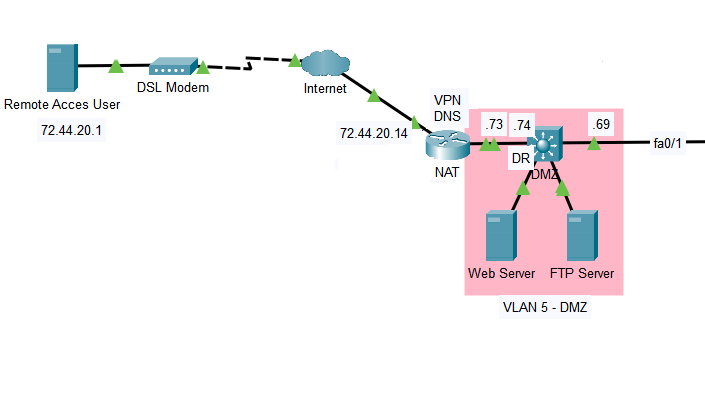
Hi, I have an accessabilty issue with a remote access VPN connection.
The remote access user can http and ftp to the Web server & FTP server, but when the remote access user connects to the VPN on the router at 72.44.20.14,
it cannot access the Web server or FTP Server. It can ping 192.168.100.73, but not .74. The Web Server IP address is 192.168.5.5 /29
I am not sure if I have to configure an access list to allow HTTP, FTP, & SSH traffic through the VPN, or if there is something else thats needs to be configured.
This is the config I have:
VPN / NAT ROUTER
int fa0/0
ip address 192.168.100.13 255.255.255.252
exit
!
int fa0/1
ip address 192.168.100.70 255.255.255.252
exit
!
int fa1/0
ip address 192.168.100.5 255.255.255.252
exit
!
int fa1/1
ip address 192.168.100.1 255.255.255.252
exit
!
int lo1
description REMOTE ACCESS TO R1
ip address 1.1.1.1 255.255.255.255
exit
!
!
aaa new-model
aaa authentication login REMOTE local
aaa authorization network REMOTE local
!
username xxxx secret xxxx
!
crypto isakmp policy 10
encryption aes 256
hash md5
authentication pre-share
group 2
lifetime 21600
exit
!
crypto isakmp client configuration group REMOTE
key CISCO
pool VPN-POOL
!
ip local pool VPN-POOL 192.168.5.1 192.168.5.10
!
crypto ipsec transform-set VPN-SET esp-aes 256 esp-md5-hmac
!
crypto dynamic-map VPN-MAP 10
set transform-set VPN-SET
reverse-route
exit
!
crypto map CLIENT-MAP client authentication list REMOTE
crypto map CLIENT-MAP isakmp authorization list REMOTE
crypto map CLIENT-MAP client configuration address respond
crypto map CLIENT-MAP 10 ipsec-isakmp dynamic VPN-MAP
!
int fa0/0
crypto map CLIENT-MAP
!
ip route 0.0.0.0 0.0.0.0 FastEthernet0/0
!
router ospf 1
router-id 100.1.1.1
network 1.1.1.1 0.0.0.0 area 0
network 192.168.100.1 0.0.0.0 area 0
network 192.168.100.5 0.0.0.0 area 0
network 192.168.100.13 0.0.0.0 area 0
network 192.168.100.70 0.0.0.0 area 0
!
auto-cost reference-bandwidth 100
!
ip nat inside source list NAT-TRANSLATIONS interface FastEthernet0/0 overload
!
ip nat inside source static tcp 192.168.5.5 80 72.44.20.14 80
ip nat inside source static tcp 192.168.5.5 443 72.44.20.14 443
ip nat inside source static tcp 192.168.5.5 80 72.44.30.14 80
ip nat inside source static tcp 192.168.5.5 443 72.44.30.14 443
ip nat inside source static tcp 192.168.5.6 20 72.44.20.14 20
ip nat inside source static tcp 192.168.5.6 21 72.44.20.14 21
DMZ Switch
ip routing
!
vlan 200
name SSH-TO-DMZ-VPN-NAT-SWITCH
!
interface Vlan200
ip address 192.168.200.41 255.255.255.248
!
vlan 5
name DMZ_VLAN
!
int vlan 5
ip address 192.168.5.1 255.255.255.248
!
int range fa0/5 - 6
switchport mode access
switchport access vlan 5
!
int fa0/1
no switchport
ip address 192.168.100.69 255.255.255.252
!
int fa0/24
no switchport
ip address 192.168.100.74 255.255.255.252
!
int lo1
description REMOTE-ACCESS-TO-L3-DMZ-SW
ip address 66.66.66.66 255.255.255.255
exit
!
ip route 0.0.0.0 0.0.0.0 192.168.100.73
!
router ospf 1
router-id 200.6.6.6
network 66.66.66.66 0.0.0.0 area 0
network 192.168.200.41 0.0.0.0 area 0
network 192.168.5.0 0.0.0.255 area 0
network 192.168.100.69 0.0.0.0 area 0
network 192.168.100.74 0.0.0.0 area 0