of this, try the following:
- Change the router IDs of both routers to something completely different from the IP addresses of the loopbacks such as 10.10.10.10 so we can exclude the router IDs from the issue. See if connectivity still exists.
- Instead of creating loopbacks, configure some physical ports in area 0 on each router with IP addresses and have them participate in OSPF. See if you can ping between those.
- Connect external devices on the physical ports and attempt to ping between them.
Try these out and let us know your results.
I hope this has been helpful!
Laz
I believe there is another way of enabling authentication?
router ospf 1
area 1 virtual-link 2.2.2.2 authentication message-digest
area 1 virtual-link 2.2.2.2 message-digest-key 1 md5 NWL
Hello Chris
Yes you are right this too is a valid way to enable MD5 authentication over a virtual link. The difference here is that this configures message-digest just for the virtual link. Authentication in the area need not be globally configured. The configuration in Rene’s lesson, enables MD5 authentication on the whole of each area. Here is Rene’s configuration for comparison purposes.
R1(config)#router ospf 1
R1(config-router)#area 0 authentication
R1(config-router)#area 1 virtual-link 2.2.2.2 authentication-key NWL
I hope this has been helpful!
Laz
Hello,
I have noticed virtual link authentication does not impact the connectivity between the area 0 and area 2.. For example I have enabled virtual link authentication only on R1 and still i can see all the LSA on R1 and R3.. My routing table in both routers is fine..
Is there any explanation ..
Thanks
Hello Nabil
I assume you mean the connectivity between the two disjointed “area 0” regions…
Note that when you enable authentication, even if you do so on only one router, OSPF will continue to function until the OSPF process is reset. If it is not, then nothing will change yet. After resetting the OSPF process, the virtual link should fail, and you will see that the two area 0s will not create a neighbor adjacency.
I hope this has been helpful!
Laz
Hello,
I have noticed virtual link authentication does not impact the connectivity between the area 0 and area 2… For example I have enabled virtual link authentication only on R1 and still i can see all the LSA on R1 and R3… My routing table in both routers is fine…
Is there any explanation …
Thanks
Hello Nabil
This query has been resolved above:
Laz
Hiii rene,
in this lesson we learned virtual link authentication if Area 0 is discontinuous.
can u please explain how to configure Authentication for below virtual link.
R1–AREA0–R2—AREA1–R3—AREA2–R4
I created virtual link on R2 & R3 to reach R4.
thanks & regards,
Varma
Hello Varma
The virtual link authentication configuration works the same way when you have a discontiguous area 0 or when you have, like in your case, a non-backbone area that doesn’t connect to area 0. In your case, you want to connect area 0 with area 2. This means you would create a virtual link between R2 and R3 just as is the case in this lesson:
Once this virtual link is configured, you would then put in the same authentication commands in the OSPF configuration of R2 and R3. In other words, the confiruation would be something like this:
R2(config)#router ospf 1
R2(config-router)#area 0 authentication
R2(config-router)#area 1 virtual-link 3.3.3.3 authentication-key NWL
R3(config)#router ospf 1
R3(config-router)#area 0 authentication
R3(config-router)#area 1 virtual-link 2.2.2.2 authentication-key NWL
A more detailed explanation of this configuration can be found at the following Cisco documentation:
I hope this has been helpful!
Laz
Hii…
Can u explain Routemaps & Prefix lists. and difference between them.
or can u provide Good web link to understand them in plain english like our network lessons.
Hello Varma
You can find out about these topics at the following lessons:
I hope this has been helpful!
Laz