This topic is to discuss the following lesson:
Hey, what is the difference in using route-maps or access-lists or prefixlists when applied to distribute-list ? they all do the same in regards to filtering routes in ospf or eigrp ? are there any minor difference between those ? can you please explain in detail. Thank you.
Hi Sri T,
All three of them will filter routers but there are some big differences…
If you haven’t seen my distribute-list with prefix-list tutorial then take a look at this link:
It will explain the prefix-list in detail.
The route-map is also very powerful…while access-lists and prefix-lists are both used to match on IP addresses or network addresses, route-maps can match on many other things including:
Incoming interface
Next hop IP address
Source of route
Metrics
Route-type (internal / external etc)
Route tags
Rene
Rene , this is wrong lesson link
you have to links referring to the same lesson
this lesson should be for EIGRP filtering with prefix-list
Hi Rene, I have a question regarding recusive routing and the filtering of routing interfaces.
I have a network similar to the one shown in the EIGRP Route-MAP Filtering lesson. The difference I have in my network is that the Tunnel areas has two ASAs so that if the primary route fails routing information can be sent over a tunnel to the remote site via the internet. Routing on this network is provided bt EIGRP. Currently when the primary route fails the link that goes over the internet goes into recursive routing and fails.
interface Tunnel0
ip address 192.168.100.1 255.255.255.0
tunnel source GigabitEthernet2/0.40
tunnel destination 10.164.58.33
!
interface Loopback0
description test interface
ip address 10.164.56.8 255.255.255.255
!
interface FastEthernet0/0
no ip address
shutdown
duplex half
!
interface GigabitEthernet1/0
no ip address
shutdown
negotiation auto
!
interface GigabitEthernet2/0
description SubInterfaced
no ip address
negotiation auto
!
interface GigabitEthernet2/0.20
description Users
encapsulation dot1Q 20
ip address 10.164.57.1 255.255.255.128
no snmp trap link-status
!
interface GigabitEthernet2/0.30
description Servers
encapsulation dot1Q 30
ip address 10.164.56.49 255.255.255.248
no snmp trap link-status
!
interface GigabitEthernet2/0.40
description ASATransit
encapsulation dot1Q 40
ip address 10.164.56.33 255.255.255.248
no snmp trap link-status
!
interface GigabitEthernet2/0.85
description Cloudbridge
encapsulation dot1Q 85
ip address 10.164.56.57 255.255.255.248
no snmp trap link-status
!
interface GigabitEthernet2/0.90
description EntelMPLS
encapsulation dot1Q 90
ip address 192.168.1.252 255.255.255.0
no snmp trap link-status
!
interface GigabitEthernet2/0.360
description NetManagement
encapsulation dot1Q 360
ip address 10.164.56.41 255.255.255.248
no snmp trap link-status
!
interface GigabitEthernet3/0
description OptusTransit
ip address 10.164.56.1 255.255.255.248
negotiation auto
!
interface GigabitEthernet4/0
no ip address
shutdown
negotiation auto
!
interface GigabitEthernet5/0
no ip address
shutdown
negotiation auto
!
interface GigabitEthernet6/0
no ip address
shutdown
negotiation auto
!
router eigrp 10
redistribute connected
redistribute bgp 64973 metric 4000 10 255 1 1476
network 10.1.1.0 0.0.0.3
network 10.164.56.0 0.0.0.7
network 10.164.56.8 0.0.0.7
network 10.164.56.16 0.0.0.7
network 10.164.56.32 0.0.0.7
network 10.164.56.40 0.0.0.7
network 10.164.57.0 0.0.0.127
network 192.168.1.0
network 192.168.100.0
no auto-summary
eigrp router-id 1.1.1.1
neighbor 10.164.56.34 GigabitEthernet2/0.40
neighbor 192.168.100.2 Tunnel0
!
router bgp 64973
no synchronization
bgp log-neighbor-changes
network 10.164.57.128 mask 255.255.255.128
network 10.164.58.6 mask 255.255.255.255
network 10.164.58.32 mask 255.255.255.248
network 10.164.58.48 mask 255.255.255.248
network 10.164.59.0 mask 255.255.255.192
network 192.168.1.254 mask 255.255.255.255
network 192.168.3.1 mask 255.255.255.255
redistribute connected
neighbor 10.164.56.2 remote-as 64972
no auto-summary
!
ip classless
ip route 0.0.0.0 0.0.0.0 10.164.56.34
no ip http server
no ip http secure-server
!
!
!
ip access-list standard NET_192_100
permit 192.168.100.0 0.0.0.255
ip access-list standard NET_56
permit 10.164.56.32 0.0.0.7
!
ip access-list extended WCCP_GRE_Redirect
permit ip any any
ip access-list extended WCCP_Redirect
deny ip 0.0.0.0 255.255.248.0 0.0.0.0 255.255.248.0
permit ip any any
!
logging alarm informational
no cdp log mismatch duplex
!
route-map FILTER_OUT deny 10
match ip address NET_192_100
!
route-map FILTER_OUT permit 20
!
route-map FILT_OUT_56 deny 10
match ip address NET_56
!
route-map FILT_OUT_56 permit 20
!
!
!
!
control-plane
!
!
!
!
!
!
gatekeeper
shutdown
!
!
line con 0
exec-timeout 0 0
privilege level 15
logging synchronous
stopbits 1
line aux 0
exec-timeout 0 0
privilege level 15
logging synchronous
stopbits 1
line vty 0 4
!
!
end
!
interface Tunnel0
ip address 192.168.100.2 255.255.255.0
tunnel source GigabitEthernet2/0.40
tunnel destination 10.164.56.33
!
interface Loopback0
ip address 10.164.58.8 255.255.255.255
!
interface FastEthernet0/0
no ip address
shutdown
duplex half
!
interface GigabitEthernet1/0
no ip address
shutdown
negotiation auto
!
interface GigabitEthernet2/0
description SubInterfaced
no ip address
negotiation auto
!
interface GigabitEthernet2/0.10
description Servers
encapsulation dot1Q 10
ip address 10.164.59.1 255.255.255.192
ip wccp 53 redirect in
ip wccp 54 redirect in
no snmp trap link-status
!
interface GigabitEthernet2/0.20
description Users
encapsulation dot1Q 20
ip address 10.164.57.129 255.255.255.128
ip helper-address 10.164.59.41
ip wccp 53 redirect in
ip wccp 54 redirect in
no snmp trap link-status
!
interface GigabitEthernet2/0.30
description GuestAccess
encapsulation dot1Q 30
ip address 172.16.34.1 255.255.255.128
ip helper-address 10.164.59.41
ip helper-address 10.160.0.40
no snmp trap link-status
!
interface GigabitEthernet2/0.40
description ASAInside
encapsulation dot1Q 40
ip address 10.164.58.33 255.255.255.248
no snmp trap link-status
!
interface GigabitEthernet2/0.85
description Cloudbridge
encapsulation dot1Q 85
ip address 10.164.58.1 255.255.255.248
no snmp trap link-status
!
interface GigabitEthernet2/0.302
description EntelMPLS
encapsulation dot1Q 302
ip address 192.168.3.2 255.255.255.0
ip wccp 51 redirect in
ip wccp 52 redirect in
no snmp trap link-status
!
interface GigabitEthernet3/0
no ip address
shutdown
negotiation auto
!
interface GigabitEthernet4/0
no ip address
shutdown
negotiation auto
!
interface GigabitEthernet5/0
no ip address
shutdown
negotiation auto
!
interface GigabitEthernet6/0
no ip address
shutdown
negotiation auto
!
router eigrp 10
network 10.164.56.66 0.0.0.0
network 10.164.57.128 0.0.0.127
network 10.164.58.1 0.0.0.0
network 10.164.58.8 0.0.0.0
network 10.164.58.32 0.0.0.7
network 10.164.59.1 0.0.0.0
network 192.168.3.0
network 192.168.100.0
distribute-list route-map FILT_OUT_58 out
no auto-summary
eigrp router-id 2.2.2.2
neighbor 10.164.58.34 GigabitEthernet2/0.40
neighbor 192.168.100.1 Tunnel0
!
ip classless
ip route 0.0.0.0 0.0.0.0 10.164.58.34
ip route 10.175.227.0 255.255.255.0 192.168.3.1 2
ip route 10.175.228.0 255.255.255.0 192.168.3.1 2
ip route 172.16.32.0 255.255.255.0 192.168.3.1 2
no ip http server
ip http access-class 20
ip http authentication local
ip http secure-server
ip http timeout-policy idle 60 life 86400 requests 10000
!
!
!
ip access-list standard NET_192_100
permit 192.168.100.0 0.0.0.255
ip access-list standard NET_58
permit 10.164.58.32 0.0.0.7
!
ip access-list extended WCCP_Redirect_LAN_Ingress
deny ip any 10.164.56.0 0.0.7.255 log
permit ip 10.164.56.0 0.0.7.255 10.0.0.0 0.255.255.255 log
ip access-list extended WCCP_Redirect_WAN_Ingress
deny ip 10.164.56.0 0.0.7.255 any log
permit ip 10.0.0.0 0.255.255.255 10.164.56.0 0.0.7.255
!
logging alarm informational
no cdp log mismatch duplex
!
route-map FILTER_OUT deny 10
match ip address NET_192_100
!
route-map FILTER_OUT permit 20
!
route-map FILT_OUT_58 deny 10
match ip address NET_58
!
route-map FILT_OUT_58 permit 20
!
!
!
!
control-plane
!
!
!
!
!
!
gatekeeper
shutdown
!
!
line con 0
exec-timeout 0 0
privilege level 15
logging synchronous
stopbits 1
line aux 0
exec-timeout 0 0
privilege level 15
logging synchronous
stopbits 1
line vty 0 4
!
!
end
AWSANTASA01(config-router)# show run
: Saved
:
: Serial Number: 9ARGJW8UCR7
: Hardware: ASAv, 2048 MB RAM, CPU Pentium II 3465 MHz
:
ASA Version 9.5(2)
!
hostname AWSANTASA01
enable password 8Ry2YjIyt7RRXU24 encrypted
xlate per-session deny tcp any4 any4
xlate per-session deny tcp any4 any6
xlate per-session deny tcp any6 any4
xlate per-session deny tcp any6 any6
xlate per-session deny udp any4 any4 eq domain
xlate per-session deny udp any4 any6 eq domain
xlate per-session deny udp any6 any4 eq domain
xlate per-session deny udp any6 any6 eq domain
names
!
interface GigabitEthernet0/0
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet0/1
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet0/2
nameif INSIDE
security-level 100
ip address 10.164.56.34 255.255.255.248
!
interface GigabitEthernet0/3
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet0/4
nameif OUTSIDE
security-level 0
ip address 200.111.55.138 255.255.255.248
!
interface GigabitEthernet0/5
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet0/6
shutdown
no nameif
no security-level
no ip address
!
interface Management0/0
management-only
shutdown
no nameif
no security-level
no ip address
!
ftp mode passive
access-list LAN1_LAN2 extended permit ip 10.164.56.32 255.255.255.248 10.164.58.32 255.255.255.248
pager lines 23
mtu INSIDE 1500
mtu OUTSIDE 1500
no failover
no monitor-interface service-module
icmp unreachable rate-limit 1 burst-size 1
no asdm history enable
arp timeout 14400
no arp permit-nonconnected
router eigrp 10
eigrp stub connected
neighbor 10.164.56.33 interface INSIDE
network 10.164.32.0 255.255.255.248
network 10.164.56.32 255.255.255.248
redistribute connected
!
route OUTSIDE 0.0.0.0 0.0.0.0 200.111.55.137 2
route OUTSIDE 10.116.58.32 255.255.255.248 186.67.106.90 2
timeout xlate 3:00:00
timeout pat-xlate 0:00:30
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 sctp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
user-identity default-domain LOCAL
http server enable
http 0.0.0.0 0.0.0.0 INSIDE
no snmp-server location
no snmp-server contact
crypto ipsec ikev1 transform-set MY_TRANSFORM_SET esp-aes-256 esp-sha-hmac
crypto ipsec security-association pmtu-aging infinite
crypto map MY_CRYPTO_MAP 10 match address LAN1_LAN2
crypto map MY_CRYPTO_MAP 10 set peer 186.67.106.90
crypto map MY_CRYPTO_MAP 10 set ikev1 transform-set MY_TRANSFORM_SET
crypto map MY_CRYPTO_MAP 10 set security-association lifetime seconds 3600
crypto map MY_CRYPTO_MAP interface OUTSIDE
AWREQASA01# show run
: Saved
:
: Serial Number: 9AGGCHM29TA
: Hardware: ASAv, 2048 MB RAM, CPU Pentium II 3465 MHz
:
ASA Version 9.5(2)
!
hostname AWREQASA01
enable password 8Ry2YjIyt7RRXU24 encrypted
xlate per-session deny tcp any4 any4
xlate per-session deny tcp any4 any6
xlate per-session deny tcp any6 any4
xlate per-session deny tcp any6 any6
xlate per-session deny udp any4 any4 eq domain
xlate per-session deny udp any4 any6 eq domain
xlate per-session deny udp any6 any4 eq domain
xlate per-session deny udp any6 any6 eq domain
names
!
interface GigabitEthernet0/0
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet0/1
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet0/2
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet0/3
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet0/4
nameif OUTSIDE
security-level 0
ip address 186.67.106.90 255.255.255.248
!
interface GigabitEthernet0/5
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet0/6
nameif INSIDE
security-level 100
ip address 10.164.58.34 255.255.255.248
!
interface Management0/0
management-only
shutdown
no nameif
no security-level
no ip address
!
ftp mode passive
access-list LAN2_LAN1 extended permit ip 10.164.58.32 255.255.255.248 10.164.56.32 255.255.255.248
pager lines 23
mtu OUTSIDE 1500
mtu INSIDE 1500
no failover
no monitor-interface service-module
icmp unreachable rate-limit 1 burst-size 1
no asdm history enable
arp timeout 14400
no arp permit-nonconnected
router eigrp 10
neighbor 10.164.58.33 interface INSIDE
network 10.164.58.32 255.255.255.248
!
route OUTSIDE 0.0.0.0 0.0.0.0 186.67.106.89 1
route OUTSIDE 10.164.56.32 255.255.255.248 200.111.55.138 2
route INSIDE 10.164.57.128 255.255.255.128 10.164.58.33 2
timeout xlate 3:00:00
timeout pat-xlate 0:00:30
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 sctp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
user-identity default-domain LOCAL
no snmp-server location
no snmp-server contact
crypto ipsec ikev1 transform-set MY_TRANSFORM_SET esp-aes-256 esp-sha-hmac
crypto ipsec security-association pmtu-aging infinite
crypto map MY_CRYPTO_MAP 10 match address LAN2_LAN1
crypto map MY_CRYPTO_MAP 10 set peer 200.111.55.138
crypto map MY_CRYPTO_MAP 10 set ikev1 transform-set MY_TRANSFORM_SET
crypto map MY_CRYPTO_MAP 10 set security-association lifetime seconds 3600
crypto map MY_CRYPTO_MAP interface OUTSIDE
Hi @Robhorseman101,
The EIGRP route-map filtering lesson only has two routers with a single link so I think you had something else in mind? ![]()
In your config, I see the tunnel interfaces of your routers:
interface Tunnel0
ip address 192.168.100.2 255.255.255.0
tunnel source GigabitEthernet2/0.40
tunnel destination 10.164.56.33
And:
interface Tunnel0
ip address 192.168.100.1 255.255.255.0
tunnel source GigabitEthernet2/0.40
tunnel destination 10.164.58.33
Not sure on which router you get the recursive routing error but for example, if it’s the first one then somehow a more specific route to 10.164.56.33 gets installed through your tunnel interface.
Make sure you filter those so that a route to 10.164.56.33 or 10.164.58.33 is never learned through the tunnel. Look for the networks that are advertised through the tunnel and deny those. If it is learned through EIGRP, you can do something like this:
R1(config)#router eigrp 1
R1(config-router)#distribute-list 1 in tunnel 0
Hope this helps!
Hi Rene,
I had a question on the Design and efficiency portion here.
We can place access-list on “in” or “out” I looked up the following which says standard access list should be placed near destination.
Standard Access Control List (ACL) filters the traffic based on source IP address. Therefore a Standard Access Control List (ACL) must be placed on the router which is near to the destination network/host where it is denied. If we place the Standard Access Control List (ACL) near to source of the traffic, there is a chance for denial or other legitimate traffic from the source network to some other network.
I also looked up the extended:
Extended Access Control List (ACL) can filter the traffic based many factors like source IP address, destination IP address, Protocol, TCP or UDP port numbers etc.
Since an Extended Access Control List (ACL) can filter the IP datagram packet based on the destination IP address, it must be placed on the router which is near to the source network/host. If we place the Extended Access Control List (ACL) near to destination, the unwanted traffic may consume the bandwidth till destination, and the the unwanted traffic will get filtered finally near destination.
However, what is best practice?? what saves the CPU the most work? I mean it almost seems to me if I placed ACL on the source R2 in your example so that it did not have to even send the traffic I save processing on both R2 and R1 which is more efficient.
also since this is only applied to EIGRP it will not effect other traffic anyway. So the rule of the standard acl would not seem to apply here so it seems like you could break that rule for best interest of the efficiency and use a standard.
However, you could use a extended as well here if you wanted. so another question I have in addition to those already asked is does the extended access list cause more work than the standard to the processor?
what is best practice here that will put the least load on our routers?
Also what is best performance and architect wise: distribution ACL, prefix, or route map?
Hello Brian
For access lists it is true that standard should be placed as near to the destination as possible since you are ONLY matching the destination and extended access lists as close as possible to the source since source IP is also taken into account for those. So for PURE access lists, this is the best practice.
The example that Rene has in his lesson does not follow these rules because it is not PURE ACLs that we’re configuring but distribute lists. It is true that if the distribute list was placed on the outbound Fa0/0 interface of R2, the result for the specific topology would be the same, with less overhead. However, it depends on what you want to do.
If you end up placing it on the outbound Fa0/0 interface of R2 then you are suppressing ALL advertisements of the loopback interfaces via Fa0/0. What if there are other routers connected to Fa0/0 and you want those to receive the advertisements but you don’t want R1 to receive them? Then you MUST place the distribution list on the specific router for which you want them to be filtered. There is no point in saving resources if the functionality you need is not provided for.
Yes you could use an extended access list here as well, however, you would still only indicate destination IP addresses. Extended ACLs do use more CPU and resources because they try to match more criteria.
I hope this has been helpful!
Laz
Thanks for answering.
So it seems to me that Best Practice here is just a starting point. Once you get enough knowledge you can be even more efficient depending on the specific design and setup. That was what I was really getting at. I am starting to understand it so my thinking once I have the basic grasp is not held down by specific rules because rules are for the most part general in nature.
I just wanted to ask and confirm that before hand because while what I just stated is logical and common sense if your not careful and don’t ask questions there may be an unknown that can impact and I would hate to pull something into my toobox of knowledge that might be a no no… thank you for helping to setup boundaries so that I know when to follow the boundaries and when to change them to tailor fit something.
when I don’t know how big my world is or the box on a specific item I am generally very cautious until I find the boundaries of my box and then after that point I can use my imagination and creativity to run amuck but only after I have a basic grasp of the foundations and understand the complete system of that box.
So yes that does help a lot! =)
Thanks .Great explanation as always …this has some typo error instead of R2 ,its written R1 in the blogs where as config shared is correct
Hello Vinod
Thanks for the feedback. I’m not sure I see the typo you’re talking about. I looked at both configs and they seem OK. Can you specify the particular location of the error?
Thanks!
Laz
Hi,
I have two routers in AS100. I need to stop exchanging all future and existing external (D EX) routes from these routers. Note that I cannot use access lists, prefix lists or route-maps. any thoughts?
Thanks
Harshan
Hello Sreeharshan
The first thing that comes to mind, after you’ve eliminated the options in your list, is a distribute list. Take a look at this lesson.
I hope this has been helpful!
Laz
How many Distribute List can be applied to a interface ?
Hello Juan
Yes, you can apply multiple distribute lists either to specific interfaces, or to all interfaces. However, the distribute lists will function successively. What does that mean?
Well it means that the distribute lists will be examined in the order that they are configured. For example, if you have configured distribute-lists 1, 3, and 2 in that order, then 1 will be checked first, then distribute-list 3, then 2 and so on, kind of like the statements in an access list. Once a network is denied by a specific distribute list, then checking stops. But if a distribute list does not deny a network, the next list is checked, and the next until either the network is denied or all the distribute lists have been checked.
Now this is the case for either the specific interface that each distribute list is applied to, or if an interface is not specified, it applies to all interfaces.
You can find specific implementations of such distribute lists in the following Cisco documentation:
In this document, the specific algorithm that is used when multiple distribute-lists are implemented is described in detail.
I hope this has been helpful!
Laz
Hi Lazaros,
I created the same distribute-list as in the example, It works well, then I created a second access list and applied to the same Interface, and the results were it applied the last access list, is that how it works?
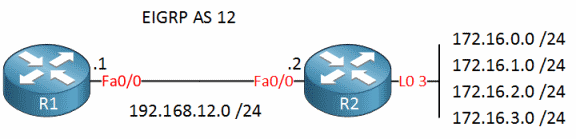
R1#show run | sec eig
router eigrp 12
network 192.168.12.0
distribute-list 2 in FastEthernet0/0
no auto-summary
R1#show access-lists
Standard IP access list 1
10 deny 172.16.1.0, wildcard bits 0.0.0.255
20 permit any
Standard IP access list 2
10 permit 172.16.2.0, wildcard bits 0.0.0.255 (3 matches)
R1#
R1#show ip route eigrp
172.16.0.0/24 is subnetted, 1 subnets
D 172.16.2.0 [90/409600] via 192.168.12.2, 00:02:09, FastEthernet0/0
R1#
Hello Juan
I’m not quite sure I follow what you have done, however, if you issue the following commands in the EIGRP section of the configuration:
distribute-list 2 in FastEthernet0/0
distribute-list 1 in FastEthernet0/0
Then the distribute list using the ACL2 will be checked first, and then the distribute list using ACL1 will be checked, both for the same interface. During those checks, if a match is found, it will apply the action and then stop checking. Both distribute lists will be applied to the interface, in the order configured.
I hope this has been helpful!
Laz
Hello Juan,
You can have two distribute lists tied to interface, one for inbound and one for outbound updates.
Correct, this is how it works in Cisco IOS. You can verify it for example using these commands.
show running-config | section eigrp
show ip protocols
First command tells you what is applied configuration under EIGRP. In your case:
- distribute-list 2 in FastEthernet0/0
Second command is going to list used filtering (including ACL for interface). You should see something like this under EIGRP output in your example.
- FastEthernet0/0 filtered by 2
So far I know, Cisco IOS allows following filtering for each process and each interface:
- 1 incoming distribute list for updates per specific interface
- 1 outgoing distribute list for updates per specific interface
- 1 incoming global distribute list for updates per specific routing process
- 1 outgoing global distribute list for updates per specific routing process
- 1 outgoing redistribution distribute list per process
Different interfaces can use different access-lists.
The way how global distribute-list per direction and distribute-list per interface per same direction inter-operate is very simple. For route to pass, it has to be permitted by both access-lists. Do not forget there is “hidden” deny any for each ACL. This “deny any” is always applied for all routes that are not permitted in the ACL. Route passes only in case its not denied in any specific ACL entry and on top of it cannot be denied by this “hidden” deny any on the end of BOTH access-lists.
Lets make one example. Imagine topology from this lesson.
Configure imaginary ACLs on R1.
access-list 1 permit 172.16.0.0 0.0.0.0
access-list 1 permit 172.16.1.0 0.0.0.0
access-list 2 permit 172.16.1.0 0.0.0.0
access-list 2 permit 172.16.2.0 0.0.0.0
Apply access lists in EIGRP process on R1.
distribute-list 1 in
distribute-list 2 in FastEthernet0/0
With such configuration, you should see only one route 172.16.1.0 on R1. Its the only one that was permitted in both ACLs. What happened to others?
172.16.0.0 – denied by ACL 2 “hidden” deny any
172.16.1.0 – permitted by ACL 1 and ACL 2, thus its the only route that passed.
172.16.2.0 – denied by ACL 1 “hidden” deny any
172.16.3.0 – denied by “hidden” deny any of ACL 1 and ACL 2
The example used within link Laz provided is indeed correct, but can be missleading. There is configuration they used.
access-list 1 permit 1.0.0.0 0.255.255.255
access-list 2 permit 1.2.3.0 0.0.0.255
router rip
distribute-list 2 in ethernet 0
distribute-list 1 in
If we are speaking about route 1.2.3.0, what happens when update with network 1.2.3.0 comes in?
- Its permitted by interface distribute list using ACL 2.
- Its permitted by global distribute list ACL 1, because it falls into range 1.x.x.x
But imagine that ACL is written like this:
access-list 1 permit 1.0.0.0 0.1.255.255
In such case, route 1.2.3.0 would be denied by “hidden” deny any within ACL 1.
Hi,
in your 3rd example you deny the route 1.1.1.0 0.0.0.255 within the ACL. Then you bind the ACL to the route-map inbound filter.
Would the route 1.1.1.0 0.0.0.255 really blocked(from route-map) if it is denied in the ACL.
Also see the discussion in cisco forum:
“If you use an ACL in a route-map permit or deny clause, and the ACL denies a route, then the route-map clause match is not found and the next route-map clause is evaluated.”
In other words: Is there a difference if the IP is permitted or denied within the ACL? Or does route-map only check the IPs that are listet and use its own rules (independent if deny/permit in ACL)?
Sorry, its a bit confusing…
kind regards
Hello Thomas
The way that route maps use access lists and how the permit and deny statements function can get confusing. You can take a look at this lesson that clarifies how these function and interact:
Concerning your specific question, however, this is what takes place:
This is the ACL being used:
R2(config)#ip access-list standard NET_1
R2(config-std-nacl)#deny 1.1.1.0 0.0.0.255
R2(config-std-nacl)#permit any
And here is the route map:
R2(config)#route-map FILTER_IN permit 10
R2(config-route-map)#match ip address NET_1
So what happens is, we look first to see what is permitted in the ACL. Remember, the route list will match whatever is permitted. So everything is permitted except for 1.1.1.0/24. That means that 1.1.1.0/24 is the only thing that will not be matched.
Now when this goes through the route map, it will permit everything it matches. It will match everything except for 1.1.1.0/24. So everything will be permitted and only 1.1.1.0/24 will be blocked.
I hope this has been helpful!
Laz