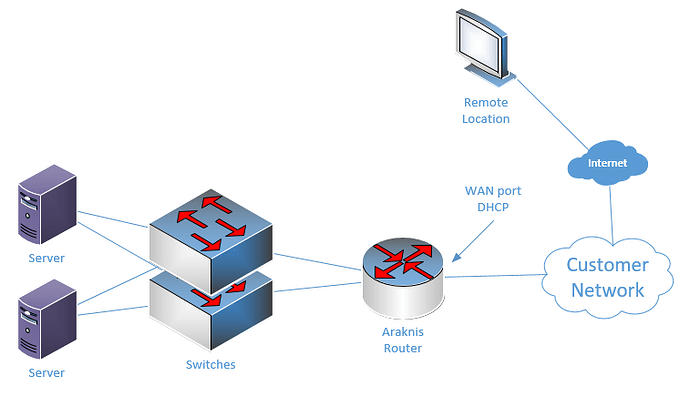
I am working on a project in which we are installing equipment throughout a campus which we will need remote access to. The campus is providing us an outside network connection from their network which we are planning on connecting to our router’s WAN port. We are using our own router (Araknis an-300-rt-4l2w) to provide our own network so the campus does not have to deal with maintaining and updating the equipment. Our router would connect to our switches and hand out IP addresses from it’s DHCP server. This all seems to work just fine but we are unable to use the VPN features (OpenVPN) from our router to connect to the network from the outside. I believe this is due to double-NAT as our router pulls an address from the campus network and our AV equipment is then behind our router. Is there anyway around this using the crude topology below? I have tried playing with static routing but have not had any success. We would like VPN access as it would be a more efficeint way to troubleshoot, etc.
Hello Bruce
There are many reasons for which a VPN connection would not function. NAT would be one of them, MTU issues may be another. To be honest, it is very difficult to provide any meaningful advice without knowing a little more about the topology, the equipment and the technologies being applied at the edge of the network. Can you share some more information?
Laz
Laz,
Thank you for the response. I will try as best I can to describe what we are trying to accomplish.
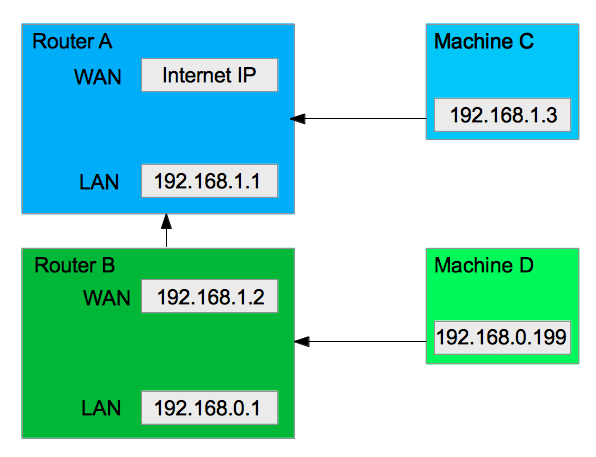
The client will be providing us a connection to their network which will have outside internet access (I am unsure currently what equipment we will be connecting to). This connection will go to our router’s WAN port (Araknis AN-300-RT-4l2w) and the router will receive a DHCP address from the client’s network. The router will then create it’s own range of DHCP addresses and connect to a couple of cisco smb switches. These switches will connect to our host equipment which we will need remote access to through the network for troubleshooting.
What we would like to have happen is to be able to connect to this network we created on the client’s site through a VPN connection. Either Gateway to Gateway or through using the OpenVPN server operating on the router we are installing onsite.
As of now I am not sure what the client will be providing us in terms of the edge network connection. Any suggestions on things to look for or configurations that could make all of this possible I would greatly appreciate the feedback! I tried mocking this setup in our shop and was unable to get a connection working. Essentially it was setup the same way above with no additional configuration to the edge network.
Hello Bruce
From my understanding, this is your topology:
And you want to access the servers from the remote location. Now because we have a “black box” which is the customer network, this may present an issue in understanding what options are available. Also, I am not familiar with Araknis as a vendor. However, here are some things to keep in mind as you research the solutions to this problem:
- Find out what the maximum MTU is from end to end. This will allow you to make sure that any overhead that may be added by the VPN connection will not cause frames to exceed the maximum MTU at any point along the path.
- Verify that the ISP as well as the customer network edge will allow incoming connections through any firewalls or NAT mechanisms. You can coordinate with them in order to verify that this is the case.
- Verify that the Araknis router does not have any security features blocking VPN access or NAT translation mechanisms that may obstruct VPN creation.
- For any network devices such as a router, it’s always preferable to use a static IP address. Although this may not have a direct impact on the VPN creation, it is always best practice to do so.
I hope this gets you started. If you get any more info about the customer network or the ISP, feel free to share it so we can take a deeper look into the issue.
I hope this has been helpful!
Laz
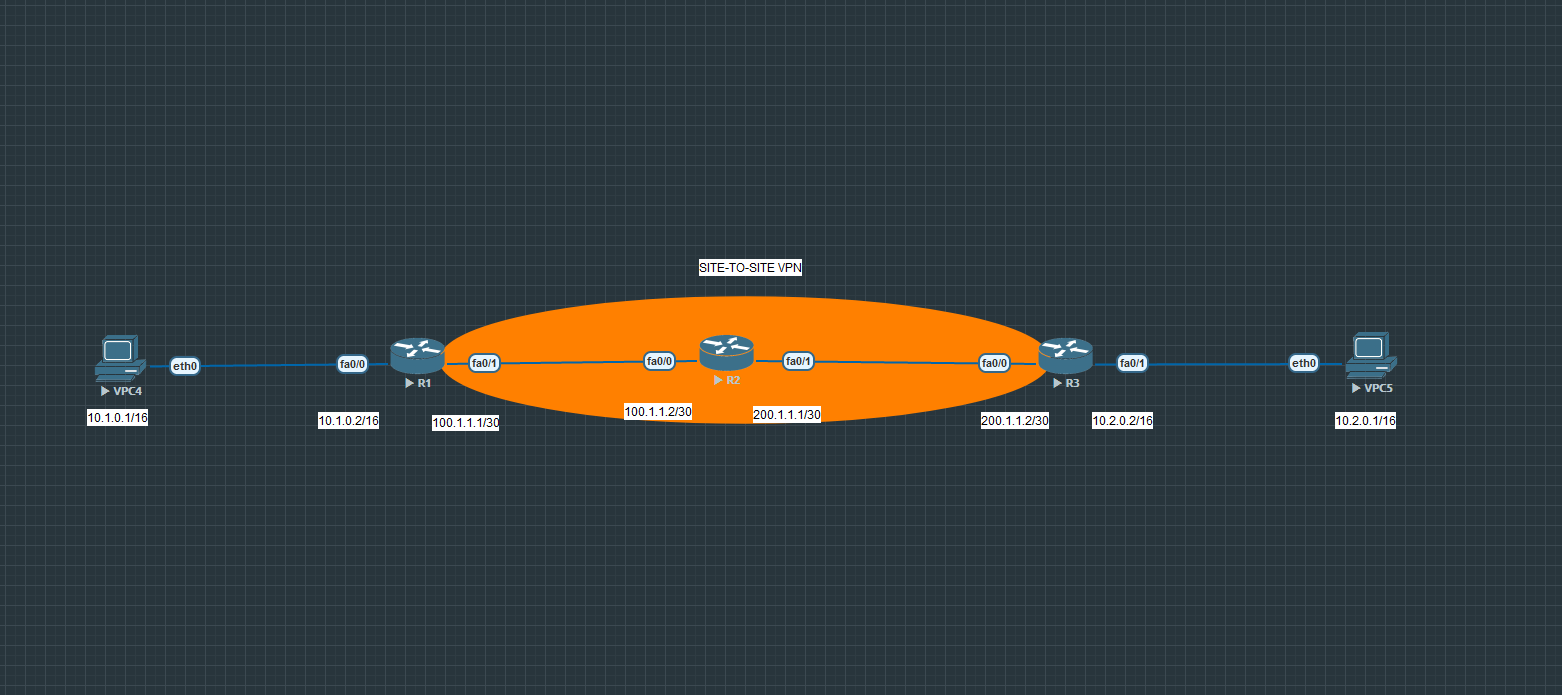
Wasn’t really sure where this question should go. The attachment is an EVE-NG lab for a Site-to-Site VPN with 3 routers. R2 is simulating the internet. the WAN interface on R1 and R3 have OSPF enabled in area 0. OSPF is not enabled on the LAN interfaces. So R1 doesn’t know about the LAN behind R3 and R3 doesn’t know about the LAN behind R1. The tunnels come up packets get encrypted and decrypted but I also get the message 10.2.0.1 “icmp_seq=1 timeout” messages. R2 only sees directly connected networks.
Hello Donald
This topology is similar to the one shown in the following lesson:
I don’t know exactly the VPN configuration that you have applied, but the principle is the same. In the lesson, the hosts are represented by loopback interfaces on the routers. In order to allow the hosts on either end of the VPN to communicate, you will see in the lesson that a static route was added to the network on the other end of the site-to-site VPN. If R1 does not know about the 10.2.0.0/16 network, then it won’t be able to route traffic there. Similarly, if R2 doesn’t know about the 10.1.0.0/16 network, it won’t be able to reach it.
You must include routing, either static (as in the lesson I linked to) or via OSPF so that these networks can be learned and reached.
I hope this has been helpful!
Laz
Laz
Once static route is added works without timing out. I was under the impression once the interesting traffic reached R1 and triggered the tunnel since the original packet was now encapsulated in the ipsec tunnel R3 would find the correct destination.
I have added configurations from R1, R2 and R3 just for clarity.
R1 site-to-site VPN.txt (1.2 KB)
R2 site-to-site VPN.txt (806 Bytes)
R3 site-to-site VPN.txt (1.2 KB)
Thanks for your help.
Laz
I created the video lab in EVE-NG you referenced. Routing has to be added to get VPN to work.
Also watched a video that talked about Crypto Map Order of Operations which stated Encryption applies after routing - A static route may be needed.
The lab example and the video cleared things up for me. Thanks again.
Hello Donald
What you have configured is a policy-based VPN, similar to the lesson I included in the previous post.
Any traffic coming in to R1 will have a destination IP address. That destination IP address will be matched first in the routing table. The routing table will indicate the next hop IP, sending it out of the appropriate interface, and only then will it be matched to the ACL in the crypto policy. If the destination address is not in the routing table, the packet will be dropped before it can be matched to the ACL and be matched as interesting traffic. This is why we need that static route.
I hope this has been helpful!
Laz