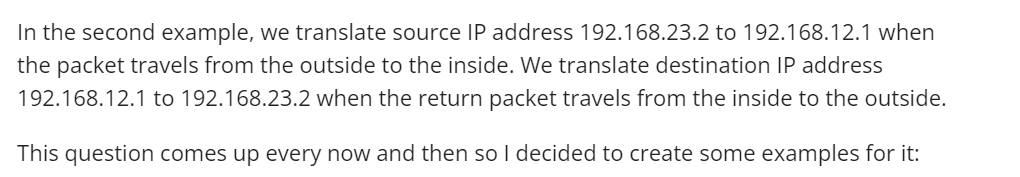
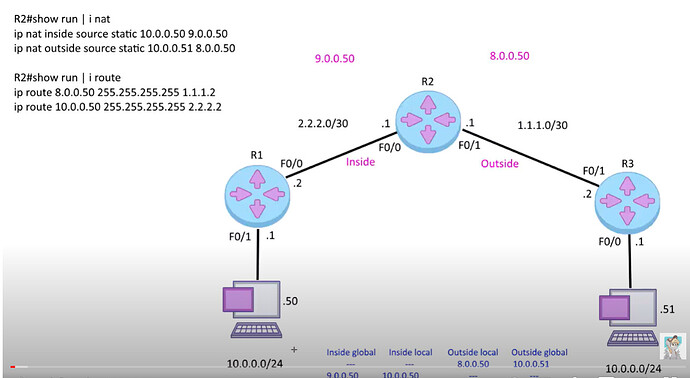
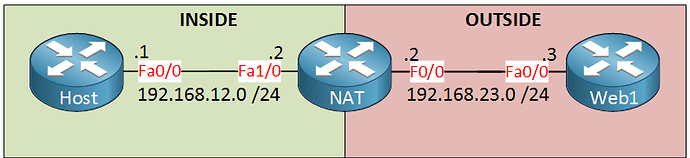
I saw the lesson (pretty good, BTW), but I would like to share some additional troubleshoot commands that may facilitate people in this forum to get a better understanding.
Forwarding/NAT debug
Cisco by default offloads packet switching to the interface hardware always when possible (fast switching). So, if you run debug ip packet on the NAT router, you’ll not see anything because the debug occurs on the processor (CPU), not on the interface hardware. So, let’s disable fast switching on the proper interfaces:
NAT(config-if)#no ip route-cache
And enable debug:
NAT#debug ip packet
Not, let’s run a single ping (only 1, so output will be easier to read):
HOST#ping 192.168.23.3 repeat 1
In the NAT router, we’ll see:
*Jun 19 01:15:49.670: IP: s=192.168.12.1 (Ethernet0/0), d=192.168.23.3, len 100, input feature, Common Flow Table(5), rtype 0, forus FALSE, sendself FALSE, mtu 0, fwdchk FALSE
[...]
*Jun 19 01:15:49.670: IP: s=192.168.23.2 (Ethernet0/0), d=192.168.23.3 (Ethernet0/1), len 100, output feature, Post-routing NAT Outside(26), rtype 1, forus FALSE, sendself FALSE, mtu 0, fwdchk FALSE
[...]
*Jun 19 01:15:49.670: IP: s=192.168.23.2 (Ethernet0/0), d=192.168.23.3 (Ethernet0/1), g=192.168.23.3, len 100, forward
*Jun 19 01:15:49.670: IP: s=192.168.23.2 (Ethernet0/0), d=192.168.23.3 (Ethernet0/1), len 100, sending full packet
*Jun 19 01:15:49.671: IP: s=192.168.23.3 (Ethernet0/1), d=192.168.23.2, len 100, input feature, Common Flow Table(5), rtype 0, forus FALSE, sendself FALSE, mtu 0, fwdchk FALSE
[...]
*Jun 19 01:15:49.671: IP: s=192.168.23.3 (Ethernet0/1), d=192.168.12.1, len 100, input feature, NAT Outside(91), rtype 0, forus FALSE, sendself FALSE, mtu 0, fwdchk FALSE
[...]
*Jun 19 01:15:49.671: IP: s=192.168.23.3 (Ethernet0/1), d=192.168.12.1 (Ethernet0/0), g=192.168.12.1
NAT#, len 100, forward
*Jun 19 01:15:49.671: IP: s=192.168.23.3 (Ethernet0/1), d=192.168.12.1 (Ethernet0/0), len 100, sending full packet
We can see the packet being received on Ethernet0/0 (in my particular case, equivalent to fastEthernet0/1 in the lesson) w/ source 192.168.12.1, being translated to 192.168.23.2 (phase output feature, Post-routing NAT Outside), and being forwarded to Ethernet0/1 (in my particular case, equivalent to fastEthernet0/0 in the lesson). Also, we see the packet being received in Ethernet0/1 w/ destination 192.168.23.2, the NAT being undone (destination changed back to 192.168.12.1 at phase input feature, NAT Outside), and then forwarded to Ethernet0/0.
Tips and tricks regarding debugging routing
You should be careful when doing such kind of debug in a real-world router, as (1) we’re disabling fast-switching and (2) we’re debugging all packets. This may result in big performance degradation.
I found some useful tips and tricks about how to properly debug in the following link: https://www.cisco.com/c/en/us/support/docs/dial-access/integrated-services-digital-networks-isdn-channel-associated-signaling-cas/10374-debug.html