I was so confused by this at first. I know its simple but its also a brain teaser for some reason.
first I pulled up my boson subnet tool its free tool by the way on the Boson.com (just need to create an account) website. At first I was thinking that first two bits mean the first two spots _ _ thinking it could be anything from 0 to 192 that it did not matter if it was a zero or a one. However after putting into the subnet calculator it helped me to see.
The next really helpful thing for me was when I went ahead and enabled the command with distribute-list prefix CLASSB in all of a sudden all my 10.x.x.x networks disappeared which shot my first theory to crap along with supporting the boson subnet calculator.
So seeing it in play in a lab really made sense. I think the confusion goes back to the rule on how the classes are setup. When we was learning sub-netting classes that you read and say oh ok but as time goes on you just get use to seeing the numbers themselves and that they are a certain class.
I am betting everyone that had a problem with this does not use the Class A, B, C rule anymore but instead over time have subconsciously just memorized the 1-127 is A, 128-191 is B, 192-223 is C and does not really think of the rule about class A the first bit always being 0, and class b the first two bits being set to 10, and class C having its first three bits set to 110… (hoping me explaining this in writing will actually help me remember it! lol)
So its like trying to do a math problem and finally that silly rule in math never used much is key to how the expression functions.
anyway below is some more information reinforcing Rene info.
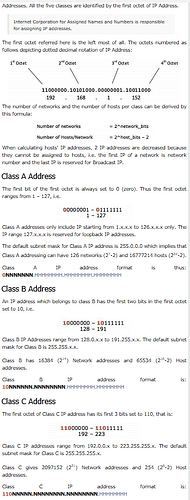
posted the rule below in greater detail that Rene implicitly mentioned briefly in his post I am one of those type that can sometimes be slow seeing something the way it should be seen until I experience it for myself.
https://www.tutorialspoint.com/ipv4/ipv4_address_classes.htm