This topic is to discuss the following lesson:
thanks for this Rene, easy to understand! PBR with IP SLA is so useful.
Dear Rene,
This is not working for me, please help..
my debug ip policy output is as follows:
*Dec 27 16:07:49.774: IP: s=192.168.12.1 (FastEthernet0/0), d=192.168.34.254, len 28, policy match
*Dec 27 16:07:49.774: IP: route map RM-192, item 10, permit
*Dec 27 16:07:49.778: IP: s=192.168.12.1 (FastEthernet0/0), d=192.168.34.254 (Serial1/0), len 28, policy routed
*Dec 27 16:07:49.782: IP: FastEthernet0/0 to Serial1/0 192.168.24.4
*Dec 27 16:07:49.794: IP: s=192.168.12.1 (FastEthernet0/0), d=192.168.34.254, len 28, policy match
*Dec 27 16:07:49.794: IP: route map RM-192, item 10, permit
*Dec 27 16:07:49.794: IP: s=192.168.12.1 (FastEthernet0/0), d=192.168.34.254 (Serial1/0), len 28, policy routed
*Dec 27 16:07:49.794: IP: FastEthernet0/0 to Serial1/0 192.168.24.4
*Dec 27 16:07:49.818: IP: s=192.168.12.1 (FastEthernet0/0), d=192.168.34.254, len 28, policy match
*Dec 27 16:07:49.818: IP: route map RM-192, item 10, permit
*Dec 27 16:07:49.818: IP: s=192.168.12.1 (FastEthernet0/0), d=192.168.34.254 (Serial1/0), len 28, policy routed
*Dec 27 16:07:49.818: IP: FastEthernet0/0 to Serial1/0 192.168.24.4
*Dec 27 16:07:49.838: IP: s=192.168.12.1 (FastEthernet0/0), d=192.168.34.254, len 28, FIB policy rejected(no match) - normal forwarding
*Dec 27 16:07:49.870: IP: s=192.168.12.1 (FastEthernet0/0), d=192.168.34.254, len 28, FIB policy rejected(no match) - normal forwarding
*Dec 27 16:07:49.926: IP: s=192.168.12.1 (FastEthernet0/0), d=192.168.34.254, len 28, FIB policy rejected(no match) - normal forwarding
*Dec 27 16:07:49.966: IP: s=192.168.12.1 (FastEthernet0/0), d=192.168.34.254, len 28, FIB policy rejected(no match) - normal forwarding
*Dec 27 16:07:50.022: IP: s=192.168.12.1 (FastEthernet0/0), d=192.168.34.254, len 28, FIB policy rejected(no match) - normal forwarding
*Dec 27 16:07:50.074: IP: s=192.168.12.1 (FastEthernet0/0), d=192.168.34.254, len 28, FIB policy rejected(no match) - normal forwarding
My run config
R2#show run
Building configuration...
Current configuration : 1794 bytes
!
! Last configuration change at 16:06:59 UTC Sun Dec 27 2015
!
version 15.2
service timestamps debug datetime msec
service timestamps log datetime msec
!
hostname R2
!
boot-start-marker
boot-end-marker
!
!
!
no aaa new-model
no ip icmp rate-limit unreachable
ip cef
!
!
!
!
!
!
no ip domain lookup
no ipv6 cef
!
!
multilink bundle-name authenticated
!
!
!
!
!
!
!
!
!
ip tcp synwait-time 5
!
track 1 ip sla 1 reachability
!
!
!
!
!
!
!
!
!
!
!
!
interface FastEthernet0/0
ip address 192.168.12.2 255.255.255.0
ip policy route-map RM-192
speed auto
duplex auto
!
interface FastEthernet0/1
ip address 192.168.23.2 255.255.255.0
speed auto
duplex auto
!
interface Serial1/0
ip address 192.168.24.2 255.255.255.0
serial restart-delay 0
!
interface Serial1/1
no ip address
shutdown
serial restart-delay 0
!
interface Serial1/2
no ip address
shutdown
serial restart-delay 0
!
interface Serial1/3
no ip address
shutdown
serial restart-delay 0
!
!
router eigrp 100
network 192.168.12.0
network 192.168.23.0
network 192.168.24.0
redistribute static metric 2048 2000 255 1 1500
passive-interface FastEthernet0/0
!
ip forward-protocol nd
!
!
no ip http server
no ip http secure-server
ip route 1.1.1.0 255.255.255.0 FastEthernet0/0
!
ip access-list extended ACL-192
permit ip 192.168.12.0 0.0.0.255 host 192.168.34.254 log
!
ip sla 1
icmp-echo 192.168.34.254
threshold 500
timeout 500
frequency 1
ip sla schedule 1 life forever start-time now
!
route-map RM-192 permit 10
match ip address ACL-192
set ip next-hop verify-availability 192.168.24.4 1 track 1
!
!
!
control-plane
!
!
line con 0
exec-timeout 0 0
privilege level 15
logging synchronous
stopbits 1
line aux 0
exec-timeout 0 0
privilege level 15
logging synchronous
stopbits 1
line vty 0 4
login
!
!
end
 
My routing table.
 
R2#show ip route
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route, H - NHRP, l - LISP
+ - replicated route, % - next hop override
Gateway of last resort is not set
1.0.0.0/24 is subnetted, 1 subnets
S 1.1.1.0 is directly connected, FastEthernet0/0
192.168.12.0/24 is variably subnetted, 2 subnets, 2 masks
C 192.168.12.0/24 is directly connected, FastEthernet0/0
L 192.168.12.2/32 is directly connected, FastEthernet0/0
192.168.23.0/24 is variably subnetted, 2 subnets, 2 masks
C 192.168.23.0/24 is directly connected, FastEthernet0/1
L 192.168.23.2/32 is directly connected, FastEthernet0/1
192.168.24.0/24 is variably subnetted, 2 subnets, 2 masks
C 192.168.24.0/24 is directly connected, Serial1/0
L 192.168.24.2/32 is directly connected, Serial1/0
D 192.168.34.0/24 [90/30720] via 192.168.23.3, 00:23:37, FastEthernet0/1
My stats
R2#show ip sla statistics
IPSLAs Latest Operation Statistics
IPSLA operation id: 1
Latest RTT: 24 milliseconds
Latest operation start time: 16:10:18 UTC Sun Dec 27 2015
Latest operation return code: OK
Number of successes: 2030
Number of failures: 0
Operation time to live: Forever
R2#show tr
R2#show track 1
Track 1
IP SLA 1 reachability
Reachability is Up
1 change, last change 21:33:29
Latest operation return code: OK
Latest RTT (millisecs) 24
Tracked by:
ROUTE-MAP 0
R2#show access
R2#show access-li
R2#show access-lists
Extended IP access list ACL-192
10 permit ip 192.168.12.0 0.0.0.255 host 192.168.34.254 log (131 matches)
Hmm the first few packets did get policy routed:
*Dec 27 16:07:49.774: IP: s=192.168.12.1 (FastEthernet0/0), d=192.168.34.254, len 28, policy match
*Dec 27 16:07:49.774: IP: route map RM-192, item 10, permit
*Dec 27 16:07:49.778: IP: s=192.168.12.1 (FastEthernet0/0), d=192.168.34.254 (Serial1/0), len 28, policy routed
Did anything change in between those pings?
Nothing. Its not forwarding through serial port. Any hint. I’ll make the topology again in gns3 and check again to see whats happening.. thanks for the reply
Hi Rene,
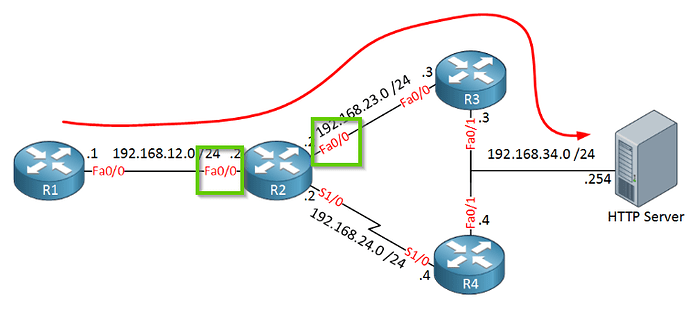
As your diagram but i change from SERVER to Internet. Do i need default route or not ?
Best Regards,
CH
Hi CH,
Your routers will need to know where to forward traffic to. If you have an internet connection behind R3/R4 then you’ll need a default route yes.
Rene
Hello, I did not get the pbr with ip sla I attached the tests and my configuration
R2#show run in
R2#show run interface f
R2#show run interface fastEthernet 0/0
Building configuration...
Current configuration : 122 bytes
!
interface FastEthernet0/0
ip address 192.168.23.2 255.255.255.0
ip policy route-map PBR
duplex auto
speed auto
end
-
R2#show rou
R2#show route-map PBR
route-map PBR, permit, sequence 10
Match clauses:
ip address (access-lists): HTTP_SERVER
Set clauses:
ip next-hop verify-availability 192.168.24.4 1 track 1 [up]
Policy routing matches: 0 packets, 0 bytes
R2#SH IP ACCE
R2#SH IP ACCEss-lists
Extended IP access list HTTP_SERVER
10 permit ip any host 192.168.34.254
R2#
R2#SHOW RUN
Building configuration...
Current configuration : 1474 bytes
!
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname R2
!
boot-start-marker
boot-end-marker
!
!
no aaa new-model
memory-size iomem 5
no ip icmp rate-limit unreachable
ip cef
!
!
!
!
no ip domain lookup
ip auth-proxy max-nodata-conns 3
ip admission max-nodata-conns 3
ip sla monitor 1
type echo protocol ipIcmpEcho 192.168.24.4
frequency 10
ip sla monitor schedule 1 life forever start-time now
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
ip tcp synwait-time 5
!
track 1 rtr 1
!
!
!
!
!
interface FastEthernet0/0
ip address 192.168.23.2 255.255.255.0
ip policy route-map PBR
duplex auto
speed auto
!
interface FastEthernet0/1
ip address 192.168.12.2 255.255.255.0
duplex auto
speed auto
!
interface FastEthernet1/0
ip address 192.168.24.2 255.255.255.0
ip ospf cost 1000
duplex auto
speed auto
!
router ospf 1
router-id 2.2.2.2
log-adjacency-changes
network 0.0.0.0 255.255.255.255 area 0
!
ip forward-protocol nd
!
!
no ip http server
no ip http secure-server
!
ip access-list extended HTTP_SERVER
permit ip any host 192.168.34.254
!
no cdp log mismatch duplex
!
route-map PBR permit 10
match ip address HTTP_SERVER
set ip next-hop verify-availability 192.168.24.4 1 track 1
!
!
!
control-plane
!
!
!
!
!
!
!
!
!
!
line con 0
exec-timeout 0 0
privilege level 15
logging synchronous
line aux 0
exec-timeout 0 0
privilege level 15
logging synchronous
line vty 0 4
login
!
!
end
-
R2#
R2#
R2#show run
Building configuration...
Current configuration : 1474 bytes
!
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname R2
!
boot-start-marker
boot-end-marker
!
!
no aaa new-model
memory-size iomem 5
no ip icmp rate-limit unreachable
ip cef
!
!
!
!
no ip domain lookup
ip auth-proxy max-nodata-conns 3
ip admission max-nodata-conns 3
ip sla monitor 1
type echo protocol ipIcmpEcho 192.168.24.4
frequency 10
ip sla monitor schedule 1 life forever start-time now
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
ip tcp synwait-time 5
!
track 1 rtr 1
!
!
!
!
!
interface FastEthernet0/0
ip address 192.168.23.2 255.255.255.0
ip policy route-map PBR
duplex auto
speed auto
!
interface FastEthernet0/1
ip address 192.168.12.2 255.255.255.0
duplex auto
speed auto
!
interface FastEthernet1/0
ip address 192.168.24.2 255.255.255.0
ip ospf cost 1000
duplex auto
speed auto
!
router ospf 1
router-id 2.2.2.2
log-adjacency-changes
network 0.0.0.0 255.255.255.255 area 0
!
ip forward-protocol nd
!
!
no ip http server
no ip http secure-server
!
ip access-list extended HTTP_SERVER
permit ip any host 192.168.34.254
!
no cdp log mismatch duplex
!
route-map PBR permit 10
match ip address HTTP_SERVER
set ip next-hop verify-availability 192.168.24.4 1 track 1
!
!
!
control-plane
!
!
!
!
!
!
!
!
!
!
line con 0
exec-timeout 0 0
privilege level 15
logging synchronous
line aux 0
exec-timeout 0 0
privilege level 15
logging synchronous
line vty 0 4
login
!
!
end
R2#
please helpme
regards
jesus
R1#traceroute 192.168.34.254
Type escape sequence to abort.
Tracing the route to 192.168.34.254
1 192.168.12.2 40 msec 48 msec 48 msec
2 192.168.23.3 68 msec 68 msec 72 msec
3 192.168.34.254 92 msec 72 msec 92 msec
R1#
*Mar 1 00:51:25.131: IP: s=192.168.23.3 (FastEthernet0/0), d=192.168.12.1, len 56, FIB policy rejected(no match) - normal forwarding
*Mar 1 00:51:25.255: IP: s=192.168.23.3 (FastEthernet0/0), d=192.168.12.1, len 56, FIB policy rejected(no match) - normal forwarding
*Mar 1 00:51:25.371: IP: s=192.168.23.3 (FastEthernet0/0), d=192.168.12.1, len 56, FIB policy rejected(no match) - normal forwarding
*Mar 1 00:51:25.547: IP: s=192.168.34.254 (FastEthernet0/0), d=192.168.12.1, len 56, FIB policy rejected(no match) - normal forwarding
*Mar 1 00:51:25.699: IP: s=192.168.34.254 (FastEthernet0/0), d=192.168.12.1, len 56, FIB policy rejected(no match) - normal forwarding
R2#
*Mar 1 00:51:25.867: IP: s=192.168.34.254 (FastEthernet0/0), d=192.168.12.1, len 56, FIB policy rejected(no match) - normal forwarding
You attached the route-map to the interface that connects R2 to R3, it should be on the F0/1 interface that connects to R1.
Hello,
What’s the difference between Track x IP SLA x reachability vs state command?
Hello sales2161
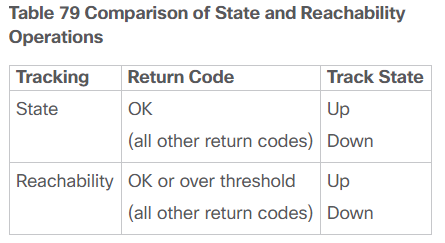
According tothis Cisco documentation, the difference is that the state and reachability options have to do with the OverThreshold return code. As stated in the documentation:
Two aspects of an IP SLAs operation can be tracked: state and reachability. The difference between these aspects relates to the acceptance of the OverThreshold return code. Table 79 shows the state and reachability aspects of IP SLAs operations that can be tracked.
Now what does this all mean? Well, practically speaking, when you configure a threshold, the reachability option only takes into account if you can reach the destination IP address with the Echo IP SLA operation. The state option also takes into account the Round Trip Time (RTT) of the Echo IP SLA operation.
I hope this has been helpful!
Laz
Thanks for replying.
So basically, reachability means if your ICMP request can get to the destination and State means if you can successfully send a request and receive a reply as well? I will try to lab it out soon
Hello sales2161
Well, almost. Reachability checks to see if you get an ICMP reply successfully. State checks to see if you get an ICMP reply successfully with a round trip time that is less than the configured threshold.
I hope this has been helpful.
Laz
Hello Rene.
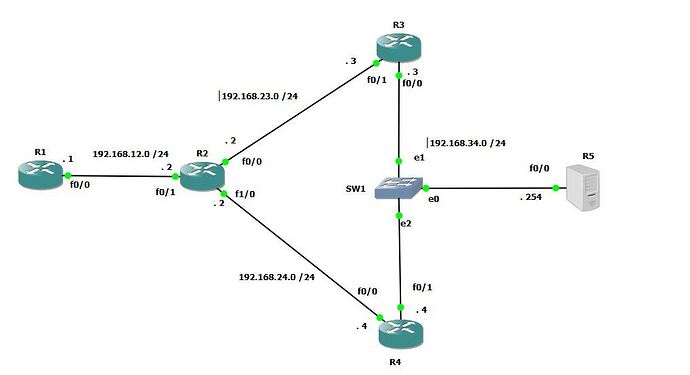
I’ve found a printing error on the topology: the same number of different interfaces on R2.
P.S.: Thanks a lot for clear explanation!
Thank you Boris, just fixed the diagram.
Rene
I study this lesson as one of my Anki flashcards (for the past couple of years!) and something came to me the other day.
Actually, the track object shouldn’t be needed as the IP 192.168.24.4 is tied to a direct physical interface between R2 & R4.
If that IP went down, then the s1/0 interface would also go down on R2, so it would no longer be able to arp for 192.168.24.4. Therefore, it should by default ignore the PBR route-map entry and use the GRT. The PBR entry is only valid if there is a valid arp entry for the next-hop IP? The arp entry should be removed immediately if that interface went down.
I guess if somehow the IP became unavailable, such as changing it to .5 on R4 (but the physical interface s1/0 remained UP on R2) then the arp entry would still be valid, so the traffic would be black holed.
Hello Chris
For this particular topology, yes you are right, you wouldn’t have to track the reachability, but you would only need to set the next hop to the IP of R4. If the interface was down, there would be no valid alternative to going via Fa0/1.
However, keep in mind that this is a special case. What if you had a larger network, and the reachability wasn’t checking the next hop, but a few hops downstream? Then if that reachability failed, it wouldn’t necessarily bring the interface down, so you would need to keep the object tracking. Or, in the event that the IP changes, as you stated in your post as well, that would also be a case where tracking would be necessary (although it would be an unusual case!)
I hope this has been helpful!
Laz
I think in this example it would be better to track 192.168.34.4 (R4 f0/1) which could blackhole traffic if it went down.