This topic is to discuss the following lesson:
Hi,
Can you explain the below with examples
“You can use 802.1Q VLAN tags for multiple virtual interfaces. This allows you to use one VLAN to access public services like S3 with public IP addresses, and another VLAN for private resources like EC2 instances with private IP addresses.”
Thanks
Hi,
Cloud vendors use the term L2 connectivity and L3 connectivity
What actually mean by this
What a cloud provider says we support only L2 connectivity ?
Hello Sims,
This is from the AWS Direct Connect documentation:
AWS Direct Connect lets you establish a dedicated network connection between your network and one of the AWS Direct Connect locations. Using industry standard 802.1Q virtual LANS (VLANs), this dedicated connection can be partitioned into multiple virtual interfaces. This allows you to use the same connection to access public resources, such as objects stored in Amazon S3 using public IP address space, and private resources such as EC2 instances running within a VPC using private IP address space, while maintaining network separation between the public and private environments. Virtual interfaces can be reconfigured at any time to meet your changing needs.
AWS uses Virtual Private Cloud (VPC). In a nutshell, this is a virtual network where you configure routing, subnets, etc.
You can create a single VPC where you run all your EC2 instances (virtual machines) and RDS instances (databases) etc, or you can create multiple VPCs and isolate your network resources.
AWS Direct Connect is a L2 trunk which uses 802.1Q so it supports VLANs.
For each VPC, you can use a different VLAN on your L2 trunk. This way, your VPCs remain isolated even when they are connected to your site over the L2 trunk.
A L2 connection usually means it’s an Ethernet based connection so you can use 802.1Q and VLANs. With L3, it’s a routed connection..no 802.1Q and VLANs.
Does this help?
Rene
Hi,
I understand “A L2 connection usually means it’s an Ethernet based connection so you can use 802.1Q and VLANs. With L3, it’s a routed connection…no 802.1Q and VLANs.”
My question is what if they offer only l2 connectivity to a customer .
What is the pros and cons if they provide only l2 connectivity and what is the pros and cons if they also providing l3 connectivity
Thanks
To clear up possible misunderstanding… 802.1q and VLANs can be used with L3 routed connections (see below). The way to understand this is when a frame arrives on a subinterface, the physical interface receives the frame and reads the 802.1q tag to determine which subinterface to direct the frame for processing. Return traffic gets encapsulated in an L2 frame with an 802.1q tag (in the example below the tag = 100). If the frame doesn’t have a tag, then it’s processed by the main physical interface.
interface gi 0/0/0
no ip address
!
interface go 0/0/0.100
encapsulation dot1q 100
ip address 10.1.100.1 255.255.255.0
A layer 2 connection, like a VPLS (ENS for Comcast or ACE for AT&T) is basically the ISP offering you a virtual switch to plug into between your sites (or the cloud) meaning all devices that have circuits terminating on that virtual switch (the VPLS) can talk to each other over layer 2. For instance, your devices may see each other through CDP. Some ISPs charge extra to pass CDP, but the principle is the same.
Of course a circuit doesn’t need to be a VPLS to offer L2 connectivity, that’s just one example. A circuit could be a point-to-point and also offer L2 reachability. That said, you’re not going to get traffic beyond a L3 hop (like a router) without an IP address.
A L3 circuit usually means you’re peering at L3 with the ISP. Your router connects usually via a dynamic routing protocol (BGP, EIGRP, etc…) to the ISP router. They take whatever advertised routes/prefixes you advertise and pass it to the other end of the circuit, where there’s another ISP router that peers with your far end router, again over L3 and passes the traffic.
The advantage of an L2 circuit is that you don’t need to interact with the ISP to connect your A-side and Z-side devices. The ISP turns up the circuit, you accept it, then you configure each end(s) and you’re done. The other advantage is that you don’t consume additional IP space peering with an ISP, though ISPs can offer public IPs to peer with even though the connection remains private.
Thanks alias,
Recently i saw cloud provider says they provide only l2 connectivity .
What I cannot do If I subscribe from them
Thanks again
You’re not limited by accepting an L2 connection. It’s just a different way of delivery end-to-end connectivity. In the end, circuits deliver connectivity between different locations - both L2 and L3 circuits perform this. The question really is, how to you want to this?
Personally I prefer L2 circuits because it allows me to control the L3 of the circuit termination points (your routers). If your ISP passes CDP, then you can even see your far end device.
The bigger question concerns whether your circuit is a point-to-point or virtual ethernet switch (VPLS).
Hi,
“Personally I prefer L2 circuits because it allows me to control the L3 of the circuit termination points (your routers)”
You mean you will do a vpn for L3?
Thanks
Hi Guys,
I saw that ENARSI blueprint at NetworkLessons course does not have the topic "Troubleshoot network problems using Cisco DNA Center assurance )connectivity, monitoring, device health, network health), covered in the exam Blueprint issued by Cisco.
I’m really working hard to take the exam this month, so I’d like to know when you will update new topic into the course or if you already have it, please send me the link, I’ll appriciate that.
Regards.
Hello Luis
You can find information about DNA in the following lesson:
I hope this has been helpful!
Laz
Hi Lazaros,
Ok, but it does not have the Assurance Topic explaining how to Troubleshooting, It explains about Cloud Connectivity, but it is not part of the Cisco’s ENARSI Blueprint.
Could you please check it again?
Thanks.
Hi Luis,
I’ll take a look and update it so it matches the blueprint topic.
Rene
Hi
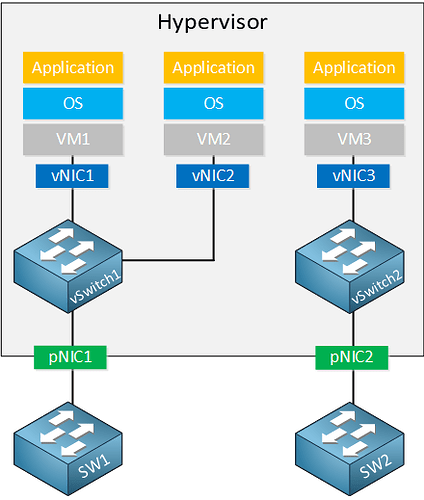
How does sw1(or sw2) forward L2 frame from VM1 to VM3 ? They have learned virtual MAC addresses(vMAC) of all VMs ?
Both vSwitch and physical switch learn vMAC of all VMs ?
There are so many VMs in one rack. Should ToR switch learn all the vMAC of VMs ?
Thanks
Michael
Hello Michael
This particular diagram is used to show the logic behind the creation of vSwitches. In this particular case, VM1 cannot communicate with VM3. You need some L2 connection (either virtual or physical) between those network segments for connectivity.
If all VMs and both the vSwitches, and the physical switches are on the same subnet, then yes, they will all learn the MAC addresses, just like they would if they were all physical devices involved.
It is for this reason that there are other options you can use to design a datacenter to reduce the number of MAC addresses that must be learned. These include the introduction of routing so that you have smaller subnets, and smaller MAC address tables, or the use of other features such as VXLANs which allow you to overcome limitations involving STP, limited number of VLANs, and large MAC address tables.
I hope this has been helpful!
Laz
Hello,
I do not see the interest of having virtual switches (vSwitch) on a network ![]() but I see the interest of VM & container when it is a server
but I see the interest of VM & container when it is a server
in a company when we create a VM with a Vnet (virtual network card) the service works.
Could you explain to me please?
In what kind of architecture do we apply that
the objective of the switch is to be an intermediate physical device to ensure L2 continuity and the possibility of separating vlan
A VM is on a physical server which must already have continuity.
Thank you for your explanation.
Hello Brahim
Virtual switching is necessary when you want your multiple virtual devices to communicate with each other. If you have several VMs within a Hypervisor or several containers within a docker, and you want them to communicate, you shouldn’t need to provide a physical switch for this. Otherwise, you would have packets exiting the hypervisor, going to a physical switch, being switched, and being sent back into the hypervisor. This is something that will actually slow down the network, and also requires additional hardware that costs money.
By creating a virtual switch, you can have packets exchanged between VMs internally, thus making the network faster, and not requiring additional hardware.
Keep in mind that you wouldn’t provision a vSwitch for physical devices, it simply wouldn’t make sense. The point is to create a virtual network environment for your virtual entities (VMs or containers) so that they can effectively communicate.
I hope this has been helpful!
Laz
Hi Rene/LaZ,
please explain Rest API in detail.
Thanks,
Ajay M
Hello Ajay
Take a look at this lesson:
Once you review it, if you have any more specific questions, feel free to ask!
I hope this has been helpful!
Laz
Hi Laz/Rene,
can you please give us more details , how Docker uses Iptables and NAT to forward ports from the outside physical interface to the vEth interface.
if you explain this with a configuration example then it would be really helpful.
BR//AM