This topic is to discuss the following lesson:
How is easy vpn different from GETVPN?
Hi Edwin,
Normally when you configure IPsec you have to configure security parameters (ESP/AH, DH, encryption algorithm, etc.) on both endpoints. Easy VPN is useful for remote workers so you don’t have to configure all these parameters on the client side. These VPN connections are all point-to-point.
Now imagine you have a large company with a HQ and multiple branch offices. All branch offices should be connected to the HQ and there should be some direct branch-to-branch VPNs. In this case, you really don’t want to configure dozens of these point-to-point VPNs which is why we have technology like DMVPN which uses point-to-multipoint tunnels.
I would recommend to read up a bit on DMVPN if you haven’t seen this before:
Everything I described above has one thing in common…we use “tunnels” to “bridge” networks together. This allows connectivity between networks with private addresses.
Now let’s say we have that large company with its multiple branch offices and everything is connected the way it should. Branch offices can reach each other directly, they can all reach the HQ etc. For now it doesn’t matter what we used…it could be MPLS VPN or DMVPN and we are not using any IPsec at all.
We want to make sure that all our traffic is protected through IPsec and we want to centralize this…
GETVPN uses a key server (a central router) which takes care of all keys and it can distribute security policies. Other routers are called group members and once authenticated by the key server, they belong to the group and they can securely communicate with other group members.
The original IP header is used which is why you already need to have connectivity through a private network like MPLS VPN or DMVPN.
So the short version…with GETVPN we have a bunch of routers that are already connected somehow. We use a central key server and all other routers are group members. Group members authenticate to the key server which takes care of keying/policies. Once you belong to the group, traffic is protected with IPsec. It only takes care of “protecting” your traffic which is why you need a private network like MPLS VPN or DMVPN (or anything else).
I hope this helps, if not let me know.
Rene
Hi,
can you make an example using PPTP?
Also let`s say that we have NAT and we are connecting using PPPoE, but on internal LAN we have some servers we want to access from outside, we need to implement static routing?
Thank you
Hi Rene,
How can i use the Easy VPN to tunnel all the traffic from the client PC, not just to reach remote networks?
Especially when VPN router is doing NATing as well.
Traffic will enter and leave the same interface like Hairpin.
Regards,
Bandu
Hi Bandu,
By default, all traffic will be tunneled unless you configure split tunneling.
Rene
Hi Rene,
can you provide a scenario of site to site VPN using Easy VPN? thanks
Hany
Hello Hany.
I have set up a site to site VPN using Easy VPN in a production environment.
Easy VPN for a site to site VPN is created using Cisco Configuration Professional GUI for Cisco routers. You connect to both the VPN server and the VPN client routers individually and enter commands using the wizards provided. You can find out more about creating a site to site VPN with Easy VPN on CCP here.
The configuration I implemented required a group of 7 PCs at a remote site to connect to internal network resources (finance server and internal email) at company headquarters. I created a VPN server using Easy VPN at the head office location. Using an ADSL connection at the remote site, I used Easy VPN to configure the client ADSL router. The result was that the seven PCs were connected to an internal subnet of headquarters such that their communication with the rest of the network was as if they were physically located within the company WAN.
I hope this has been helpful.
Laz
Hi Laz,
Can you post the configuration as it shows up in the CLI of the central and remote sites?
Thanks
Hany
Hello Hany
Here’s an excerpt from the client side VPN router, that is, the ADSL router at the remote site. Of course it has been sanitised…
!
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname XXXXXX
!
boot-start-marker
boot-end-marker
!
logging buffered 52000
enable secret 5 XXXXXXXX
!
aaa new-model
!
!
aaa authentication login default local
aaa authorization exec default local
!
!
aaa session-id common
clock timezone PCTime 2
clock summer-time PCTime date Mar 30 2003 3:00 Oct 26 2003 4:00
!
crypto pki trustpoint TP-self-signed-3860321116
enrollment selfsigned
subject-name cn=IOS-Self-Signed-Certificate-3860321116
revocation-check none
rsakeypair TP-self-signed-3860321116
!
!
crypto pki certificate chain TP-self-signed-3860321116
certificate self-signed 01
XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
quit
dot11 syslog
ip cef
!
!
no ip dhcp use vrf connected
ip dhcp excluded-address 10.96.1.73 10.96.1.74
!
ip dhcp pool sdm-pool
import all
network 10.96.1.72 255.255.255.248
default-router 10.96.1.73
dns-server 10.96.0.66 XXXXXXXXXX
!
!
ip domain name XXXXXXXXX.com
ip name-server XXXXXXXXX
ip name-server 10.96.0.66
!
multilink bundle-name authenticated
!
!
username name privilege 15 secret 5 XXXXXXXXXXXXXXXXXXXXXXX
username name2 privilege 15 secret 5 XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
!
!
!
!
!
!
crypto ipsec client ezvpn SDM_EZVPN_CLIENT_1
connect auto
group VPN_Group key XXXXXXX
mode network-extension
peer 10.96.0.15
peer 10.96.0.13
virtual-interface 2
username name password XXXXXXXXXXXXXXX
xauth userid mode local
!
!
archive
log config
hidekeys
!
!
!
!
!
interface BRI0
no ip address
encapsulation hdlc
shutdown
!
interface ATM0
no ip address
no atm ilmi-keepalive
dsl operating-mode auto
!
interface ATM0.4 point-to-point
pvc 8/35
encapsulation aal5mux ppp dialer
dialer pool-member 1
!
!
interface FastEthernet0
!
interface FastEthernet1
!
interface FastEthernet2
!
interface FastEthernet3
!
interface Virtual-Template2 type tunnel
no ip address
tunnel mode ipsec ipv4
!
interface Vlan1
description $ETH-SW-LAUNCH$$INTF-INFO-HWIC 4ESW$
ip address 10.96.1.73 255.255.255.248
ip nat inside
ip virtual-reassembly
ip tcp adjust-mss 1412
crypto ipsec client ezvpn SDM_EZVPN_CLIENT_1 inside
!
interface Dialer3
ip address negotiated
ip nat outside
ip virtual-reassembly
encapsulation ppp
dialer pool 1
dialer-group 1
no cdp enable
ppp authentication chap callin
ppp chap hostname XXXXXXXXXXXXXXXXXXXXXXXXXX
ppp chap password 0 XXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
crypto ipsec client ezvpn SDM_EZVPN_CLIENT_1
!
ip forward-protocol nd
ip route 0.0.0.0 0.0.0.0 Dialer3 2
!
!
ip http server
ip http access-class 23
ip http authentication local
ip http secure-server
ip http timeout-policy idle 60 life 86400 requests 10000
ip dns server
ip nat inside source list 1 interface Dialer3 overload
!
access-list 1 remark INSIDE_IF=Vlan1
access-list 1 remark SDM_ACL Category=2
access-list 1 permit 10.96.1.72 0.0.0.7
access-list 101 permit ip any 10.0.0.0 0.255.255.255
access-list 101 deny ip any any
dialer-list 1 protocol ip permit
snmp-server community XXXXXXXX RO
no cdp run
!
!
!
!
control-plane
!
banner login C----------------------------------------------------------------
XXXXXXXXXXXXXXXXXXXX
-----------------------------------------------------------------------
!
line con 0
no modem enable
line aux 0
line vty 0 4
privilege level 15
transport input telnet ssh
!
scheduler max-task-time 5000
end
I was unable to get access to the VPN server today, but when I do I will post that as well.
I hope this has been helpful!
Laz
Thanks Laz. very helpful
Hi Rene,
Can you please give an example of using IKEv2 instead of IKEv1 ??
Hello Hussein
Until @ReneMolenaar creates a lesson that shows the differences in implementation of IKEv1 and IKEv2 on Cisco devices, take a look at this Cisco Documentation that compares configs for IKEv1 and IKEv2 on Cisco IOS devices. The connections in each case are made with strongSwan devices, but you can see the differences in the configs on the IOS side of the connections.
I hope this has been helpful!
Laz
Thanks for answer Laz
I will definitely be excited to this lesson, but for now I want only to know how to connect VPN from my win 10 to the router using IKEv2 ?? because cisco VPN client is end of sales and not used these days !!
Hi,
thank for the lesson. please can you check why this image is not displaying in the article ?
B.R
Hello Thierry
Thanks for letting us know. We’ll get it fixed ASAP.
Laz
Thank you Thierry, I just fixed this image.
Rene
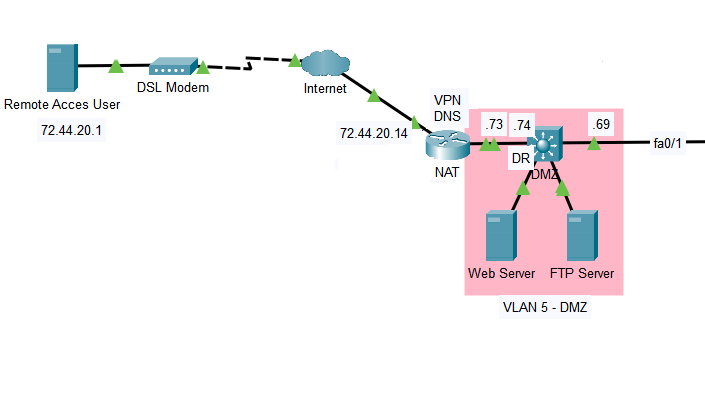
Hi, I have an accessabilty issue with a remote access VPN connection.
The remote access user can http and ftp to the Web server & FTP server, but when the remote access user connects to the VPN on the router at 72.44.20.14,
it cannot access the Web server or FTP Server. It can ping 192.168.100.73, but not .74. The Web Server IP address is 192.168.5.5 /29
I am not sure if I have to configure an access list to allow HTTP, FTP, & SSH traffic through the VPN, or if there is something else thats needs to be configured.
This is the config I have:
VPN / NAT ROUTER
int fa0/0
ip address 192.168.100.13 255.255.255.252
exit
!
int fa0/1
ip address 192.168.100.70 255.255.255.252
exit
!
int fa1/0
ip address 192.168.100.5 255.255.255.252
exit
!
int fa1/1
ip address 192.168.100.1 255.255.255.252
exit
!
int lo1
description REMOTE ACCESS TO R1
ip address 1.1.1.1 255.255.255.255
exit
!
!
aaa new-model
aaa authentication login REMOTE local
aaa authorization network REMOTE local
!
username xxxx secret xxxx
!
crypto isakmp policy 10
encryption aes 256
hash md5
authentication pre-share
group 2
lifetime 21600
exit
!
crypto isakmp client configuration group REMOTE
key CISCO
pool VPN-POOL
!
ip local pool VPN-POOL 192.168.5.1 192.168.5.10
!
crypto ipsec transform-set VPN-SET esp-aes 256 esp-md5-hmac
!
crypto dynamic-map VPN-MAP 10
set transform-set VPN-SET
reverse-route
exit
!
crypto map CLIENT-MAP client authentication list REMOTE
crypto map CLIENT-MAP isakmp authorization list REMOTE
crypto map CLIENT-MAP client configuration address respond
crypto map CLIENT-MAP 10 ipsec-isakmp dynamic VPN-MAP
!
int fa0/0
crypto map CLIENT-MAP
!
ip route 0.0.0.0 0.0.0.0 FastEthernet0/0
!
router ospf 1
router-id 100.1.1.1
network 1.1.1.1 0.0.0.0 area 0
network 192.168.100.1 0.0.0.0 area 0
network 192.168.100.5 0.0.0.0 area 0
network 192.168.100.13 0.0.0.0 area 0
network 192.168.100.70 0.0.0.0 area 0
!
auto-cost reference-bandwidth 100
!
ip nat inside source list NAT-TRANSLATIONS interface FastEthernet0/0 overload
!
ip nat inside source static tcp 192.168.5.5 80 72.44.20.14 80
ip nat inside source static tcp 192.168.5.5 443 72.44.20.14 443
ip nat inside source static tcp 192.168.5.5 80 72.44.30.14 80
ip nat inside source static tcp 192.168.5.5 443 72.44.30.14 443
ip nat inside source static tcp 192.168.5.6 20 72.44.20.14 20
ip nat inside source static tcp 192.168.5.6 21 72.44.20.14 21
DMZ Switch
ip routing
!
vlan 200
name SSH-TO-DMZ-VPN-NAT-SWITCH
!
interface Vlan200
ip address 192.168.200.41 255.255.255.248
!
vlan 5
name DMZ_VLAN
!
int vlan 5
ip address 192.168.5.1 255.255.255.248
!
int range fa0/5 - 6
switchport mode access
switchport access vlan 5
!
int fa0/1
no switchport
ip address 192.168.100.69 255.255.255.252
!
int fa0/24
no switchport
ip address 192.168.100.74 255.255.255.252
!
int lo1
description REMOTE-ACCESS-TO-L3-DMZ-SW
ip address 66.66.66.66 255.255.255.255
exit
!
ip route 0.0.0.0 0.0.0.0 192.168.100.73
!
router ospf 1
router-id 200.6.6.6
network 66.66.66.66 0.0.0.0 area 0
network 192.168.200.41 0.0.0.0 area 0
network 192.168.5.0 0.0.0.255 area 0
network 192.168.100.69 0.0.0.0 area 0
network 192.168.100.74 0.0.0.0 area 0
Hello Dinesh.
One thing you might want to look at is to see if it is a routing issue. What internal IP address is the host getting? If it can ping .73 which is on the NAT router, but not .74, it gives me the impression that .74 doesn’t know where to respond to the ping. That’s the first thing I would check.
Take a look and let us know so that if needed, we can continue to help with the troubleshooting.
I hope this has been helpful!
Laz
(post withdrawn by author, will be automatically deleted in 24 hours unless flagged)