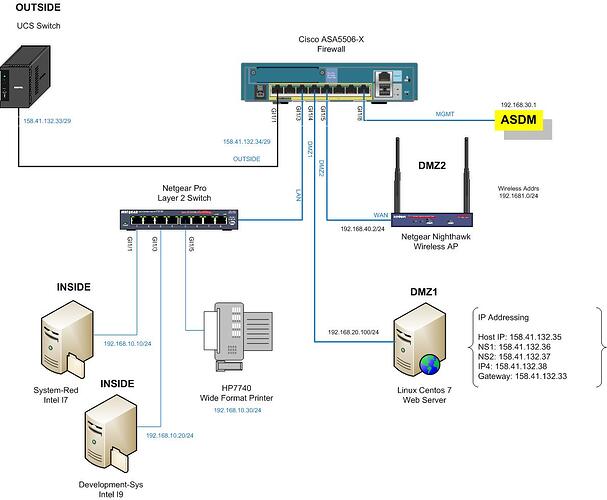
I have a CentOS system running CWP (Centos Web Panel, 192.168.20.100). The system is connected to the ASA interface on the same subnet (192.168.20.1). The server has a public ip address that gets natted to the 192.168.20.1 address. The server also has two public IP addresses defined for NS1 and NS2 in the running DNS instance on this server. The problem I am having is I can’t seem to get any outbound connectivity for DNS queries, updates, etc. The console log on the server when doing a “DIG ns1.nettrades.biz” comes back with error “no servers could be reached”. In using packet tracer, I set the interface dmz1 (192.168.20.1); For packet type (UDP); Source (IP 8.8.8.8); Source Port (53); Destination (IP 192.168.20.200 - Server); Destination Port (53); Run it and “Packet is Allowed”. Same result in reverse. Any ideas? Thanks in advance!!
Hello Wes
Thanks for sharing your setup and the challenges you are facing! I’m not sure if I have fully understood the setup, so if I’m mistaken in something please let me know.
You have your CentOS device with an IP address of 192.168.20.100/24 connected to the ASA on a port configured as a DMZ. The ASA is configured to translate that address using NAT to 158.41.132.35/29. However, the server is unable to successfully reach the two NS devices (158.41.132.36 and .37) for DNS queries etc, correct? Here are my thoughts that my help you in your troubleshooting:
- First, in the diagram you have an IP address for the server of 192.168.20.100, while in your text you mention 192.168.20.200. I will assume the .100 private address for the server is correct.
- Secondly, I see the IP addressing information in your server is in the 158.41.132.32/29 subnet. Shouldn’t that actually be the internal private address? i.e. 192.168.20.100/24 with a gateway of 192.168.20.1? The NATting to the outside address should be done by the ASA. I’m not sure if this was just informational or if you actually configured it that way.
- I assume however that all of that is configured correctly, and your server is actually able to reach other addresses on the Internet with the appropriate NAT translation. Otherwise your troubleshooting wouldn’t focus only on the DNS queries, but connectivity in general.
- Are you able to ping the 158.41.132.36 and .37 addresses? In other words, is DNS the only problem or connectivity in general?
I see you used the ASA packet tracer feature to check if packets are allowed. You used it on a test address of 8.8.8.8. However, I suggest you test it using either one of your NS addresses because these are on the same subnet as the NAT-translated public address, and that will affect how the ASA deals with that packet. If you do that, I believe the packet tracer results will give you a more definitive answer as to why they are being dropped.
If I have misunderstood any of your configurations or tests, please clarify so that we can help you further. Test it out and let us know how you get along!
I hope this has been helpful!
Laz
Hello Laz,
Thank you so much for replying!
You were actually very close. Let me explain.
My web server is connected to ASA gi1/4. The IP address on that interface is 192.168.20.1. The server’s address is 192.168.20.100.
The name servers NS1.nettrades.biz and NS2.nettrades.biz are running in the DNS service on that server.
I think the issue is NAT. This is a weird kind of Linux install. I am running an application on the Linux server called CWP (Centos Web Panel). It is very
Close to CPanel if you have ever been exposed to that. In setting up CWP, it sets the servers IP address to the public address – 158.41.132.35. Keeping that in
Mind, most people who use this have a private IP. Mine is 192.168.20.100. There is a checkbox on the setup page in CWP that says to check this box if you want to
Use NAT to translate the private ip – 192.168.20.100 to 158.41.132.34?
I am thinking that I should not have checked the NAT box because the server is most likely Natting from 192.168.20.100 to 158.41.132.35. Then comes the ASA.
It is trying to NAT again, but it is seeing the public address coming in, not the private address. Same thing with the nameserver addresses (public).
The server name is mars.nettrades.biz and I can get to it’s CWP control panel from the INSIDE interface just fine using 192.168.20.100. If I run a DIG from the server against any
Public address on that server, the message log Shows that it could not connect outbound. So, nettrades.biz DNS record is not getting propagated (not getting past the ASA). I do have DNS inspection Turned on. Did not matter.
I am going to turn off NAT on the server today and see what happens but if I do that, I will have to change all IP addresses that are private. Then, the server will no longer be on
The 192.168.20.1 network. Delimma !! You may think, well why not use one of my public address on the DMZ1 interface? I can’t because I lease a block of 5 usable addresses
( /29 ). One of those addresses is used for the OUTSIDE interface. You can’t route between two subnets that are the same address. So, DMZ1 has to stay private.
I know this is long and I do very much appreciate you taking the time to help. What are you thoughts?
Thanks,
Wes Senter,CEO
Songwriters Portal Intl, LLC
Hello Wes
Thanks for the detailed response! I understand the dilemma. Ideally, if you’re using a DMZ for your server, you would either have another public subnet for that DMZ (other than the one on your outside interface) or you would employ NAT on the ASA and translate all of the addresses to private. As you say, there’s no middle ground, you can’t route between two addresses in the same subnet. So it’s a matter of design. Let us know how your changes to NAT go and what the results are.
I hope this has been helpful!
Laz
Hello Laz,
Thanks for the reply. Actually, I am doing all of that already. The DMZ interface has a private ip. That private ip is getting natted to the servers public ip for inbound traffic. Same going out. All packets verified with packet tracer. All packets allowed. This includes udp port 53 for DNS. However, when I do a DIG command on the server for my domain name, I do get a reply. Before I didn’t. I can do a DIG for 8.8.8.8 and I get a good resolution. If I do the DIG on my domain name, I do not get the answer field “1” . So, I don’t know about this. Question? When the ASA natts the DMZ private IP to the public ip of the server, that public address must go through the outside interface, which is itself a public ip on the same subnet. I would think that would not route, however I am getting a pass from the packet tracer on the natted servers ip address. ???
Thanks,
Wes
Hello Wes
OK sounds good that one part of the problem has been resolved!!
Since your server does receive a response when querying 8.8.8.8, but not when querying its own domain, the issue may have to do with the NAT reflection or hairpin NAT behavior on the ASA. I see that your nameservers are on the same subnet as your server and your external ASA interface. Where are those DNS servers running, internally to you network? If so, are you querying the external address or the internal one? If you’re querying the external address, (i.e. dig 158.41.132.36 nettrades.biz) or the internal one? Try resolving using the internal address to see if the issue is indeed network-related or DNS server-related.
If you are querying the external address, you may have an issue with the NAT hairpin behavior. You can also use the +trace option for the dig command to trace the path from the root DNS servers to AS for your domain to see where the breakdown occurs. If the issue is indeed hairpin NAT, take a look at this lesson for more info:
Hopefully that will help you in your troubleshooting process for that. Let us know how you get along!
Yes, however, the configured address of the outside interface is never used as a “next hop” in the routing process. Indeed, the outside interface “adopts” the external address of the server. So there is no “routing” from one address to another in the same subnet. Take a look at this NetworkLessons note for more information.
I hope this has been helpful!
Laz