This topic is to discuss the following lesson:
This is a GREAT walkthrough , however I see in the url that it sits in “uncatagorized”, do you have a quick way to browse to this location to locate this walkthrough? I only happened across it via a link in another comment.
Hello Edgar
Thanks for pointing that out, I’ll give a shout out to Rene to see if it can be located somewhere more accessible.
Thanks again!
Laz
Hi Rene and staff,
i was doing a basic lab ipv6 with GNS3 and SSH came in front of the scene (no matter ipv4 or ipv6 in this post)
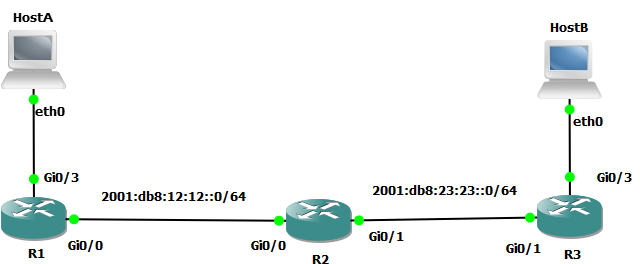
This is the lab
and opening SSH session from HostA to R1 led me to review crypto keys with cisco (just to remind)
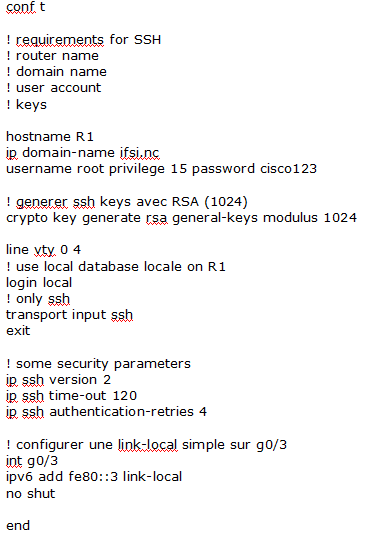
R1 configuration is
Host A is toolbox
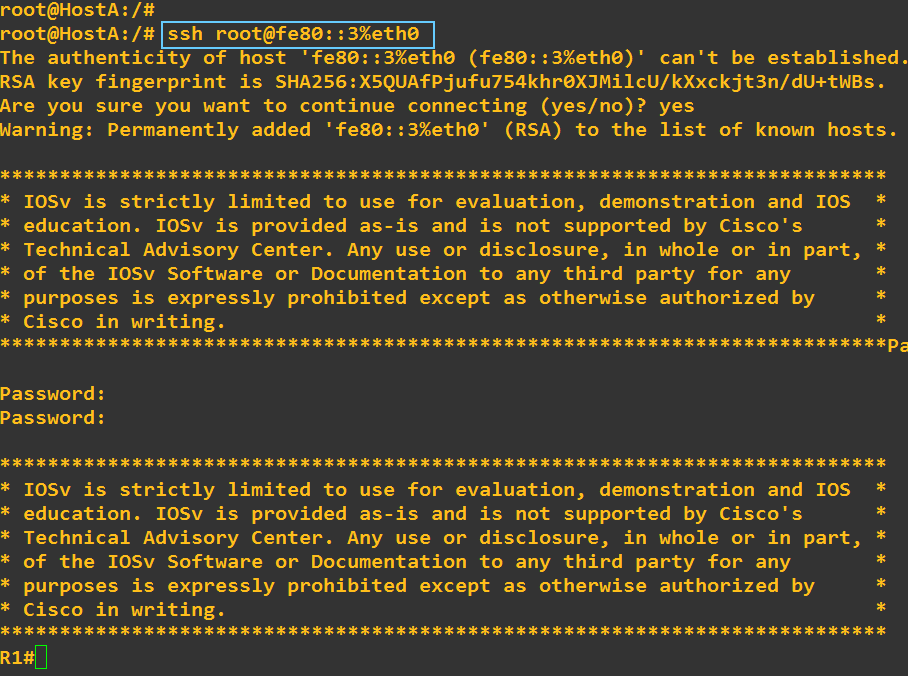
I opened the ssh session
Sorry, i failed the password twice
And exit the session
At this step, my question is about to find the public key of R1 in hostA
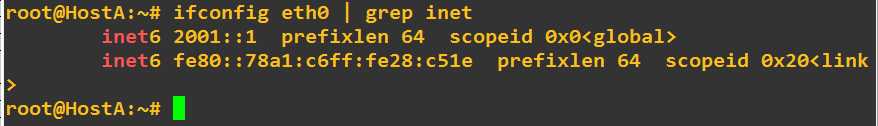
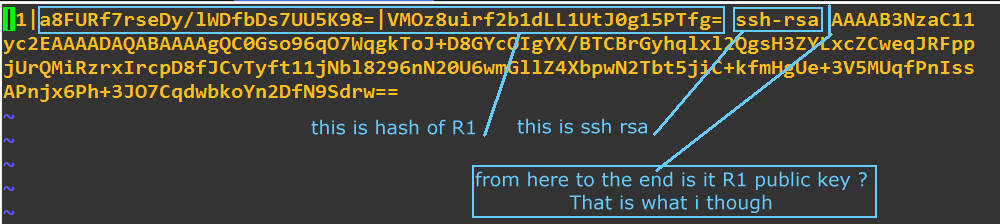
Going to hostA here is what i found
(vi /root/.ssh/known_hosts)
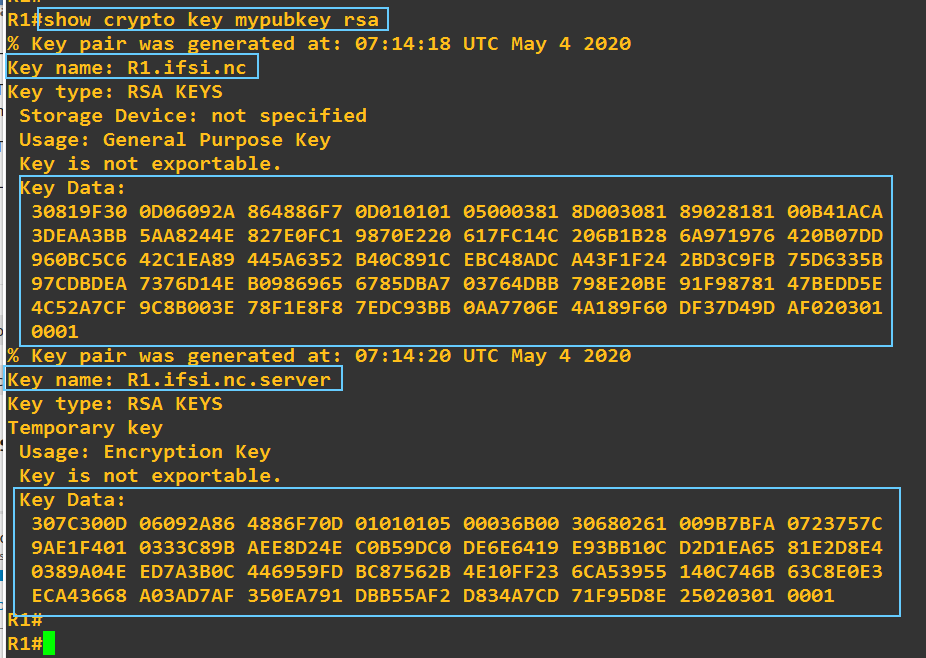
Going to R1 here is what i found
Key data on R1 seems not to match with the content of the file known_hosts in the client hostA: that is what i want to understand
If i am in a wrong way please tell me so i could understand
Regards
Hello Dominique
The key data in the router and that found within the known_hosts file do appear different, and this is simply because of the method of encoding. Within the router, the key data is displayed in Hexadecimal while in the known_hosts file, in what is known as Base64 encoding which represents binary data in ASCII (and this is why you see all the letters of the alphabet as well as many symbols). This Ubuntu man page includes a description of the format of the known_hosts file format.
I hope this has been helpful!
Laz
Hi!
This is a great walkthrough but I have an older 3560 in my lab and the ip ssh pubkey-chain command doesn’t exist. Is there a different method to accomplish this on older switches? Here’s the image it’s running:
c3560-ipservicesk9-mz.122-55.SE9.bin
Second question: How can we setup authorization so that successfully authenticating with radius puts you in priv exec mode?
Hello Aaron
If you take a look at this Cisco command line reference, you’ll see that this command was introduced in version IOS 15.0
It seems that the 3560 platform doesn’t support public key authentication for SSH. The following documentation however describes how to secure SSH communication:
Yes, it is possible. Take a look at this Cisco documentation:
I hope this has been helpful!
Laz
Hi,
As far as i understand, in the procedure a local username is used (WINDOWS_USER) and added to the configuration of the IOS device
R1#show running-config | begin pubkey
ip ssh pubkey-chain
username WINDOWS_USER
key-hash ssh-rsa 8FB4F858DD7E5AFB372780EC653DB371
quit
But this is still a local username which has to be added to the switch/router/ASA… . Is it possible to use ssh keys while authenticating with a Tacacs+ username ?
Thanks a lot,
Olli
Hello Oliver
It seems that SSH Public Key Authentication is only available for local username authentication. This can be seen in the following Cisco documentation:
https://www.cisco.com/c/en/us/td/docs/routers/crs/software/crs_r4-2/security/configuration/guide/b_syssec_cg42crs/b_syssec_cg42crs_chapter_01001.html#con_1095059
As I don’t have personal experience with SSH Public Key Authentication in combination with an AAA system, doing a bit of research online, there seems to be the consensus in general on other sites focusing on RADIUS and TACACs that this is not possible. Although it is not stated clearly anywhere official, the general experience of users seems to indicate that it is not possible.
I hope this has been helpful!
Laz
So I’ve been experimenting with FreeRadius and have a radius working with a “Cleartext-Password” (still researching what other versions I can use) however if I create a public key for myself on the router, it will begin logging me in, show me the motd, then disconnect me. I’d like my ssh public key in free radius and not on the router (to begin with) and of course would like the login to complete.
Still trying to debug why it boots me after doing the pubkey handshake.
! note that my radius server is on the VRF-lite “relay_admin” network
aaa group server radius RADIUS_SERVERS
server name RADIUS1_IPv4
ip vrf forwarding relay_admin
ip radius source-interface Loopback102
load-balance method least-outstanding ignore-preferred-server
!
aaa authentication login default group RADIUS_SERVERS local
aaa authorization exec default group RADIUS_SERVERS if-authenticated
aaa accounting exec default start-stop group RADIUS_SERVERS
!
radius server RADIUS1_IPv4
address ipv4 172.16.1.10 auth-port 1812 acct-port 1813
key SECRET_KEY
!
ip ssh pubkey-chain
username my-test-acct
key-hash ssh-rsa E40E01E464A9C15EEE76DDB7A10C5B8E my-test-key
Radius server has radcheck table entry:
null,"my-test-acct","Cleartest-Password",":=","my-test-password"
Radius server has radreply table entries:
null,'my-test-acct','Service-Type','+=','NAS-Prompt-User'
null,'my-test-acct','cisco-avpair','+=','shell:priv-lvl=15'
Don’t know where to put the ssh key or if there is a table entry for it in the radcheck?
Marcos
Hello Marcos
If you look at some of the above posts you’ll find that an ssh public key on a non-local AAA system such as free radius is not supported ![]() .
.
Looking through some of the posts and links above may help you in further understanding this approach. If you have any further questions, just let us know!
I hope this has been helpful!
Laz
Hi rene and staff,
there is so much stuff to do, i am going between forward and back between CCIE lessons to test as much things as i can
I come back to this lesson just to ask a question about thing that is surprising me
in ubuntu (18.04), the user dom generates its rsa keys pair: id_rsa the private key and id_rsa.pub the public key
I found no problem to work with these keys, for example to authenticate the user “dom” with its ssh keys to ssh a router (IOS or ASA)
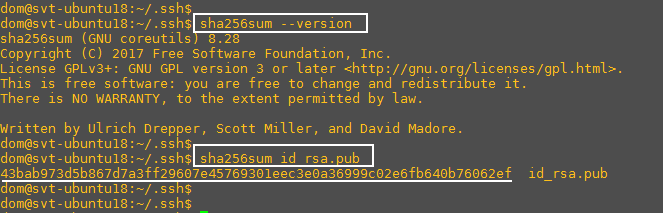
But I got the idea to test more ubuntu commands like
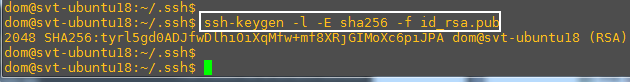
(-E sha256 is default)
This command output says that the private key is 2048 length and the hash with sha256 is
tyrl5gd0ADJfwDlhiOiXqMfw+mf8XRjGIMoXc6piJPA
Is not it ?
Then i try to verify the hash with the command sha256sum
For the hash this command gives the output below
43bab973d5b867d7a3ff29607e45769301eec3e0a36999c02e6fb640b76062ef
the 2 hashes dont match inside the same ubuntu version
I dont understand why: i do some google search but i dont find any response
Could you give me help ?
Regards
Hello Dominique
Looking over some of the commands myself, I have found the following:
The ssh-keygen command used to generate what it calls an RSA key fingerprint. This fingerprint for this particular command seems to be 43 characters long. The output for the sha256sum command is always 64 characters long. So there are two things I have in mind here:
- The first has to do with what the actual
sha256sumcommand does. It generates a hash based on thersa.pubfile. This command is used to ensure file integrity, so it may be taking some additional information as input to the hash beyond just the contents of the file, such as the file name itself or some attributes. As a result, the hash will be different. - The second has to do with the fundamental difference between the output hashes. The
ssh-keygencommand, from what I’ve seen in examples online, will always generate a 43 character hash, that is, 344 bits. Unlike the output of thesha256sumcommand which gives us 64 characters, or a 512-bit hash. It could be that thessh-keygencommand generates what is known as a truncated hash and not the full hash result expected.
So based on these two things, I think that the two things you are actually comparing are apples ad oranges. That is, they are two different things that are not expected to be the same. I hope this gives some insight into the results you see.
I hope this has been helpful!
Laz
Hi,
I have a strange issue with ssh and hoping someone might have an idea of what the issue could be.
I recently configured a couple of brand new cisco 9300 switches and set them up for SSH access.
However I cannot SSH to them from a client PC or any pc or server on the same network/subnet even thou I can ssh into all other switches from any pc or server on that network.
I can however successfully connect to them from other switches on the same network/subnet from the cisco cli using ssh - l [username] [switch ip]
I know its not my config as its fairly basic stuff to set this up and I’ve configured thousands of switches for this over the years.
Its not the firewall as I’ve checked there and nothing blocking them either and nothing allowing the ones I can ssh to.
I’m at a total loss as to why the only way I can access these switches is by using ssh from another switch on the same network/subnet.
So just to clarify if I plug a pc into this subnet I can ssh to all other switches on it but I can’t ssh to these new switches directly, the only way I can ssh to them is by ssh into a switch on the same subnet and then ssh from the cli of that switch into the new switches.
Hello Sean
There may be a number of things going on in this scenaro. The first thing to notice is that you are using two different SSH clients, one on the PC, and one on another switch. The switch’s client can successfully connect, while the PC’s cannot. From my understanding, this is the case for all 9300 switches you have, and is not the case for other Cisco IOS switches, correct?
So there is some config on the PC’s SSH client that is not being accepted by the 9300 switches. And it’s probably something new compared to configs made on the older IOS switches.
I was looking at some of the documentation for SSH for the catalyst 9300 switches and noticed the following:
The SSH server and the SSH client are supported only on Data Encryption Standard (DES) (56-bit) and 3DES(168-bit) data encryption software. In DES software images, DES is the only encryption algorithm available. In 3DES software images, both DES and 3DES encryption algorithms are available.
Now I’m not saying that this is the issue, but I am saying that there are particular restrictions and configurations that are required depending upon the software image you are using, and it could be one of these that is causing the problem.
When you attempt to SSH into the device, what error message do you see? That will give you a clue as to why the connection is failing. Secondly, you can use the debug ip ssh command to see what connection requests are being made to the device, and why the connection is failing.
If you’re using Putty on your PC, you can also enable logging there by going to Logging and selecting SSH Packets before connecting.
Looking at these should put you in a position to make some better determinations as to why your ssh sessions are failing. Let us know your results so that we can help you further in your troubleshooting process.
I hope this has been helpful!
Laz
Thanks Laz,
The issue only effects some 9300’s and others not.
They all came in the same batch so its very strange.
I will take another look and see what the error was as I cant remember off top of my head.
I will try the “debug ip ssh” command as you suggested and see what it throws back when I try to connect. Thanks Laz.