Hello Justin,
I hope you are doing well. To answer your question, the switch knows which interface to forward a packet based on a few things.
First thing to know is by default all ports on a switch start in VLAN 1 this is the “native” vlan by default. As an administrator, you are going to decide what VLAN an interface should participate in.
For example, if we wanted to place an interface in VLAN 7 we would use the following commands:
switch(config#)vlan 7 (tells the switch to create vlan 7)
!
switch(config-vlan)# name VOIP (tells the switch vlan 7 is named VOIP)
!
exit
!
switch(config)# int fa0/7
!
switch(config#) switchport mode access (Tells the switch this port is an access port)
!
switch(config)# switchhport access vlan 7
(tells the switch what vlan the port belongs to)
When the above commands are completed this information is placed in the vlan.dat file located in NVRAM.
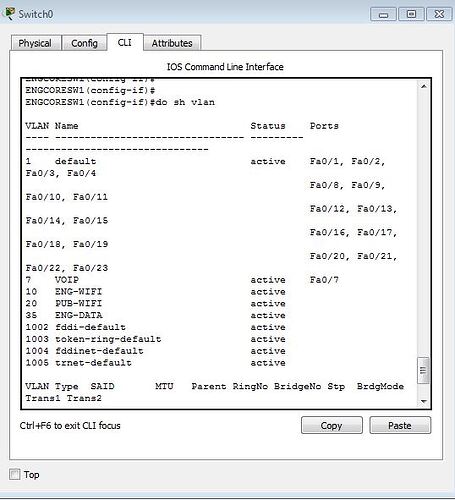
You can see this information when you run “sh vlan”, below you can see a network I have been working on in packet tracer and the results of the “sh vlan” command.
the sh vlan command will show all the access ports and their corresponding vlan. This information is pulled from the vlan.dat file.
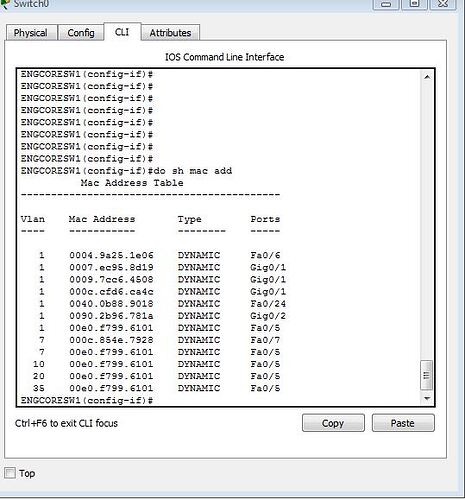
Also in the mac address table you can see what vlan is assigned to a port. I have attached an example of this below.
A trunk is different than an access port, by default a trunk lets all VLANs traverse the interface.
An example config would be
switch(config)# int fa0/24
!
switch(config-if)# switchport mode trunk (turns the interface into a trunk)
!
switch(config-if)# switchport trunk allowed vlan 1,7,10,20,35
(denys all other vlans from traversing trunk)
This info is also added to the vlan.dat you can look at what trunks have been created (if the interface is up/up) by running the command sh int trunk
Now this explains how the switch knows what ports are apart of what VLAN but this does not explain how the switch decides what vlan the traffic is coming from.
An access port does not expect to see tagged traffic
A trunk port expects to see tagged traffic (except for the native vlan)
So, for example, say I have a PC attached to fa0/7 this port is an access port assigned to vlan 7. When my PC sends data it does not know to tag the traffic to identify it as part of vlan 7. When the packet goes into the interface, the switch will then add a 4 byte tag to the frame. Now the switch knows what ports are a part of each vlan and what vlan the traffic belongs to. The exception to this rule is that native vlan is never tagged unless configured to be tagged.
Now say I have a wireless access point that is configured with 3 SSID’s/networks. Each SSID is apart of its own vlan. However, the access point only has one data port. In this case we would use a trunk. The access point can be set to send x tag for x network, So that way when we send traffic over the trunk it will know what vlan the traffic is apart of.
So to recap:
vlans are defined by the admin, this info is put into the vlan.dat file to use
the mac address table also has a list of interfaces and what vlan they are apart of
(as long as traffic has been seen on the ports in question)
the switch or endpoint device will tag the traffic, so that the switch knows what vlan the traffic belongs to and sends it to the proper port. I hope this answers your vlan question!
Thanks,
Scott