Hello.
As I’ve mentioned before, some Wireless topics aren’t covered by NW so I tend to create a new thread when talking about them. Is it okay if I create a new thread each time or should I post these questions to a specific wireless thread?
3.3.d Describe the main principles and use cases for Layer 2 and Layer 3 roaming
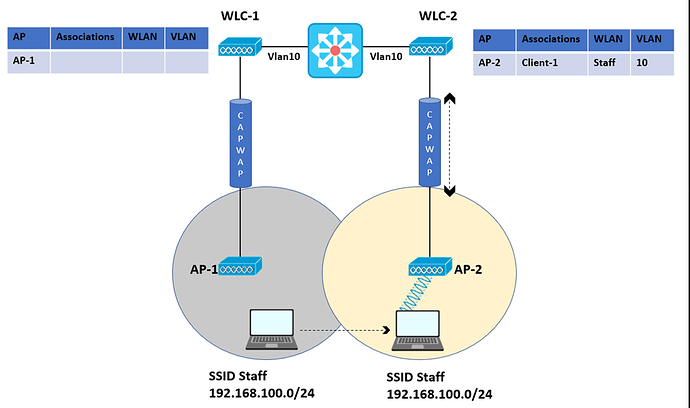
I always thought that roaming works like this - the same SSID/security parameters are configured on the WLC and the APs, the wireless station then associates to the second AP as the user walks from one BSS to another and that the subnet remains the same.
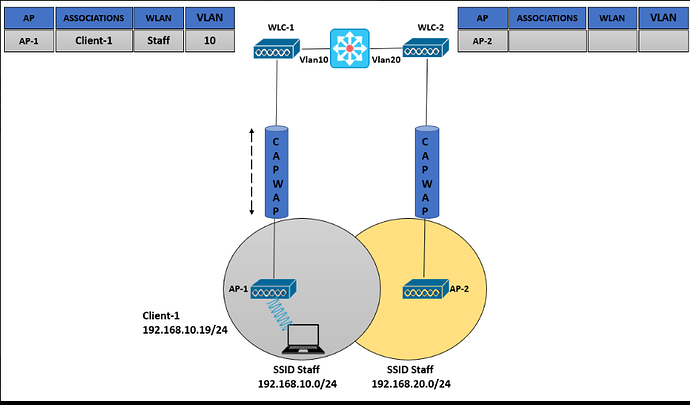
Then the book talks about L3 roaming (this isn’t a snippet from the book, it’s available for free on google)
What exactly is this design? Why would there ever be an SSID like Staff that would have different subnets, depending on which AP you associate with? Wouldn’t you just configure your DHCP server to provide one subnet for each WLAN?
This kind of configuration indicates three things
- The SSID is the same
- The security parameters such as the PSK are the same
- The VLAN mapped to that SSID and the subnet are different for both SSIDs
This seems a very unusual way for me to design a wireless network, why would you ever want to do this?
Some more questions,
Does DHCP happen all the time or only sometimes or what is it dependent on?
The client authentication process presents the biggest challenge because the dialog between controller and a RADIUS server, in addition to the cryptographic keys that need to be generated and exchanged between the client and an AP or controller, can take a considerable amount of time to accomplish. Cisco controllers offer three techniques to minimize the time and effort spent on key exchanges during roams:
■ Cisco Centralized Key Management (CCKM): One controller maintains a database
of clients and keys on behalf of its APs and provides them to other controllers and
their APs as needed during client roams. CCKM requires Cisco Compatible Extensions
(CCX) support from clients.
■ Key caching: Each client maintains a list of keys used with prior AP associations and
presents them as it roams. The destination AP must be present in this list, which is lim-
ited to eight AP/key entries.
■ 802.11r: This 802.11 amendment addresses fast roaming or fast BSS transition; a client
can cache a portion of the authentication server’s key and present that to future APs as
it roams. The client can also maintain its QoS parameters as it roams
I haven’t covered much wireless security but I understand somewhat the last two, just not the first one. How exactly does CCKM operate?
Each client uses a unique encryption and decryption key, right? This key has to be derived somehow, right? Does the WLC just straight up tell the new AP (the one the client is roaming to) what the key is with CCKM?
Thank you.
David