Hi Network Lessons,
I am new using ASA and planning update 2 Firewall via ASDM next week, I have checked that I need to update the two firewall firmware as per CISCO.
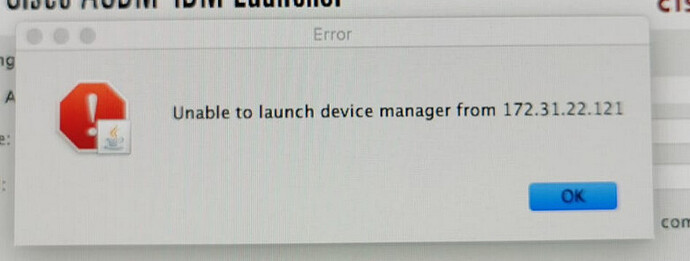
As the setup has been here before I came in the operation, I’m struggling to access the second FW ASDM to do backup first, I have checked that both firewall mode : Router
Here is the config for Active and Standby (Active would be 172.31.22.122 [Accessible ASDM] and supposed Standby [172.31.22.121 Unable to launch]
When I search the whole config and 172.31.22.121 only appears one and when I try to access it via browser, it is unreachable and only 172.31.22.122 reachable via browser[Prompt install ASDM]
crypto ca trustpoint ASDM_Launcher_Access_TrustPoint_0
enrollment self
fqdn none
subject-name CN=172.31.22.121,CN=_____ASA01P
keypair ASDM_LAUNCHER
crl configure
http server enable
http 172.31.22.64 x.x.x.x management
Active
> _____ASA01P# show interface ip brief
Interface IP-Address OK? Method Status Protocol
GigabitEthernet1/1 unassigned YES unset up up
GigabitEthernet1/2 unassigned YES unset up up
GigabitEthernet1/3 unassigned YES unset up up
GigabitEthernet1/4 unassigned YES unset up up
GigabitEthernet1/5 unassigned YES unset administratively down down
GigabitEthernet1/6 unassigned YES unset administratively down down
GigabitEthernet1/7 unassigned YES unset administratively down down
GigabitEthernet1/8 192.168.1.1 YES unset up up
Internal-Control1/1 127.0.1.1 YES unset up up
Internal-Data1/1 unassigned YES unset up up
Internal-Data1/2 unassigned YES unset up up
Internal-Data1/3 unassigned YES unset up up
Internal-Data1/4 1xx.2xx.1.1 YES unset up up
Management1/1 172.31.22.122 YES CONFIG up up
Port-channel1 xxx.x5.9x.116 YES CONFIG up up
Port-channel2 17x.3x.2x.x96 YES CONFIG up up
_____ASA01P# show failover interface
interface LAN_FO GigabitEthernet1/8
System IP Address: 192.168.1.2 255.255.255.0
My IP Address : 192.168.1.1
Other IP Address : 192.168.1.2
_____ASA01P# Show Failover
Serial Number: Ours XXX5AV, Mate XXX57K
Last Failover at: 22:21:05 SGT Oct 4 2021
This host: Primary - Active
Active time: 13033389 (sec)
slot 1: ASA5516 hw/sw rev (3.0/9.12(1)) status (Up Sys)
Interface management (172.31.22.122): Normal (Waiting)
Interface Outside (xxx.x5.9x.116): Normal (Waiting)
Interface Inside (17x.3x.2x.x96): Normal (Waiting)
slot 2: SFR5516 hw/sw rev (N/A/6.2.0-362) status (Up/Up)
ASA FirePOWER, 6.2.0-362, Up, (Monitored)
slot 2: SFR5516 hw/sw rev (N/A/6.2.0-362) status (Up/Up)
ASA FirePOWER, 6.2.0-362, Up, (Monitored)
Other host: Secondary - Standby Ready
Active time: 0 (sec)
slot 1: ASA5516 hw/sw rev (3.0/9.12(1)) status (Up Sys)
Interface management (0.0.0.0): Normal (Waiting)
Interface Outside (0.0.0.0): Normal (Waiting)
Interface Inside (0.0.0.0): Normal (Waiting)
slot 2: SFR5516 hw/sw rev (N/A/6.2.0-362) status (Up/Up)
ASA FirePOWER, 6.2.0-362, Up, (Monitored)
slot 2: SFR5516 hw/sw rev (N/A/6.2.0-362) status (Up/Up)
ASA FirePOWER, 6.2.0-362, Up, (Monitored)
Standby
> _____ASA01P# show interface ip brief
Interface IP-Address OK? Method Status Protocol
GigabitEthernet1/1 unassigned YES unset up up
GigabitEthernet1/2 unassigned YES unset up up
GigabitEthernet1/3 unassigned YES unset up up
GigabitEthernet1/4 unassigned YES unset up up
GigabitEthernet1/5 unassigned YES unset administratively down down
GigabitEthernet1/6 unassigned YES unset administratively down down
GigabitEthernet1/7 unassigned YES unset administratively down down
GigabitEthernet1/8 192.168.1.2 YES unset up up
Internal-Control1/1 127.0.1.1 YES unset up up
Internal-Data1/1 unassigned YES unset up up
Internal-Data1/2 unassigned YES unset up up
Internal-Data1/3 unassigned YES unset up up
Internal-Data1/4 1xx.2xx.1.1 YES unset up up
Management1/1 unassigned YES CONFIG up up
Port-channel1 unassigned YES CONFIG up up
Port-channel2 unassigned YES CONFIG up up
_____ASA01P# show failover interface
interface LAN_FO GigabitEthernet1/8
System IP Address: 192.168.1.1 255.255.255.0
My IP Address : 192.168.1.2
Other IP Address : 192.168.1.1
_____ASA01P# Show Failover
Serial Number: Ours XXX57K, MateXXX5AV
Last Failover at: 22:20:52 SGT Oct 4 2021
This host: Secondary - Standby Ready
Active time: 0 (sec)
slot 1: ASA5516 hw/sw rev (3.0/9.12(1)) status (Up Sys)
Interface management (0.0.0.0): Normal (Waiting)
Interface Outside (0.0.0.0): Normal (Waiting)
Interface Inside (0.0.0.0): Normal (Waiting)
slot 2: SFR5516 hw/sw rev (N/A/6.2.0-362) status (Up/Up)
ASA FirePOWER, 6.2.0-362, Up, (Monitored)
slot 2: SFR5516 hw/sw rev (N/A/6.2.0-362) status (Up/Up)
ASA FirePOWER, 6.2.0-362, Up, (Monitored)
Other host: Primary - Active
Active time: 13033471 (sec)
slot 1: ASA5516 hw/sw rev (3.0/9.12(1)) status (Up Sys)
Interface management (172.31.22.122): Normal (Waiting)
Interface Outside (xxx.x5.9x.116): Normal (Waiting)
Interface Inside (17x.3x.2x.x96): Normal (Waiting)
slot 2: SFR5516 hw/sw rev (N/A/6.2.0-362) status (Up/Up)
ASA FirePOWER, 6.2.0-362, Up, (Monitored)
slot 2: SFR5516 hw/sw rev (N/A/6.2.0-362) status (Up/Up)
ASA FirePOWER, 6.2.0-362, Up, (Monitored)
Hoping you would able to help me, I don’t want to update the firewall without backing the second FW and accessible via ASDM.