Hi Lazaros,
I am still a little confused. I tried using packet tracer to test the configs but it is buggy, so based on my current network the commands and ports should be as follows for dhcp snooping and dai:
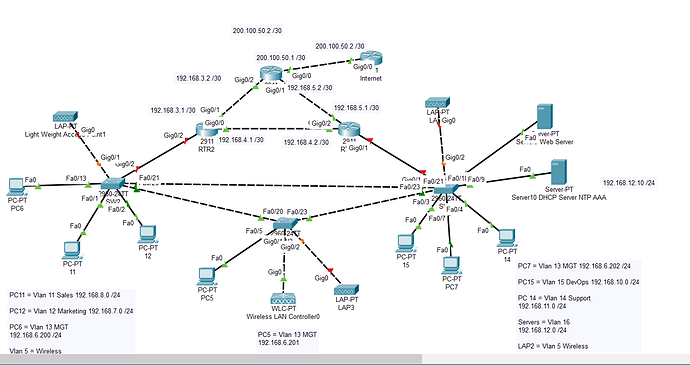
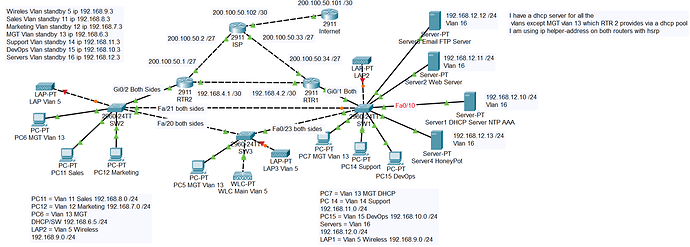
SW2:
config>
ip dhcp snooping
no ip dhcp snooping information option
ip dhcp snooping vlan 5-13
(I have the other vlans active on far right switch SW1 should I put all vlans on network in general under this command? = vlan 5-16)
int gi0/2> ip dhcp snooping trust
(because I have a dhcp pool and router on a stick comming from here with dhcp relay for vlans on the far right network)
int range fa0/20-21> ip dhcp snooping trust
(the two ports connected to trunks on switch two)
SW3
Config>
ip dhcp snooping
no ip dhcp snooping information option
ip dhcp snooping vlan 5, 13
**int fa0/23**> ip dhcp snooping trust
(on port connected to switch 3)
SW1
ip dhcp snooping
no ip dhcp snooping information option
ip dhcp snooping vlan 5, 13, 14, 15, 16
(Like above, not sure here if I need to include vlans that exist on other side of network on SW2 like vlans 11 and 12 even if they arent being used in active ports on this switch as I do have hsrp enable?)
int gi0/1>ip dhcp snooping trust
(Should I also put on this port link to router because I have MGT vlan 13 pool coming from RTR2 on left?)
int fa0/10> ip dhcp snooping trust
RTR2
Config> ip dhcp relay information trust-all
(I have to enact this command on my router because I have ip helper-addresses for my vlans to the server right? Is there anything else I need to command on the routers for dhcp snooping or dai for my network?)
RTR1
Config> ip dhcp relay information trust-all
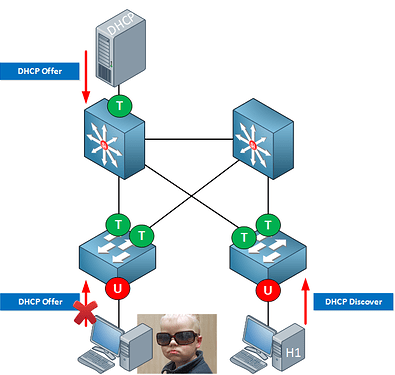
DAI
SW2
Config> ip arp inspection vlan 5-13
int gi0/2 >ip arp inspection trust
int range fa0/20-21> ip arp inspection trust
SW3
Config> ip arp inspection vlan 5, 13
int fa0/23>ip arp inspection trust
SW1
Config>ip arp inspection vlan 5, 13, 14, 15, 16
int gi0/1>ip arp inspection trust
int fa0/10>ip arp inspection trust