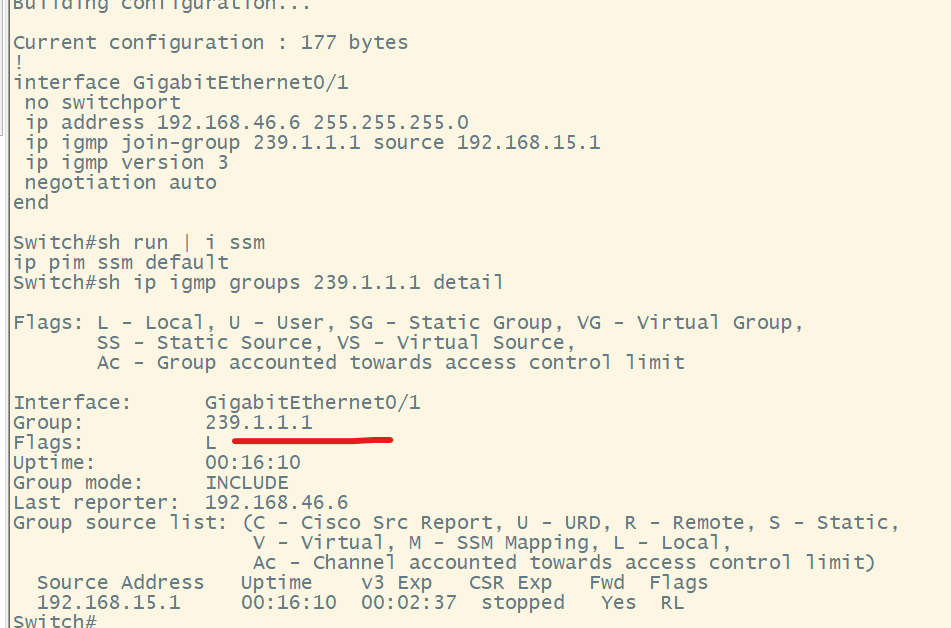
Hi,
I set up a lab and found that the router interfaces on which I ran the join command (to simulate a host, like in your example) didn’t actually need to have IGMP v3 configured.
(R5)-----Gi0/1.58--------(R8)--------Gi0/1.108-------(R10)
Joining the group:
R10(config)#int Gi0/1.108
R10(config-subif)#ip igmp join-group 232.1.1.1 source 150.1.9.9
Verifying IGMP version on the interface:
R10# sh ip igmp inter
GigabitEthernet0/1.108 is up, line protocol is up
Internet address is 155.1.108.10/24
IGMP is enabled on interface
Current IGMP host version is 2
Current IGMP router version is 2
Confirming the interface has joined the group:
R10#sh ip igmp groups
IGMP Connected Group Membership
Group Address Interface Uptime Expires Last Reporter Group Accounted
232.1.1.1 GigabitEthernet0/1.108 00:28:09 stopped 155.1.108.10
Upstream router R8’s mroute table:
R8:
(150.1.9.9, 232.1.1.1), 00:23:05/00:03:02, flags: sT
Incoming interface: GigabitEthernet0/1.58, RPF nbr 155.1.58.5
Outgoing interface list:
GigabitEthernet0/1.108, Forward/Sparse, 00:23:05/00:03:02
In fact, even if I try to join a group without specifying a source, it complains, despite that interface still being v2:
R10(config-subif)#ip igmp join-group 232.1.1.1
Ignoring request to join group 232.1.1.1, SSM group without source specified
I can a ping from the source to 232.1.1.1 and that interface was responding:
R9#ping 232.1.1.1 repeat 1000 source Lo0
Type escape sequence to abort.
Sending 1000, 100-byte ICMP Echos to 232.1.1.1, timeout is 2 seconds:
Packet sent with a source address of 150.1.9.9
Reply to request 0 from 155.1.108.10, 16 ms
Reply to request 1 from 155.1.108.10, 13 ms
Could it be working because the router itself is running multicast and as a result not actually truly representing a host receiver? That’s the only thing I can conclude.
And by the way, for the sh ip igmp interfaces output, what is the difference between IGMP host version and router version?
Thanks,
Sam