Hi I think I may have gotten a bad prep exam question as I cannot get it to work in labs and it does not make sense fully to me from how I learned VLANS. I will upload the practice test question from Boson and would like input please.
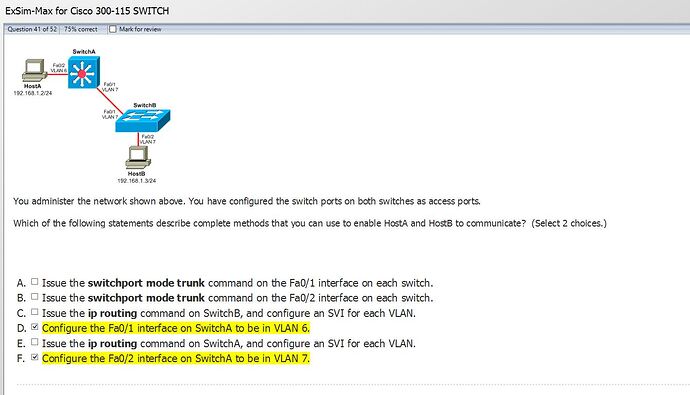
above is what they say is the answer and the topology its very brief. and below is their explanation.
Now I tried this in lab it does work if I make both Fa0/2 and Fa0/1 in the same VLAN 7 for Switch A that logically makes sense to me all the way around. I was able to ping from host A to Host B no problem.
However if I did the other part change Fa0/1 on Switch A to Vlan 6 where both ports on the switch was in VLAN 6 then I could no longer ping from Host A to Host B.
which that makes sense to me as VLANS are suppose to separate traffic that’s the entire point of VLANS to be able to ISOLATE traffic.
However, saying that what they did say about access ports only sending untagged frames, which are frames that do not contain VLAN information. that part sounded kind of logically to me as well but… now I am confused on a basic of switching and not to mention its like 12 midnight and my brain is shutting down and I cannot think very well…ugg anyway when in doubt create a lab and test it and I did and its not working like they say so I was hoping for some explanation like they are incorrect or partially right but basically looking for an answer.
Thanks!
EDITED:::
Ok when I tested this on Cisco VIRL Equipment which for most everything is same as real equipment I was indeed able to ping from VLAN 6 to VLAN 7; where VLAN 6 host had same subnet 192.168.1.2 255.255.255.0 and VLAN 7 host had IP 192.168.1.3 255.255.255.0
I have to admit this has kind of shaken my foundation of thinking as I liked to think of vlan as a pipe that traffic flowed through…
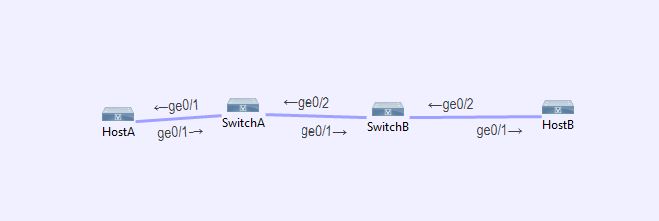
on my VIRL I used 4 switches with two of them acting as hostA and hostB. I setup hostA in VLAN 6 and then assigned the ip to that VLAN6 and for host B I did the same thing but for vlan 7.
Only other odd thing was when I set up the connection between the two switches one side in VLAN 6 and the other side in VLAN 7 I got a native VLAN mismatch error but the traffic still flowed and I was able to ping across VLAN.
Diagram below:
So Boson was correct.
when we use command: switchport access vlan 6
that seems to change the native vlan yet there is also a command to change the native vlan. I guess since a switchport can only have one vlan assigned to it (except in the case of the voice vlan which is special case) that works same on an access port as changing the native vlan.
The command to change the native vlan is not really needed for access port was created so you can change the native vlan on a trunk?
From a security aspect this means VLANs does not really separate traffic or protect it as untagged just goes… this is going to fill so many of my ways of thinking with holes as this was a foundation idea I had in my head.
anyway this shook my world a bit. feel free to post link to any good reading on this or talk about access ports and the communication of untagged traffic over different VLANS!
EDITED:
Ok I Think I am getting my head around some of this. at first this new idea crushed me I mean why have VLANS?? if traffic can go across them there is no security. I was literally stunned and very rattled.
I however then started reading carefully and see this is a very specific circumstance that takes advantage of a granular ingress rule and the lack of a similar egress rule which applies at least to cisco switching in general.
They the following:
-
Traffic received by a switch that arrives on one VLAN will be forwarded only to ports in the same VLAN(unless IP routing is enabled and setup). this is why in my example they say FA0/1 & FA0/2 must be in the same VLAN in order for traffic to pass between them. So right there is a specific requirement.
-
So its basically shoving(in my our example) untagged traffic to FA0/1 because it can receive traffic from the same VLAN according to the rules of the switch (Which it did). Then from there its moving along the port and gets over to Switch B who gets this untagged traffic and does what its suppose to which is move the traffic along.
-
So the rule is kind of an ingress rule now an egress rule so the rule says incoming has to be in the same vlan on the same switch in order for it to send. Makes sense. However, once its sent to another switch that is different. A switch receiving it would think everything is as it should be because its untagged and would just carry on as normal.
-
so basically a native vlan mismatch which is what this was can be dangerous security flaw and that’s why we are informed about it and the importance of it as it would allow traffic from another vlan to move to another switch and do something it normally should not.
-
I don’t know why they don’t have an egress rule that says unless your in the same VLAN you cannot enter… however if you think about it that’s what Trunking is!!! So actually I guess I do know or at least that is how it would seem to be logically.
So I think my world is once again safe but using this special circumstances to break the normal really helped to teach me something and please correct me if I am wrong but I think I have it figured out in my head.