Hi Rene, staff and students,
well, …for me, private-vlan is not a concept as obvious as it seems
may i add some memo about private-vlan and could you agree or not ?
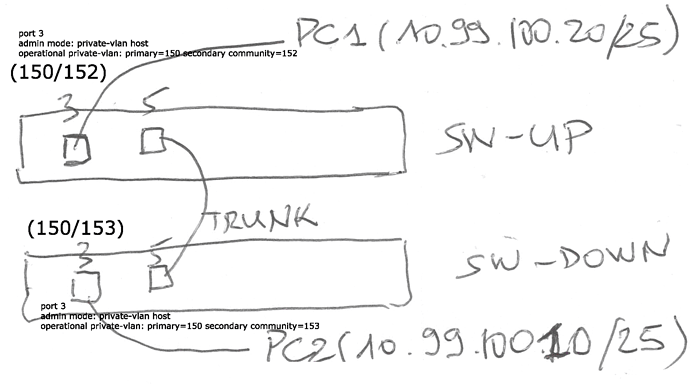
The main point to well understand is promiscuous ports
In my opinion, i noticed two cases for promiscuous ports:
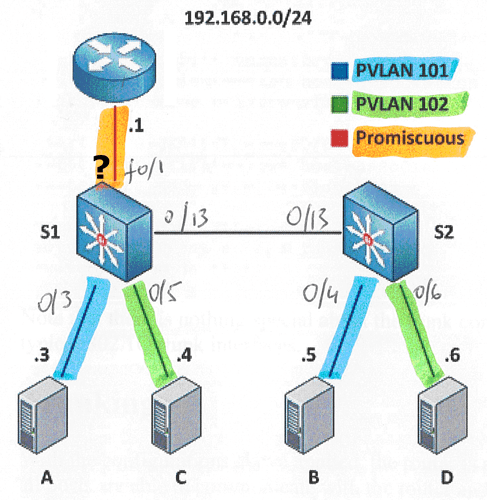
First case
In this case, there is one single IP subnet; the device plugged in the promiscuous port is a server or a router and the promiscuous port is used only to make communication between each secondary and the server or each secondary and the outside of vlan via the router
In this case the promiscuous port works “like access port”
The configuration is
S1(config)#int f0/1
S1(config-if)#switchport mode private-vlan promiscuous
S1(config-if)#switchport private-vlan mapping 100 101-102
You can set only a single primary vlan in the mapping (this is like access/edge port). In this case, secondary vlans are isolated at L2 and they cant communicate (never)
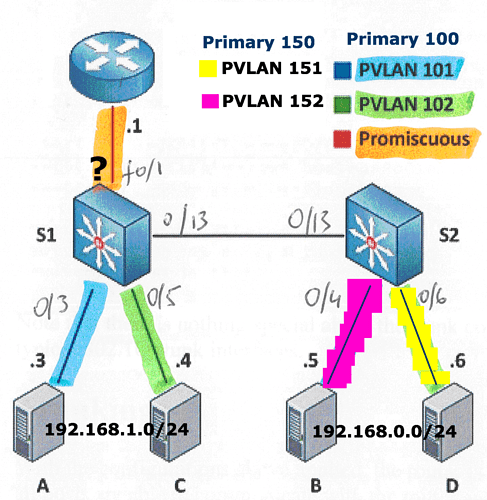
Second case
In this case, there are more than one IP subnet; the device plugged in the promiscuous port is a router and the promiscuous port is used to make communication between each secondary and outside of vlans,
but we want also to make inter primary vlan routing at L3
In this case the promiscuous port works “like trunk port”
The configuration is
S1(config)#int f0/1
S1(config-if)#switchport mode private-vlan trunk promiscuous
S1(config-if)#switchport private-vlan mapping trunk 100 101-102
S1(config-if)#switchport private-vlan mapping trunk 150 151-152
In contrary with case 1, you can set many primary vlan in the mapping (this is like trunk). In this case, secondary vlans are isolated at L2, but they can communicate via L3 routing
Infortunatly, you cant lab case 2 with 3750 but only with a few SW like 4500 (?)
I hope you will agree this memo, but if not, thank you for your answer that will help me (and perhaps others) to understand private-vlan concepts
Best regards