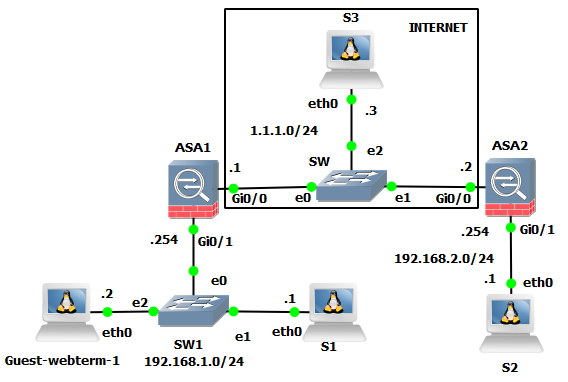
This topic is to discuss the following lesson:
Hello Rene,
What device did you use for the cloud? The one that I saw in gns3 has 3 interfaces, not 3. This lab requires 3 interfaces for the cloud device.
Hello Patrice
Because the two ASAs and the S3 server are on the same subnet in the topology, you can simply use a switch to represent the cloud. The prerequisite is that connectivity is achievable between those devices.
I hope this has been helpful!
Laz
Hi Rene and staff,
i lab this lesson in GNS3 like this
S1,S2, S3 are build with GNS3 appliance Networkers’s toolkit
Guest-webterm is a linux GUI client with firefox, build with the GNS3 appliance Webterm
My lab works fine, but i want to add these comments and questions
1)
i prefer to name the internal subnet object as “INTERNAL” rather than “INSIDE”, not to be confused between a network object and the name (if) of the internal interface.
So the nat configuration becomes
- nat (inside,outside) source static INTERNAL INTERNAL destination static LAN2 LAN2
or - nat (inside,outside) source static INTERNAL INTERNAL destination static LAN1 LAN1
Could you clarify this command step by step, because i am confused with the repetition of the network objects ?
Also i am confused with the place of the NAT commands: why are some NAT commands inside network objects, and some others in general config ?
- IOS and ASA are quite different when configuring VPN site to site (i used to configure vpn site to site with ios)
Where you used “authentication pre-share” with IOS in phase 1, you have to use tunnel-group with ASA, is not it ?
Cisco’s help says you have to use a WORD…but this is not working when you use a word that is not the IP address of the neighbor. The configuration is accepted, but this is not working. Do you know why ? So it is not working, but … suppose you use a WORD: in this case, it should be referenced in another place ? where ?
Regards
For your NAT, you’re saying this.
NAT the following:
NAT (INTERNAL IP) and change to (INTERNAL IP) in this case do not change it!
NAT (LAN2) and change to (LAN2) in this case do not change it!
NAT on ASA are broken the down like this every time.
Original Source IP:
Translated Source IP:
Destination IP:
Translated Destination IP:
If both source/destination stay the same, we are exempting them from all NAT statements, especially our PAT statement for internet traffic so they match our crypto ACL for a tunnel. This is called a NAT exemption for this reason.
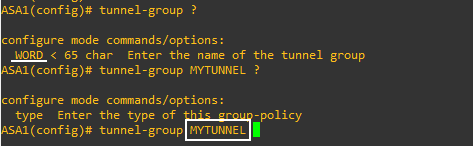
You need to configure some variable within a tunnel group depending on the type. So you create it like you did with the tunnel-group NAME command. But you also need to clarify values.
As an example for a IPSec Remote Access Tunnel Group.
tunnel-group "tunnel_group_name" type ipsec-ra
For an IPSec RA tunnel for example, you need to configure some attributes.
tunnel-group "tunnel_group_name" general-attributes
In here you configure things like authentication servers, default group policy to reference.
For a L2L Tunnel group it might look something like this:
tunnel-group DefaultL2LGroup type ipsec-l2l
tunnel-group DefaultL2LGroup general-attributes
no accounting-server-group
default-group-policy DfltGrpPolicy
tunnel-group DefaultL2LGroup ipsec-attributes
no pre-shared-key
peer-id-validate req
no chain
no trust-point
isakmp keepalive threshold 10 retry 2
Hello Dominique
What’s happening here is something called “twice NAT” and is used to identify both the source and destination address in a single rule. As stated in this Cisco documentation:
Specifying both the source and destination addresses lets you specify that a source address should be translated to A when going to destination X, but be translated to B when going to destination Y, for example.
And actually, when you use the same object for both real and mapped addresses, you are doing a very special type of twice NAT called Identity NAT. This is where the real and mapped objects are the same. Identity NAT simply says “translate to the same address” or simply “don’t translate”.
You can find out more about Identity NAT at the following Cisco link:
https://www.cisco.com/c/en/us/td/docs/security/asa/asa95/configuration/firewall/asa-95-firewall-config/nat-reference.html#ID-2091-0000038c
You can also find out more at this post:
This has to do with the way in which NAT is applied. When the NAT statement is within the object, this kind of configuration is called network object NAT. It’s a quick and easy way to configure NAT for a single IP address or a range of addresses, or a subnet. The NAT command within the object is applied to the similarly configured subnet within the object. You can find out more about it here:
Looking at the lesson I do see a typo where the NAT statement was outside the object, so I’ll let Rene know to fix that…
This command will specify a tunnel-group, but you must create and configure the tunnel-group for it to function. This can be done using several command modes including:
tunnel-group general-attributes
tunnel-group ipsec-attributes
tunnel-group webvpn-attributes
tunnel-group ppp-attributes
One or more of the above should be used to enter the configuration mode of the particular attributes for this tunnel group. More about this can be found at this Cisco ASA command reference:
You can find out more details on how to configure these and what all of their parameters are at the following Cisco documentation:
https://www.cisco.com/c/en/us/td/docs/security/asa/asa95/configuration/vpn/asa-95-vpn-config/vpn-groups.html
Note that the entities called “tunnel-groups” are now called VPN connection profiles, however, the syntax seems to be the same.
I hope this has been helpful!
Laz
Hello Laz,
I’ve tried this same config but the exemption only works on my topology when the NAT exemption statement is above the NAT statement for internet connection.
Basically this 3 order of statement works for me:
1st for DMZ to OUTSIDE statement (DMZ to INTERNET)
2nd for INSIDE to OUTSIDE exemption statement
3rd for INSIDE to OUTSIDE dynamic statement (INTERNAL TO INTERNET)
but when I swapped the 2nd and 3rd, the traffic coming from behind of the ASA will go through 2nd statement, not to the 3rd which is for the exemption.
So I’m curious how to make this configuration “dual-stack”, that is, I want to include my IPv6 stack through the same tunnel that was established on the IPv4 network (or do I need to create a separate IPv6 tunnel for the independent traffic?)
Marcos
Hello Marcos
It was somewhat difficult to find information about the creation of an IPSec site-to-site dual-stack VPN between ASAs. Apparently, you can find some information about it here.
Specifically, in the ACL that defines what traffic to encrypt, you can add IPv4 and IPv6.
I hope this has been helpful!
Laz
Looked at what he did and its along the lines of something I was trying, but the “work around” was to use IKEV1 for IPv4 and IKEV2 for IPv6 so that the two tunnel protocols wouldn’t run into one another. The issue however is now your doing two different setups when I wanted to eliminate IKEV1 from my overall system.
Its weird that for over a decade everyone is trying to be “dual-stacked” in the ISP business however there is so little support for actually doing dual-stacked (nor documentation). Lots of examples of IPv4 or IPv6, but never with both at the same time.
Marcos
Hello Marcos
Indeed it is frustrating that no such precedent has been set. Unfortunately, there is little documentation about this and I haven’t been able to find others that have successfully created a single dual-stack IKEv2 VPN. It may be worth doing some further experimentation or raising it as an issue on Cisco community Cisco learning network forums.
I wish we could have been more helpful!
Laz
Hi there,
I have read the threads and came across Twice NAT, which had been mentioned previously. I also read the Cisco documentation but need some advices for clarification.
I quoted the following from your chapter.
"ASA1(config)# nat (INSIDE,OUTSIDE) source static INSIDE INSIDE destination static LAN2 LAN2
The rule above tells the ASA to translate traffic:
From INSIDE 192.168.1.0/24 destined to OUTSIDE 192.168.2.0/24 to 192.168.1.0/24.
From INSIDE 192.168.2.0/24 destined to OUTSIDE 192.168.1.0/24 to 192.168.2.0/24."
How one rule specify both “INSIDE 192.168.1.0/24 to OUTSIDE 192.168.2.0/24” and “INSIDE 192.168.2.0/24 to OUTSIDE 192.168.1.0/24” at the same time?
Hello PO
You are indeed correct. This is a typo, and the statement should read:
From INSIDE 192.168.1.0/24 destined to OUTSIDE 192.168.2.0/24 to 192.168.1.0/24.
From OUTSIDE 192.168.2.0/24 destined to INSIDE 192.168.1.0/24 to 192.168.2.0/24.
Rene has corrected the typo in the lesson.
I hope this has been helpful!
Laz
Hi Laz,
Thank you for confirmation.
I have another question regarding access list.
"
We need an access-list to define the traffic we want to encrypt. In this example, we’ll encrypt all traffic between the 192.168.1.0/24 and 192.168.2.0/24 subnets.
ASA1(config)# access-list LAN1_LAN2 extended permit ip 192.168.1.0 255.255.255.0 192.168.2.0 255.255.255.0
"
From the above list I quoted, please enlighten me as I’m quite confused.
Could you break down the list and explain a bit? My understanding for access list is to either permit or deny traffic from entering ASA1 OUTSIDE interface. How does access list encrypt the traffic?
Source IP: 192.168.1.0/24 (ASA1)
Dest. IP: 192.168.2.0/24 (ASA2)
My interpretation for this access list is as follows.
ASA1’s access list, LAN1_LAN2, is allowing all the traffic from 192.168.1.0/24 (ASA1) to enter 192.168.2.0/24 (ASA2).
As this is not bidirectional, Wouldn’t traffic from 192.168.2.0/24 (inbound) still be blocked and ASA won’t be able to communicate with each other? Am I missing something here?
Hello PO
You must remember that access lists can be used for two fundamental purposes: to filter traffic, and to classify traffic. If we were to apply this access list to an interface in an inbound or outbound direction, then the access list would indeed be used for filtering, and it would permit and deny traffic.
However, in this case, the access list is not applied on an interface, but is referenced to the proposal in the very next set of configurations:
ASA1(config)# crypto map MY_CRYPTO_MAP 1 match address LAN1_LAN2
This command will use the ACL to match traffic and classify it (it will not filter it). Matched traffic will be encrypted, and traffic that does not match will not be encrypted. From the point of view of ASA1, the matched traffic is any packet that has a source IP in the 192.168.1.0/24 network and a destination IP in the 192.168.2.0/24 network. From the point of view of ASA2, it is the other way around.
I hope this has been helpful!
Laz
Hi Laz,
Thank you for your detailed explanation.
‘From the point of view of ASA1, the matched traffic is any packet that has a source IP in the 192.168.1.0/24 network and a destination IP in the 192.168.2.0/24 network.’
Can I interpret in this way?
Any traffic matched source IP in the 192.168.1.0/24 network and a destination IP in the 192.168.2.0/24 network is permitted to enter the specific interface.
When ASA2 sending packets to ASA1, the destination IP for that packet will be ASA1.
When that packet enter ASA1, shouldn’t it be blocked because it does not match source IP in the 192.168.1.0/24 network and a destination IP in the 192.168.2.0/24?
Apologies for so many questions but I am trying very hard to understand the access list.
Hello PO
No need to apologize for asking questions. You’re here to ask them, we’re here to answer them!
![]()
First of all, keep in mind that this access list is not filtering traffic. It is not permitting or denying traffic from entering or exiting an interface. Indeed it is not even applied to an interface. The access list is defining what traffic will be encrypted. Note that it is applied within the crypto map with the following command:
ASA1(config)# crypto map MY_CRYPTO_MAP 1 match address LAN1_LAN2
The match keyword is enlightening because tells us that this access list is used to match traffic. So, any traffic that has a source IP address in the network of 192.168.1.0/24 and a destination IP address in the network 192.168.1.0/24 is matched and is thus encrypted.
Anything that doesn’t match is not encrypted. It is not blocked, it is simply not encrypted.
Note that what I described is for traffic exiting ASA1. The counterpart access list that matches traffic for encryption in the other direction, is found on ASA2 and has the networks swapped.
I hope this has been helpful!
Laz
Hi Laz,
Thanks again for the explanation.
Now I understand that access list,LAN1_LAN2, is for encryption because it is being used in crypto map.
Could you slightly explain traffic filtering for access list?
ASA1(config)# access-list LAN1_LAN2 extended permit ip 192.168.1.0 255.255.255.0 192.168.2.0 255.255.255.0
If I apply LAN1_LAN2 to interface, this list will filter the traffic right?
Am I correct if I interpret as follow?
Any traffic matched source IP in the 192.168.1.0/24 network and a destination IP in the 192.168.2.0/24 network is permitted to enter the specific interface.
Hello Po
The access list LAN1_LAN2 could be applied to a particular interface to filter traffic. First off, we must clarify that this is an extended access list, which means that it matches both source and destination IP addresses to apply the action of permit or deny. So if you were to apply LAN1_LAN2 outbound on an interface, then the following would be checked:
Each packet exiting this particular interface would have its source and destination addresses compared to the source and destination addresses in the access list. If BOTH source and destination match, then the packet would be permitted. If either one or both do not match, the packet would be denied due to the explicit deny any any at the end of each access list.
For more information on extended access lists take a look at the following lesson:
I hope this has been helpful!
Laz
Hi Laz,
Great explanation! Thank you so much for such detailed information.
I have few questions regarding the following statements from this chapter.
The ASA’s order of operation is that it first translates a packet with NAT, then checks if the packet should be encrypted or not. This packet doesn’t match our LAN1_LAN2 access-list, so it won’t be encrypted.
What happened if packets are not encrypted? Will they be dropped automatically?
ASA2 drops the packet because no access-list permits traffic from the outside to the inside.
If we have the access-list to permit traffic from the outside to the inside, does that mean we don’t have to use NAT exemption?