This topic is to discuss the following lesson:
protected port on steroids ![]()
I also enjoyed the term ![]()
Hi Reno,
Very Simple and Great explanation !
Regards,
Srini
lol freedom fighter.
lol protected port on steroids.
LOL! haha
Hello Rene,
Is the Protected option is available in Switch types like 2960 , 3560 ? if yes, i try to applied it on packet tracer which support both switch but it said not supported. Would you please let me know which switch is supported. Thank you
Hi Sinan,
Yes it’s available on the 2960 and 3560. I’m guessing that packet tracer doesn’t support it, it’s a simulator after all.
Rene
Hlw Rene,
this is good stuff, thanks. One questions …
Protected port feature will work within SW local port & within Same VALN , right ??
br//
zaman
Hi Zaman,
That’s right. It will work for the VLAN that the interface is assigned to.
Rene
Hello Rene/ Laz,
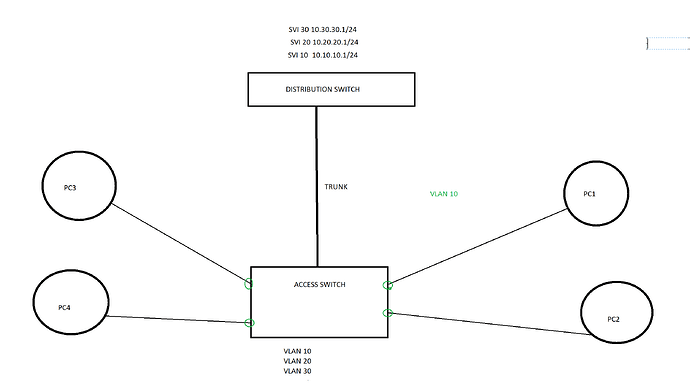
I have a question and I am going to use the below topology as a reference for the question.
As you see in the diagram, all the PCs are in VLAN 10. The access switch is hosting other VLANs as well. All the SVIs are located in the Distribution switch as you see in the diagram. The link between access switch and the distribution switch is a Trunk link to carry multiple VLANs.
Now my requirement is to block access for PC3 and PC4 so they can not go out of local network. If PC3 and PC4 can not talk to each other, that is ok. They are only allowed to talk to the devices in the local network(VLAN 10). I am thinking to configure PC3, PC4 and the Trunk port on the access switch as Protected port. I am not quite sure how protected port works on a trunk port. I am expecting that PC3 and PC4 will not able to get to the gateway and therefore, they will not be able to go out of the local network. I am also expecting all other devices to have normal functionality. Please clarify this.
Thank you in advance.
Azm
Hello Azm,
If you want to restrict PC3 and PC4 but not PC1 and PC2 then I would probably just create a new VLAN, let’s say VLAN 11. Add PC3 and PC4 to VLAN 11.
You can either create VLAN 11 without an SVI so there is no gateway or create an SVI and add an access-list to define to which other subnets they can go or not.
Rene
Hi Laz,
As per topology related to Hacker, I want to know in this hacker is still able to reach our router then how could it be protected instead using port and mac security?
Hello Pradyumna
Yes, you are correct that in the specific scenario, the hacker will have access to the router, and if they were able to hack the webserver, they may be able to compromise the router as well.
However, the point of the protected port is to disable any host to host communication within a subnet. Everyone must have access to the router to exit the subnet, but you don’t need access to other hosts in order to have network access. This not only protects other servers on your network from a compromised server, but it also helps protect you from malicious users on your own subnet. The hacker may not be someone that remotely attacked a system on your network, but it might be a fellow employee on your corporate network as well.
You are correct that port security is a more complete and comprehensive solution for securely administrating network access privileges within a network. Another similar feature is also private VLANs.
I hope this has been helpful!
Laz
but laz still any one of the server has a possibility of being hacked by any company user so in that case we have to use port security for all users but then they will not be access any server if we do like this.
Hello Pradyumna
The best security you can have is simply disconnecting your sever completely from the network. That way no one can access it, and it is 100% safe. But as you know very well, this is not an option, because servers are made for clients to connect to them.
Theoretically, if clients have access to a server, they can potentially hack it. But you can’t use this as a principle of security because you defeat the purpose of the network.
For this reason, security features are employed to minimize the possibility of security breaches. Port security as well as protected ports are some features that you can use to limit access, and thus mitigate hacking. You, however, as a networking professional, must decide which solution is best for your situation. These features, along with additional security features used by the server in question should work together to provide a more complete and more secure environment for network services to be deployed.
I hope this has been helpful!
Laz
Hi Team ,
As mentioned below in the lesson
’ Protected ports are unable to communicate with each other. It might also be a good idea to protect your servers with protected ports:’ - In this case we will not have any user in the VLAN able to connect to connect any servers on the same VLAN if user machines are protected & also the servers
Regards
Shaan
Hello Mohammed
Yes, you are correct, if you have your servers on protected ports, any hosts connected to protected ports as well will not be able to contact the servers. For this reason, you should either apply the protected ports to your hosts OR to your servers, not both.
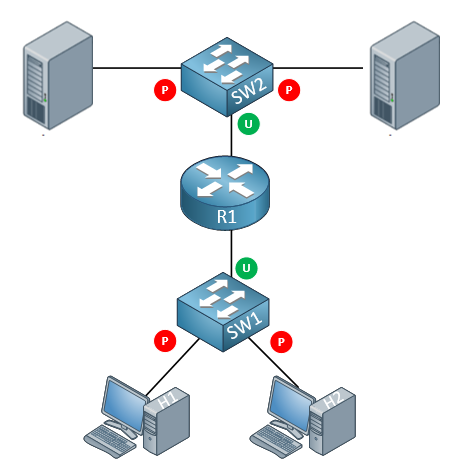
Now all of the above suggests that both servers and hosts are on the same VLAN/subnet. Remember that protected ports are Layer 2 features, and are not affected by protected port configurations in other VLANs. In any VLAN, the default gateway should be connected to an unprotected port, so that any hosts or servers on protected ports will be able to communicate with other subnets via routing, without any problems. For example, take a look at the following diagram:
Note that even though both hosts are on protected ports, and so are both servers, each host can communicate with each of the servers, via the unprotected ports connected to the router. In this scenario the two hosts cannot communicate, nor can the two servers between them. Note also that the hosts are on the same VLAN/subnet with each other, and the servers are also on the same VLAN/subnet with each other.
I hope this has been helpful!
Laz
Hi Laz ,
So if i am not wrong anything connected on Unprotected port will not be able to communicate with something on a Protected Port ?
Regards
Ziad
Hello Mohammed
Communication between two protected ports on the same VLAN is blocked. All other communication is not. So, communication between a protected port and an unprotected port is not blocked.
Take a look at this NetworkLessons Note on protected ports for more detailed information.
I hope this has been helpful!
Laz
Hello,
Thank you for another excellent article!!!
The article made me wonder about further real-world applications of this feature.
Is it best practice to configure all interfaces that connect to end users as protected ports?
In fact, in an enterprise environment, isn’t it a good idea to configure almost all interfaces in all VLANs as protected ports? The one exception would be the port that connects to the default gateway (doing so would certainly isolate the end user devices from the network, if they are all connected to the same switch). In a real world enterprise environment, if the devices in their VLANs shouldn’t communicate with each other directly anyway, then why not do so? Shouldn’t all communication be taking place between the default gateway and the end user devices anyway?
Of course, in a data center employing a spine-leaf topology, this would make no sense.
Isn’t it the case that protected ports in the same VLAN can communicate if they are on different switches? What if the separate physical switches are configured as one logical switch, for example using VSS?
Thank you.
Attila