Hello José
Wow, that’s a lot of questions! I will do my best to address them.
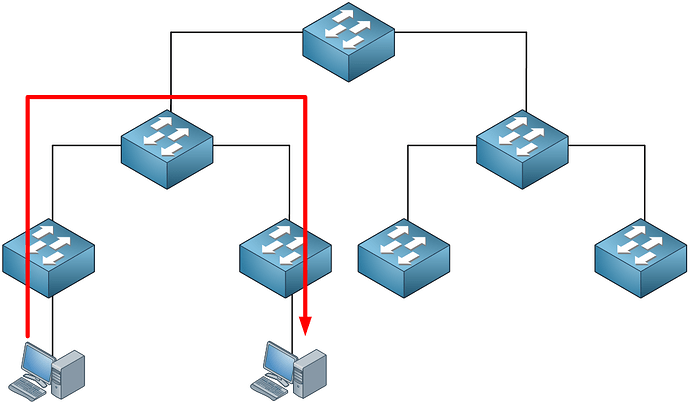
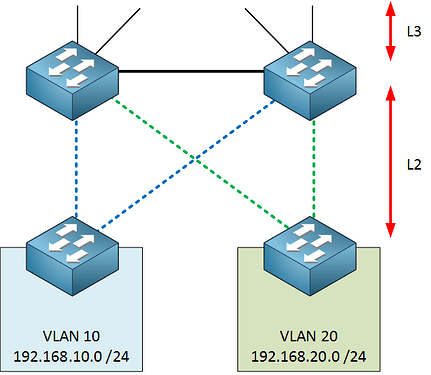
If the VLAN exists on two different switch blocks then yes, you must ensure that you have Layer 2 connectivity across the core devices. However, it is best practice to try to keep VLANs contained within each switch block so that the core performs only routing.
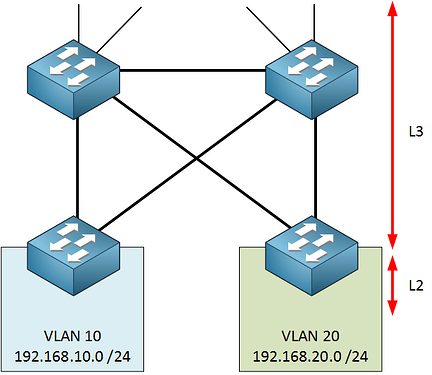
It depends on your design. Best practice dictates that the core should perform routing between switch blocks. If the core devices are L3 switches, which they typically are, then you would create SVIs with IP addresses to act as the next hop IPs or default gateways. If they’re routers, then each interface would have its own IP address to act as the gateway/next hop. Some routing would also take place at the distribution layer to avoid having intra-block traffic go to the core and come back.
If that were the case, traffic between subnets would be routed at the access layer. Such traffic would not reach the distribution or core layers at all.
Yes
Typically you would add another switchblock and call it “network edge” where the edge equipment would be (edge router, firewall, IDS, IPS etc) to connect to the “outside world” either to the Internet or via MPLS to remote sites.
See answer above.
Yes that can happen, but it is best practice not to span VLANs across campuses. VLANs should not be spanned across switch blocks if at all possible. You should have only routing across any tunnels you create or across MPLS.
Layer 3 switches are preferable because you can create as many SVIs as you like to serve each individual subnet in your topology, where using a router, you are limited by the physical interfaces that exist on the device.
This design is for any enterprise network that is generally large. Whether it is in one large building or in several buildings on a campus makes no difference. For branch office networks, it all depends upon the size. If they’re large enough they too should conform to these campus network design principles.
VSS will indeed negate the need for FHRP and STP however, it has limitations. VSS can only connect two core devices and is supported only on the older catalyst 6500 and 4500 series switches. A better alternative is to use either Stackwise Virtual or a more traditional FHRP arrangement. Still other options include the use of a spine and leaf architecture, but those are more often used in data centers, although not exclusively so.
I hope this has been helpful!
Laz