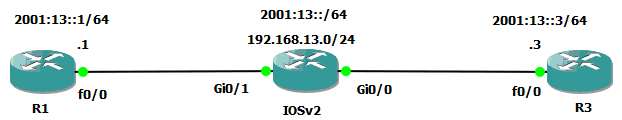
This topic is to discuss the following lesson:
Hi all, I labbed up transparent bridging. R1 is able to ping R3 etc and everything seems to be working, however, when i apply the access-list to the interface fa 0/1 of R2, it seems like it never gets a hit. Traffic continues to flow, there’s no dropping of traffic. any idea why???
so from what i can tell, when the traffic comes back from R3, R2 only looks at the layer 2 information. Since R2 knows the frame is destined for the mac address it switches the frame at layer2. In other words, the ACL is never checked. So how rene did this lab is a mystery to me..
I’m doing the lab in gns3 using Cisco IOS Software, 3700 Software (C3725-ADVENTERPRISEK9-M), Version 12.4(25)
Hello Kam
Pinging from R1 to R3 will work whether you have the access list applied to Fa0/1 or not, as the access list will allow traffic from R1 to R3 as well as responding traffic. Try pinging from R3 to R1 to see if the access list is blocking.
Now it is true that the access list is applied to a layer 2 interface, however, access lists that are configured to inspect tcp, udp and icmp as is the case here will also check higher level protocols to determine if a frame can be forwarded or should be dropped.
Let us know of your results and if need be, we can help you further…
I hope this has been helpful!
Laz
Hi Lagapides
According wording “This means that R1 and R3 will be in the same layer 2 domain.” , it mean if Braodcast strom happen from R1 then it effect with R3 right ?
If Yes, How we limited Broadcast storm ?.
We can configuration STORM CONTROLL BROADCAST LEVEL AS CISCO SWITCH ?
Hello Vittawat
Yes that is correct. In the specific topology, R2 would essentially function as a switch so any broadcasts sent on Fa0/0 of R1 would reach the Fa0/0 interface of R3.
Now as for your question about limiting broadcast storms, for a topology similar to that in the lesson, a broadcast storm would not be a possibility. This is because there are only two hosts in the link, R1 and R3. A broadcast storm is a concern only when there are tens or even hundreds of devices within the same broadcast domain. Typically when you configure a router to function as a layer two bridge, you wouldn’t connect it to a LAN with many devices, but it would most likely be a point to point connection, so no storm control configurations need be implemented.
I hope this has been helpful!
Laz
Hi aujla3,
I lab it up & I too notice access list R3-TO-R1 is not hit. CBAC also shows no traffic.
On R2:
interface FastEthernet0/0
no ip address
ip inspect CBAC in
interface FastEthernet0/1
no ip address
ip access-group R3-TO-R1 in
ip access-list extended R3-TO-R1
deny ip any any
ip inspect name CBAC tcp
ip inspect name CBAC udp
ip inspect name CBAC icmp
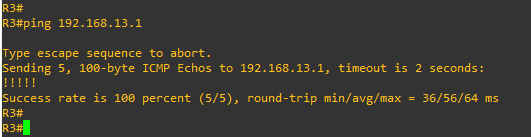
R3#ping 192.168.13.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.13.1, timeout is 2 seconds:
!!!!!
R2#show access-list R3-TO-R1
Extended IP access list R3-TO-R1
10 deny ip any any
R2#show ip inspect sessions
R2#
I just labbed this up again, just in case I’m not losing my mind ![]()
On Cisco VIRL, it’s also not working for me. I can ping between R3 and R1 without issues and I don’t get any hits on my access-lists.
On my older 2800 routers running IOS 15.1(4)M10 it’s working though:
R1#show version
Cisco IOS Software, 2800 Software (C2800NM-ADVENTERPRISEK9-M), Version 15.1(4)M10, RELEASE SOFTWARE (fc2)Let’s enable a debug on R2:
R2#debug ip packet
IP packet debugging is onTry a ping from R3:
R3#ping 192.168.13.1 repeat 1000 timeout 0R2 drops them:
R2#show access-lists R3-TO-R1
Extended IP access list R3-TO-R1
10 deny ip any any (1027 matches)Ping from R1:
R1#ping 192.168.13.3
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.13.3, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/2/4 msThis is traffic that R2 inspects:
R2#show ip inspect sessions
Established Sessions
Session 49BFA068 (192.168.13.1:8)=>(192.168.13.3:0) icmp SIS_OPENRene
Hi Rene and staff,
i am studying fw now and this is fun to lab this lesson because I never used transparent fw in real life, only routed ones
In this case
- fw is not seen as a hop in the network (that is why the name is transparent)
- sits between LAN and next-hop device (router)
- forwarding like a switch at L2, but inspection and filtering IP packets inside L2 frames
So…let’s go !
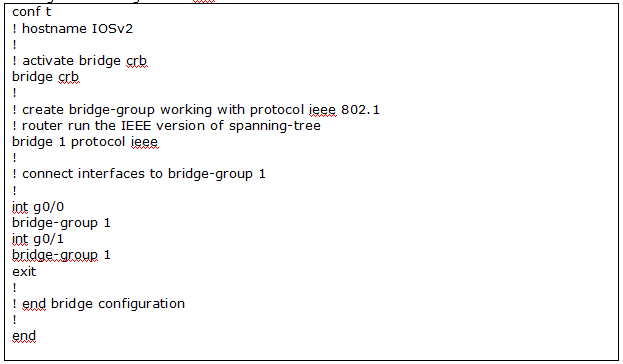
In my lab R2 is IOSv

Let’s configure interfaces
Let’s configure bridge
Let’s configure policy
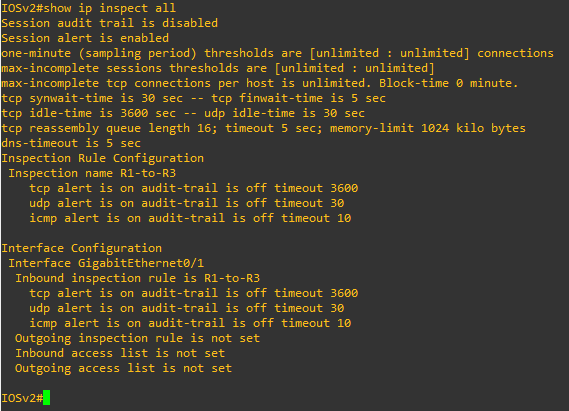
Access-list R3-to-R1 is not working
No match for the access-list

When pinging R1 to R3 or telnet R3 from R1: inspected sessions are empty

The L3 content of ethernet L2 frames are not inspected by the bridge, as we would have liked !
Oups …I wonder if this is related to ip cef ? but ip cef is on for ipv4

So what’s going on ? L2 frames are not inspected, IOSv works like just a bridge !
Bad configuration ?
Losing my mind too ![]()
Fw transparent mode has to work, is not it ?
And also, assume it works, i wonder if it consumes a lot of ressource inspecting every L2 frame ?
Regards
Hello Dominique
Both Rene and I tried to replicate your results and we get the same behavior as you. It seems that some things have changed in the later IOS versions. The truth is that CBAC is also quite old.
Instead, try the transparent firewall option in the zone-based firewall configuration found here:
Rene has arranged to update the content accordingly.
I hope this has been helpful!
Laz
Hi,
What are the use case scn=enarios for this bridging
Thanks
Hello Sims
I think this Cisco documentation explains it adequately:
The Transparent Cisco IOS Firewall feature allows users to “drop” a Cisco IOS Firewall in front of their existing network without changing the statically defined IP addresses of their network-connected devices. Thus, users can allow selected devices from a subnet to traverse the firewall while access to other devices on the same subnet is denied.
It is essentially the implementation of Context Based Access Control (CBAC) over a Layer 2 device. The advantages here include:
- The use of a Cisco IOS router - no specialized (and expensive?) firewall device is necessary. It’s kind of like a “poor man’s firewall” but does a decent job.
- There is no need to modify your subnets, since the device itself transmits frames at layer 2. It’s easy to place on your network with minimal topology changes.
- It gives you the ability to selectively allow or deny services or hosts within the same subnet.
This is by no means a full-scale security solution, but it can be more than adequate for many small to medium-sized businesses. And it is often the case that you will have a free IOS router lying around, so it often costs next to nothing.
I hope this has been helpful!
Laz