This topic is to discuss the following lesson:
Hello Rene.
Fantastic lesson. I have some doubts about NAT like the one described below using your example:
When a ping is done from the NAT server to the Webserver there is a failure.
Logs from NAT are reporting this:
NAT#ping 192.168.23.3
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.23.3, timeout is 2 seconds:
*Mar 1 00:12:43.191: IP: tableid=0, s=192.168.23.2 (local), d=192.168.23.3 (FastEthernet0/1), routed via FIB
*Mar 1 00:12:43.191: IP: s=192.168.23.2 (local), d=192.168.23.3 (FastEthernet0/1), len 100, sending
*Mar 1 00:12:43.279: NAT*: s=192.168.23.3, d=192.168.23.2->192.168.12.1 [41].
*Mar 1 00:12:45.187: IP: tableid=0, s=192.168.23.2 (local), d=192.168.23.3 (FastEthernet0/1), routed via FIB
*Mar 1 00:12:45.187: IP: s=192.168.23.2 (local), d=192.168.23.3 (FastEthernet0/1), len 100, sending
*Mar 1 00:12:45.219: NAT*: s=192.168.23.3, d=192.168.23.2->192.168.12.1 [42].
*Mar 1 00:12:47.059: NAT: expiring 192.168.23.2 (192.168.12.1) icmp 10 (10)
*Mar 1 00:12:47.187: IP: tableid=0, s=192.168.23.2 (local), d=192.168.23.3 (FastEthernet0/1), routed via FIB
*Mar 1 00:12:47.187: IP: s=192.168.23.2 (local), d=192.168.23.3 (FastEthernet0/1), len 100, sending
*Mar 1 00:12:47.219: NAT*: s=192.168.23.3, d=192.168.23.2->192.168.12.1 [43].
*Mar 1 00:12:49.187: IP: tableid=0, s=192.168.23.2 (local), d=192.168.23.3 (FastEthernet0/1), routed via FIB
*Mar 1 00:12:49.187: IP: s=192.168.23.2 (local), d=192.168.23.3 (FastEthernet0/1), len 100, sending
*Mar 1 00:12:49.219: NAT*: s=192.168.23.3, d=192.168.23.2->192.168.12.1 [44].
*Mar 1 00:12:51.155: NAT: expiring 192.168.23.2 (192.168.12.1) icmp 11 (11)
*Mar 1 00:12:51.187: IP: tableid=0, s=192.168.23.2 (local), d=192.168.23.3 (FastEthernet0/1), routed via FIB
*Mar 1 00:12:51.187: IP: s=192.168.23.2 (local), d=192.168.23.3 (FastEthernet0/1), len 100, sending
*Mar 1 00:12:51.219: NAT*: s=192.168.23.3, d=192.168.23.2->192.168.12.1 [45].
Success rate is 0 percent (0/5)
*Mar 1 00:13:05.491: NAT: expiring 192.168.23.2 (192.168.12.1) icmp 6 (6)
*Mar 1 00:13:05.491: NAT: expiring 192.168.23.2 (192.168.12.1) icmp 4 (4)
*Mar 1 00:13:29.555: NAT: expiring 192.168.23.2 (192.168.12.1) icmp 12 (12)
*Mar 1 00:13:51.571: NAT: expiring 192.168.23.2 (192.168.12.1) icmp 13 (13)
Could you help me to understand more this log ?
Does the Static NAT rule apply to self-genereting traffic ?
Hi Klaus,
It would be easier if I could see the entire config but something to keep in mind is that traffic generated locally on the router that is configured for NAT doesn’t get translated. Packets have to flow through the router…
Rene
Renee
Great lab this one … just out of interest I wanted to see what would happen … (the lab was so succcessful i had to try something to mess it up …) … if I also removed the ip default gateway from the host too (as well as removing the default gateway from the webserver) and it still worked … should this have been the case ? and if so can you explain how the #host (ping) could still get to through to the webserver … jsut curious really if you can have a look
thanks again
Will
NOTE: it worked the (translated) ping after having removed BOTH default gateway commands on BOTH #host and #webserver ![]()
Hi William,
If you used the same topology then you will require a default gateway only on the host and not on the web server anymore. The host will be sending packets to an IP address outside its own subnet but the web server will be communicating with 192.168.23.2 which is on its own subnet.
Rene
Hi Rene,
I have configure nat on router but when i ping from PC1 it is successful but when i do the same from PC3 is not successful. Could you please explained it why this happening. Also can you explain a bit in more details the “ip nat outside source list example pool example” command?
Rene, to allow for more clients in the 192.12.18.0/24 subnet would the following be correct for static NAT?
!
ip nat inside source static 192.168.12.1 192.168.23.2
ip nat inside source static 192.168.12.2 192.168.23.3
ip nat inside source static 192.168.12.3 192.168.23.4
...
!
If so, could you put this into an access-list or object-group with a range statement and refer this to the NAT rule?
Matt.
Hi Matt W,
The reason behind the static NAT is one-to-one map between the private and the public IP.
When you create an access-list for range of IP’s, then when applying the global nat command you won’t be able to specify the outside IP but only the interface or the pool (see below). In this case, if you chose the interface and make it overload than you are doing PAT, and if you use the pool then you are doing dynamic NAT.
Router(config)#ip nat inside source list 1 ?
interface Specify interface for global address
pool Name pool of global addresses
Hope I could answer you.
Hi Rene,
I am confused about the some issue on NAT …
What is the diference between below two command ?
NAT(config)#ip nat inside source static 192.168.12.1 192.168.23.2
NAT(config)#ip nat inside source static tcp 192.168.12.1 80 192.168.23.2 80
and
NAT(config)#ip nat outside source static tcp 192.168.12.1 80 192.168.23.2 80
Please correct me if i am wrong on below command …
- ip nat inside (when traffic flow from Inside to outside/dmz)
- *ip nat outside (when traffic flow from Outside to inside/dmz)
- *ip nat dmz (when traffic flow from dmz to outside/inside)
so IP NAT (inside/outside/dmz) depends on the traffic direction from where to where, right ?
br/
zaman
Hi Zaman,
Indeed NAT can be a confusing topic especially with NAT outisde.
Let me give you a general overview of the difference between IP NAT INSIDE & IP NAT OUTSIDE:
IP NAT INSIDE: It will translate the source packet that is going from the inside to the outside, and it will translate the destination packet that is coming from the outside to the inside. In other word, IP NAT INSIDE perform a translation for the packets coming from inside of our network so from our inside interface.
IP NAT OUTSIDE: It will translate the source packet that is going from the outside to the inside, and it will translate the destination packet that is coming from the inside to the outside. In other word, IP NAT OUTSIDE perform a translation for the packets coming from outside of our network so from our outside interface.
Hope this could help.
Dear Rene/Maher,
Thanks . Please correct me if I dont get you correctly …
IP NAT INSIDE : 1. Source ip will rewrite to inside Global when traffic flow from inside to outside and
2. Destination ip will rewrite when traffic flow from outside to inside.
IP NAT OUTSIDE= 1. Source ip will rewrite when traffic flow from outside to inside and
2. Destination ip will rewrite when traffic flow from inside to outside.
Which situation will we use IP NAT OUTSIDE . Still I am confused , Could you please give some example or write a lessone on it .Thanks in again .
br/
zaman
Hello Mohammad!
The IP NAT INSIDE command indicates that the interface in question is on the inside network. The IP NAT OUTSIDE command indicates that the interface in question is on the ouside network. (I’m sure you got that down, I just want to start from the beginning.) Let’s say the IP address of the inside interface is 10.10.10.1/24 and that of the outside interface is 20.20.20.1/24.
Any traffic that enters the router on the inside interface and exits the router on the outside interface will have the following addresses changed:
Source address will change from 10.10.10.X to 20.20.20.1, destination address will be unchanged where 10.10.10.X is the host on the inside network communicating with the outside world.
Any traffic that enters the router on the outside interface and exits on the inside interface will have the following address changed:
Source address will remain unchanged. Destination address will change from 20.20.20.1 to 10.10.10.X.
So, the purpose of the outside command on an interface is to indicate that this interface is participating in NAT and will have to make the appropriate changes to the source addresses when packets are traversing it.
I hope this has been helpful!
Laz
Hi Rene,
some of our customers use “extendable” at the end of static nat command.
Could you please explain what does it mean?
Thanks
I figured it would be best to answer this with an example. Take a look here:
Hello Laz,
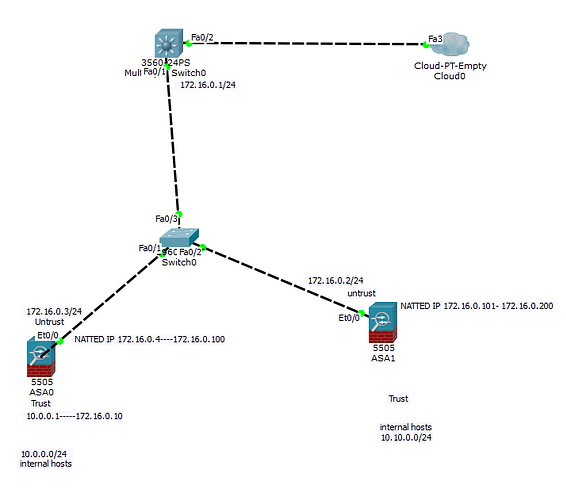
I have a question regarding NAT. I am going to use the below topology for my question.
In this topology, I have a 3560 switch that is acting as my edge device that is connected to the ISP through Fa0/2 interface. Two firewalls and the edge switch are connected to the same segment (172.16.0.0/24) through the Layer 2 switch. The ASA 0 is using 172.16.0.4 - 172.16.0.100 address block as the Natted IPs for some internal hosts that are using 10.0.0.0/24 and ASA1 is using 172.16.0.101- 172.16.0.200 address block as the Natted IP for some other internal hosts that are using 10.10.0.0/24.
Question:
-
Let’s say one of the internal hosts 10.0.0.1 is being natted to 172.16.0.10 on ASA0. When the edge switch sends out an ARP request to get the mac address of 172.168.0.10 IP address, how would ASA0 know it has to respond to the ARP request even though the IP is not attached to any interface? Why would ASA1 not respond to the same ARP request?
-
Can ASA0 and ASA1 both use the same IP address (for instance 172.16.0.10) as a NATTED IP for the internal hosts located behind them on different ports? [for instance, in ASA0 some internal IPs(10.0.0.1-10.0.010) are taking traffic on 172.16.0.10 on port 80 and in ASA1 some internal IPs(10.10.0.1-10.10.0.10) are taking traffic on the same IP 172.16.0.10 on port 443] ?
Thank you so much in advance.
Hello AZM
The ARP request would come from the 3560 router saying “I need the MAC address of the device which has an IP address of 172.16.0.10.” Because ASA0 is configured with the specific NAT configurations, it knows that it must respond to any ARP requests for addresses in the range of 172.16.0.4 to 172.16.0.100. Similarly, ASA1 knows that it is responsible to answer any ARP requests for addresses in the range of 172.16.0.101 to 172.16.0.200. When ASA1 gets the ARP request, it will discard it, while ASA0 will take it and answer with the appropriate MAC address.
No, this is not possible. If you configured both ASAs to NAT the same external IP address, for example, 172.16.0.10, then any ARP request coming from the 3560 for this IP address would be responded to by both ASAs. You would essentially have an IP address conflict on the subnet. In order to have this work, the two ASAs must be differentiated based on Port Number, something that cannot be achieved on layers 2 and 3.
I hope this has been helpful!
Laz
Hi Rene,
Thanks.When we will use “ip nat outside source static tcp 192.168.12.1 80 192.168.23.2 80” command in global configuration mode. Could you please share in which situation we can use it.Actually i didn’t see any scenario where we used “ip nat outside”[It’s Not interface level command but global configuration mode ] command in global configuration mode .
One more questions …
Can we configure NAT on L3 switch in full features and use SVI as inside /outside interface??
br//zaman
Hi @Zaman.rubd
IP nat outside source static translates:
- The source IP address from packets that are sent from the outside to the inside.
- The destination IP address for packets that are sent from the inside to the outside.
One example of how you can use this is if you have overlapping address space. For example, you can configure your router so that whenever a host on the inside sends something to destination 5.5.5.5, it gets translated to 192.168.1.5.
Most Cisco IOS switches don’t support NAT, only the higher end platforms like the 6500 do. Here’s an old document from Cisco that explains which switches support NAT:
Here’s an example from Cisco btw:
http://www.cisco.com/c/en/us/support/docs/ip/network-address-translation-nat/13770-1.html#netdiag