Makes sense, thank you! ![]()
Hi guys
Does the PVLAN a deprecated concept nowadays for the data center enviroment?
Does have any sense with the VXLANs ?
Thank you
Hello Giovanni
PVLANs are usually used at the access layer of a network, where end users connect to the network. Its primary usefulness comes from the fact that it allows you to block the communication between users on the same subnet without blocking their communication to vital services such as the default gateway, and particular servers. PVLANs are necessary in such an environment, because you don’t have directly control over what end users will actually attempt to do (such as set up an FTP file transfer between two employee computers for example.)
Datacenters are a more controlled environment, with a somewhat different addressing and connectivity structure so you don’t need the type of functionality that PVLANs offer.
VXLANs provide a different service than PVLANs. They are used to tunnel Layer 2 traffic over an IP (Layer 3) network. And yes, VXLANs do indeed address many of the requirements of Datacenters. You can find out more about VXLANs in the following lesson.
I hope this has been helpful!
Laz
HI there,
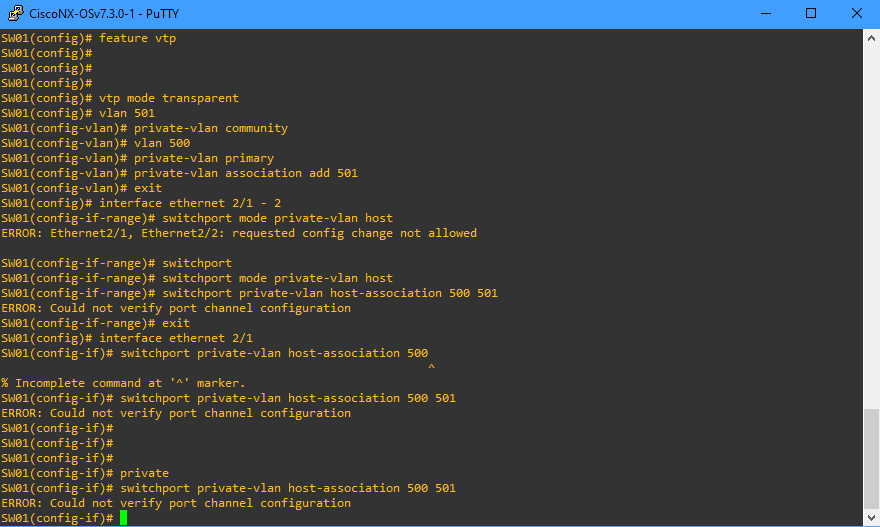
ive got a Problem. In my Hardware Lab I got 4 Catalyst 3550 and its not possible to configure PVLANs with it. SO i try Packet Tracer and there is the same i cannot configure PVLans with every switch which is to pick. After that i tried Nexus OSv 7.3, there i come to this step:
Can Someone help me ?!
Hello Jan
I’ve responded to this at the following post:
I hope this has been helpful!
Laz
Hi Lagapides,
yes that helps me. I thought its my foolishness yet. So but now i have the Problem that i think there are more Problems with GNS3 or my Hardwarelab or Packettracer and i cannot properly practice. Any ideas? VIRL is not an option because its to expensive for me.
Hello Jan
Specifically for the PVLANs, the only solution is VIRL or real equipment. For other concepts, many of them can be done with GNS3 or Packet tracer but not all. For GNS3, make sure you have the newest version. It may also be helpful, if you find you’re getting many errors or strange behaviour, to do a clean install to make sure that all of its components are up to date and working correctly together. It is quite a complicated setup, but they’ve done an excellent job in automating much of the installation process and documenting configuration procedures.
Otherwise, if you have one or two study buddies, you may be able to purchase VIRL together and share it. Other than that, the only other suggestion I have is to find some very cheap equipment on eBay. You may be able to do a combination of all of the above to get the cheapest combination for you.
Unfortunately, studying for these certifications does have some cost, in labs, software, equipment, study materials, and the exam itself. But believe me, it pays off and it is all worth it!!
I hope this has been helpful!
Laz
Hi,
i know that it will cost a little bit. Atm i will try my best with 4 catalyst 3550, GNS3 and Packet tracer. I hope i will come as far as possible with this.
Can you recommend Hardware for a Lab which is cheap ans i can use for all the topics ?
Hello Jan
The lesson below is a good starting point for getting information about some of the devices you may want to purchase. Typically, GNS3 should be enough for the routing part of CCNP level certifications, and for most of the CCIE. For switching features, it may be necessary to purchase some devices. To see which are the most appropriate, see the lesson below:
The switches mentioned there should be OK.
In order to save as much money as possible, I suggest you try everything out with GNS3. If something doesn’t work, say PVLANs for example, invest only in the equipment that you absolutely need. Remember, it is also possible to connect your real equipment to the virtual GNS3 equipment as well, making a topology made of both virtual and real devices. Here’s how you can do that:
I hope this has been helpful!
Laz
Hi Laz,
Can Private VLAN concept only be used if the VTP is configured in Transport mode on all switches?
Hello Pradyumna
Private VLANs cannot be used or shared using VTP. In order to implement private VLANs, all switches participating in private VLANs must be configured in transparent mode.
I hope this has been helpful!
Laz
Thanks Laz for clarifying this.
I have one more doubt, how to provide ip address and which Vlan we need to provide ip address , could you give an one example which include Vlan from basic configuration to division in to Private Vlans ?
Hello Pradyumna
Take a look at the lesson on Subnetting, as it describes in detail how to create an IP addressing scheme for various VLANs in an enterprise network.
As for private VLANs, remember, that all of the devices within the same primary VLAN will have the same subnet and the same default gateway. You can find out more about it at the following lesson:
I hope this has been helpful!
Laz
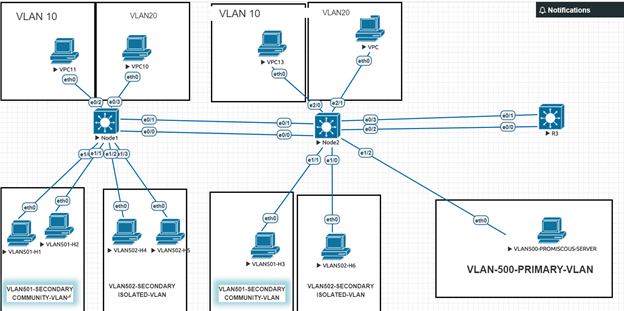
I have a guestion . I crated topoloji include 3 L3 switch , vlan 10,20 and Pvlan500, 501, 502 and SwI interface for vlan 10,20,500 in sw3 .Also there are erherchannels and trunks between switches . I can ping SVI interface and promiscous port of Pvan 500 from hosts in vlan 10,20,501,502, but I cant ping hosts in isolateted vlan 502 and comminity vlan 501 from vlan 10 and 20
Hello Tesla
What you describe is normal behaviour. The community VLAN is able to ping all hosts within the community VLAN and the promiscuous port (on VLAN 500 primary VLAN) while the hosts in the isolated VLAN can only ping the promiscuous port.
This also means that hosts in other VLANs such as VLANs 10 and 20 will not be able to ping hosts in the isolated and community VLANs.
I hope this has been helpful!
Laz
Hi laz ;
I understood that isalotaded ve comminty vlan cant access each other also normal vlan (not private ) cant acces these vlans. Normal vlans only access promiscous port .
thanks for your answer
Hello Tesla15
When creating a private VLAN arrangement on your switch, you must keep the following in mind:
- The promiscuous port, community VLAN ports and isolated VLAN ports all belong to the same primary VLAN. In the topology in the lesson, this is VLAN 500.
- Community VLAN hosts can communicate with the promiscuous port
- Isolated VLAN hosts can communicate with the promiscuous port
- Community VLAN hosts can communicate with other community VLAN hosts
- Community VLAN hosts cannot communicate with hosts in other community VLANs
- Community VLAN hosts cannot communicate with hosts in isolated VLANs
- Isolated VLAN hosts cannot communicate with hosts in any isolated or community VLAN.
Now normal VLANs are a configuration completely outside of this. If you have a normal VLAN, say VLAN 400 and add it to a port in the switch in the topology, of course, it will not be able to communicate with VLAN 500 or any of the private VLANs unless inter-VLAN routing is enabled. Remember that normal VLANs cannot communicate with each other unless you have routing.
Now, what happens if, in the lesson’s topology, we add an access port to the 500 VLAN simply as a normal port? How will it communicate with the other ports? Well, I labbed this up and I found that if you do so, the normal VLAN port will not communicate with any of the isolated, community or promiscuous ports. If you do this it is considered a misconfiguration. If VLANs 500, 501 and 502 are set up as VLANs of a private VLAN setup, then you should not configure any other ports using these VLAN IDs.
I hope this has been helpful!
Laz
Hi laz ;
I used intervlan routing on R3 also add 2 normal vlans (10 ,20 ) to lesson topology . I can access only gateway and promiscous port of vlan 500 (primary vlan ) but I can’t access hosts of isolated and cumminity vlans . İs it normal and not ?
I have known rules of private vlans . I only wonder between relationship of private and normal vlans .
Hello Tesla15
So far within the lesson, and in the posts above, we have only dealt with communication between hosts within the same primary VLAN. Specifically, communication between hosts on the same subnet. But you bring up a good point. In most cases, you would want these hosts to access resources on other networks as well, such as a corporate network and even the Internet. How do private networks behave when their hosts communicate with destinations outside of the primary VLAN?
Well, in order to achieve this, you first must create an SVI for the primary VLAN. This will act as a default gateway for all hosts, whether in a community or an isolated VLAN. You must also configure the hosts to use the IP address of this SVI as the default gateway.
At this point, hosts will not yet be able to reach this SVI as the default gateway. Using the example in the lesson, only hosts on VLAN 500 that are not assigned to any secondary VLAN will be able to access other networks. You need one more command that will map the secondary VLANs to the primary SVI. Specifically:
S1(config)# interface vlan500
S1(config-if)# private-vlan mapping 501-502
This command tells the SVI that these two secondary VLANs belong to the primary VLAN of 500. Once this is complete, all hosts, within community and isolated VLANs will be able to communicate with resources outside of their subnet.
Remember that the purpose of private VLANs is to restrict communication between hosts within the same VLAN. For the restriction of traffic between subnets, access lists are the most suitable solution.
I hope this has been helpful!
Laz
Hello Laz,
your answer is awesome and really easy to understand. Thanks a lot.
but ı wonder if ıuse router instead of L3 switch, How ı can write that commands.