This topic is to discuss the following lesson:
Hi ,
As i understand the IP PHONE working as a switch and separate traffic between voice and data and the connections between IP PHONE-COMPUTER and IP PHONE-VOICE(PHONE) are like access port and tagged with corresponding vlan that learning with cdp from the switch and then send to the trunk port . Is it wright ?
Please let me now
Dionisis
Thanks
Hi Rene,
So does that mean even though we configure ‘switch-port mode access’ , but for VOICE VLAN that same port works as trunk port because it carries 2 VLAN?
thanks
Hello Dionisis
Yes you are correct in your description. Any traffic coming from the PC through the phone will be untagged and will go to the access VLAN configured on the port of the switch. All voice traffic is tagged and will go to the voice vlan configured on the port of the switch.
Keep in mind that the voice vlan configuration not only configures the appropriate VLANs for data and voice, but also sends voice traffic with a QoS based on IEEE 802.1p CoS. In other words, a Quality of Service technique is automatically incorporated into the functionality of the voice VLAN.
I hope this has been helpful!
Laz
Hello Abhishek
In the past, before the advent of the switchport voice vlan command you would have to configure a port as a trunk port that included both the voice and data VLANs. It was around 10 years ago when I was first learning about Cisco IP telephony where we would use such a configuration. Back then, connections to IP phones were literally trunks.
Today however, we use ports configured with voice VLANs. Such a port will have both the switchport mode access command as well as the switchport voice vlan command. So is this an access port or a trunk?
They are often referred to as “a special type of 802.1q trunk”. This makes sense since 802.1q tagging is included in the frames that are in the voice VLAN. However, Cisco has (more correctly in my opinion) referred to such a port as a @multi-VLAN access port."
Really, you can take your pick of what to call it, just realise that 802.1q tagging takes place on the voice frames and does not on the data frames.
I hope this has been helpful!
Laz
Hi Rene,
How does switch differentiate between DATA traffic and VOICE traffic ? Consider IP phone is non-cisco
Hello Aniket
Let me quote Rene from his lesson:
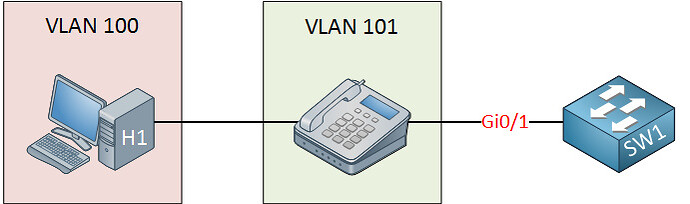
This is the image he uses:
Behind the scenes, we have a trunk between our switch and IP phone. The port on the IP phone that connects to the computer is an access port. The IP phone will forward all traffic from the computer to the switch untagged, traffic from the IP phone itself will be tagged. The only two VLANs that are allowed though, are the access and voice VLAN.
So, all traffic to and from the phone will be tagged (voice traffic) and all traffic to and from the PC will not be tagged (data). For more information about tags and how they work, take a look at this lesson:
I hope this has been helpful!
Laz
Thanks for the explanation Lazaros,
However I have seen a working scenario wherein DATA VLAN is 135 & VOICE VLAN is 137, also switch port is not TRUNK, Native VLAN is 1. So how could DATA Vlan traffic will go untagged as DATA Vlan being 135… Also under switchport we are giving commnad as "Switchport mode access " for DATA vlan, then how can we put this interface in Trunk mode? (as per my understanding switchport would be either access or trunk port)
Hello Aniket
I think you had the same post on another thread, but that’s ok, cause I can add something here.
If the native VLAN on a trunk is 1, then this VLAN will definitely function as the data VLAN in a scenario where a PC is connected to an IP phone connected to an access switch. VLAN 135 was not being piped through the phone to the connected PC in this particular instance. In order to answer more specifically, we’d need to see the actual configuration.
That’s the beauty of the voice VLAN configuration. It provides a third alternative to just access or trunk by allowing you to configure an access port but tag only voice packets so an IP phone can intercept them. See more about this in my reply to your other post:
I hope this has been helpful!
Laz
I’m working on the Voice VLAN tutorial in one of the lessons - following the tutorial using packet tracer. Everything is working but one command is not. That is the show interfaces GigabitEthernet 0/1 trunk command. It has a marker ^ at trunk. Any ideas why this won’t work?
Thanks
Hello David
I tried issuing the command you stated on packet tracer using the 3560-24PS switch and indeed it didn’t have it available. This could be because you’re using packet tracer. You can use the show interfaces trunk command instead to show you all the information about all trunks. Or you can use the show interfaces GigabitEthernet 0/1 switchport command to show info about the switchport configuration of that particular trunk.
Remember that Packet Tracer has a subset of all of the available commands on a real device. In order to get the same availability of commands, I suggest you use GNS3.
I hope this has been helpful!
Laz
Hi Rene & Team,
What is the reason we have to have an access port working as (virtual) trunk. Why can’t we just have Trunk if need to transport more than 1 VLAN’s.
One reason I could think of is related to STP stuff where we wana control BPDU sending receiving on access ports globally. Would appreciate if you could explain in a bit detailed way the reason vendors do this.
Hello Babar
Take a look at this post and you will see that in the past, for IP phones, the only way to make them work with a workstation is to create a trunk port as you suggest:
However, creating a Voice VLAN configuration on a port is advantageous for several reasons:
- First of all, the concept of a trunk port is almost always between two switches, so that you can carry multiple VLANs. Here we have an end device, an IP phone, and it goes against the philosophy that end devices connect to access ports.
- By creating a “specialized” voice VLAN port, you are also automatically enabling certain QoS features on that port that are preconfigured. If the platform supports it, CoS and DSCP values are automatically adjusted (if QoS is enabled) to give priority to the voice packets.
- The configuration of a Voice port really is something unique. It’s not really an access port since more than one VLAN is being transported, but it’s not a trunk port either, because you have end devices connecting to it. I see it as a third category of port types that has a specialized purpose.
I hope this has been helpful!
Laz
What happen if I use #switchport mode trunk on a swithcport connected to ip phone? If I use that then it will show the trunking.
Hello Jalendra
It is possible to set up the port to which an IP phone is connected as a trunk port. A voice VLAN port is really just a special kind of trunk. And in the past, that’s how IP phones were configured (when you wanted to connect a workstation to the phone). You can find out more information about this at the following post:
I hope this has been helpful!
Laz
Is a different set up also possible? I might be totally mistaken but (I think) I remember that the IP phone at my previous work was attached to the computer instead of the IP phone in the middle.
Hello Marit
As far as I know the only option is to have the phone in the middle. I am not aware of an implementation where the PC connects to the switch, and the phone in turn to the PC.
I hope this has been helpful!
Laz
Yes, I think you are right, I just did not have a trained eye back then… ![]() Thanks!
Thanks!
I was reading the cisco documents and books and was wondering when would Vlan 0 be used?
They mentioned there are 4 configurations which are:
switchport voice vlan vlanid - which is what is covered in this topic which says that voice traffic will be sent tagged by whatever vlan was configured using this command and the PC data will be sent untagged.
switchport voice vlan dot1p - says that the voice traffic will be sent using vlan 0 and PC traffic untagged.
switchport voice vlan untagged - says the voice traffic and PC data will be sent without a vlan tag
switchport voice vlan none - and this says the voice traffic and PC data will go by what is on the Access VLAN
So when would I configure to use the dot1p command? And now that I think of it, how would I decide to use any of these commands? But the dot1p I’m very curious about because it involves Vlan 0 which there seems to be little information floating around.
Any information would be appreciated! ![]()
Hello Grant
In order to understand the use of VLAN 0, we must first understand what a VLAN tag is. A VLAN tag (defined by IEEE 802.1Q) is an additional 4 bytes of data that is added to the header of an Ethernet frame. This tag has several fields which include a 12 bit VLAN identifier, and a 3-bit field called a Priority Code Point (PCP) which is defined in IEEE 802.1p which provides prioritization information used by Layer 2 QoS mechanisms. VLAN tags are added to the headers of frames whenever they traverse a trunk (to keep the VLANs separated) and to segregate voice from data traffic when using PC–>IPPhone–>Switch interconnectivity connectivity. More details about this can be found at the 802.1Q Encapsulation Explained lesson.
Now back to VLAN 0. In order to have a VLAN ID of 0, you must have an 802.1Q tag. An untagged frame doesn’t mean that the VLAN ID is 0, it simply means that there is no VLAN ID field in the frame header at all! So untagged does not equal VLAN 0.
Because both the VLAN ID and the PCP field exist in the same tag, Layer 2 QoS mechanisms can only be applied to frames that have such a tag. But what if you want to apply Layer 2 QoS mechanisms to a frame that isn’t on a trunk or on an IP phone connection? You have no PCP info in the frame header, so you cannot apply Layer 2 QoS. This is where the VLAN 0 ID comes in.
The purpose of using a VLAN ID of 0 is when you want to take advantage of the QoS mechanisms provided by the 3-bit PCP field in situations where there is no need for a VLAN ID. This way you can prioritize such frames based on their PCP fields, and the VLAN ID is ignored completely.
The following Cisco documentation explains it quite well.
Out of your four scenarios, only the second one involves VLAN 0. The others simply use regular VLAN IDs or are untagged completely.
I hope this has been helpful!
Laz